Introduction
This is Part 2 of a new series of guides which will cover managing Windows 365 Cloud PC’s using PowerShell and Microsoft Graph. This mini series should help you get started with automating and managing your Cloud PC’s using PowerShell via Microsoft Graph. If you are new to Windows 365 Cloud PC’s then please read our previous series called Getting started with Windows 365 available here. At the time of writing, Paul is a 7 times Enterprise Mobility MVP based in the UK and Niall is a 13 times Enterprise Mobility & Windows and Devices MVP based in Sweden.
Below you can find all parts in this series:
- Automating Windows 365 part 1 – Introducing Graph and setting up Visual Studio code
- Automating Windows 365 part 2 – Using Graph X-Ray <- you are here
- Automating Windows 365 part 3 – Provisioning Cloud PC’s
- Automating Windows 365 part 4 – Managing your Cloud PC
- Automating Windows 365 part 5 – Cloud PC reports
In this part we’ll cover the following:
- Introducing Graph X-Ray
- Installing Graph X-Ray
- Using the extension
- Running code produced by Graph X-Ray
- Related reading
- Summary
Introducing Graph X-Ray
Graph X-Ray is a web browser extension created by a bunch of very smart people at Microsoft including Merill Fernando (Senior Product Manager). It was designed as part of a hackathon project to work with various web-browsers including Google Chrome and Microsoft Edge running on Windows or MacOS. The extension gives you a sneak peek at the API calls that Graph is making when you do various actions in any app or console that uses Graph API.
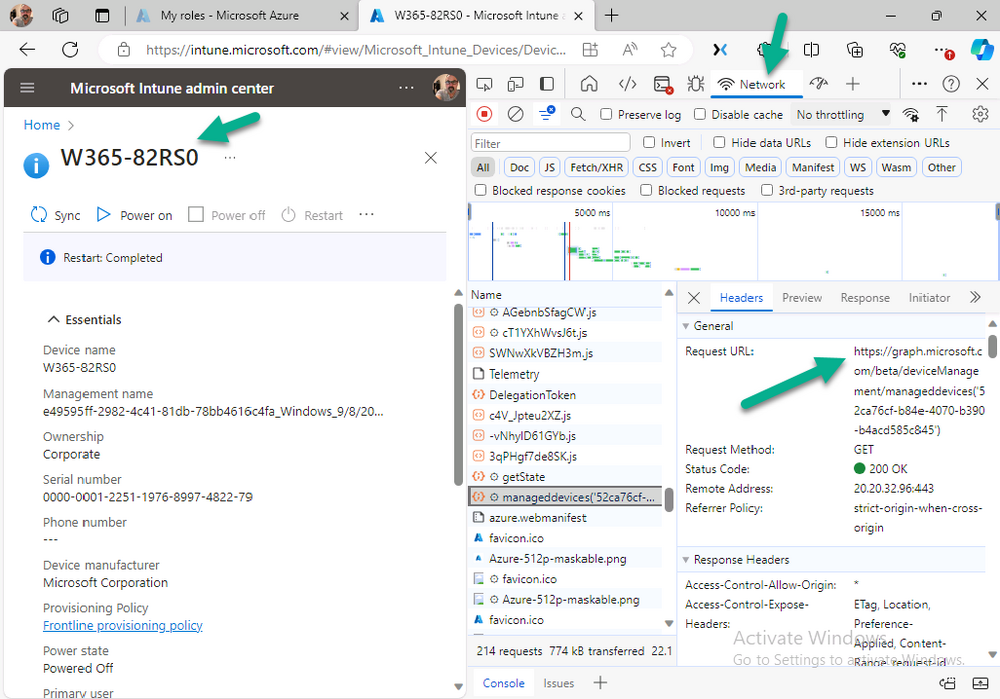
Graph X-Ray does more than the built in Network developer tools included with these web-browsers, for example, it simplifies some of the calls as well as giving you the commands in other programming languages. Below is a sample of data from Network developer tools output when viewing the details of a Windows 365 Cloud PC in Intune. Without filtering, you have to really dig through masses of data to find the Graph calls in the output.
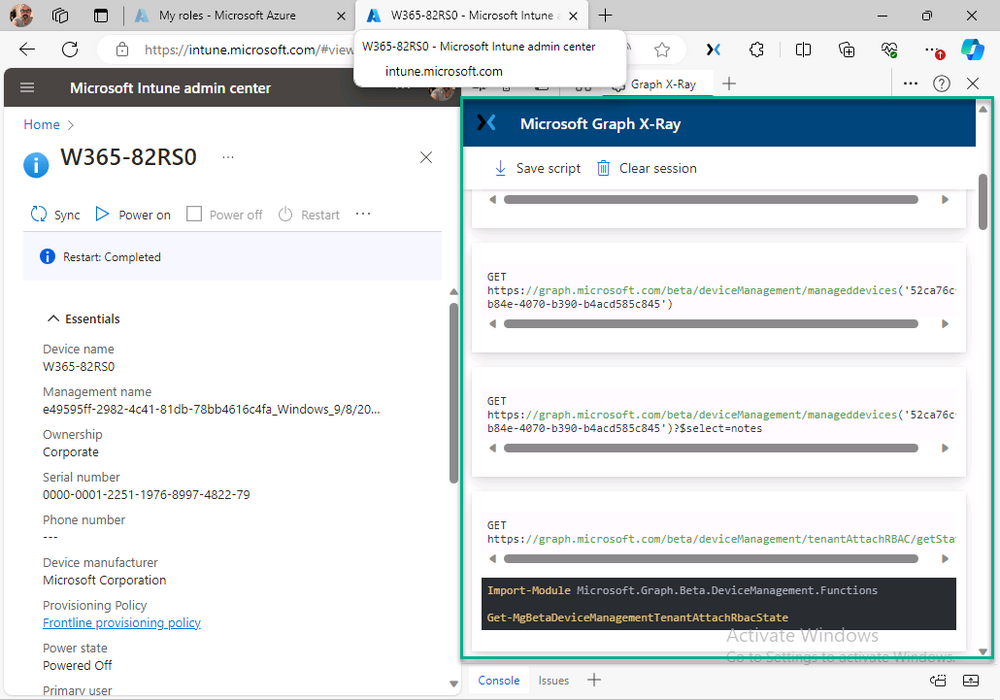
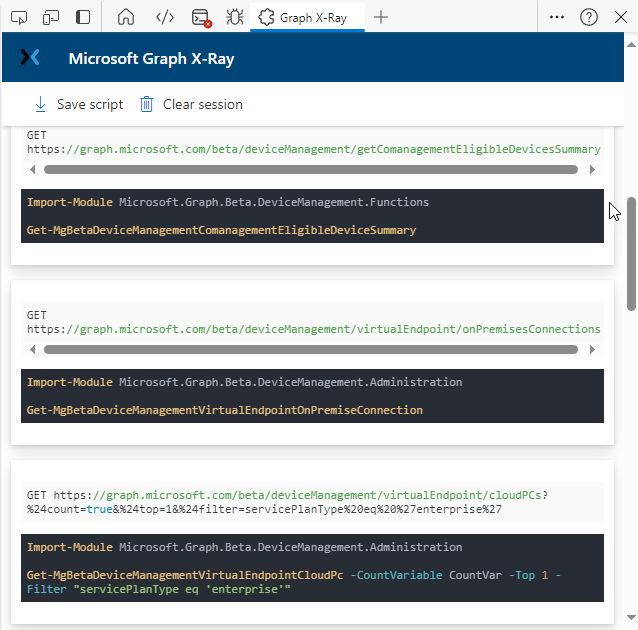
If we compare output of the same action using Graph X-Ray highlighted in the green box below, you can see it’s much easier to comprehend and more useful for scripting a solution. In addition, it removes all the unnecessary information captured via Network developer tools and only shows the Graph calls we are interested in and if available the respective cmdlets that can be used to get that info using PowerShell.
Graph X-Ray will definitely make your job easier when it comes to automating things with Windows 365, but it won’t do all the work for you, so be prepared to get stuck in.
Installing Graph X-Ray
Installing Graph X-Ray is simple. You can download it directly from http://graphxray.merill.net or if using Microsoft Edge click here.
After downloading the extension by clicking on Get, you’ll need to Add the extension to your browser. Click on Add extension.
You’ll be informed of the progress.
Using the extension
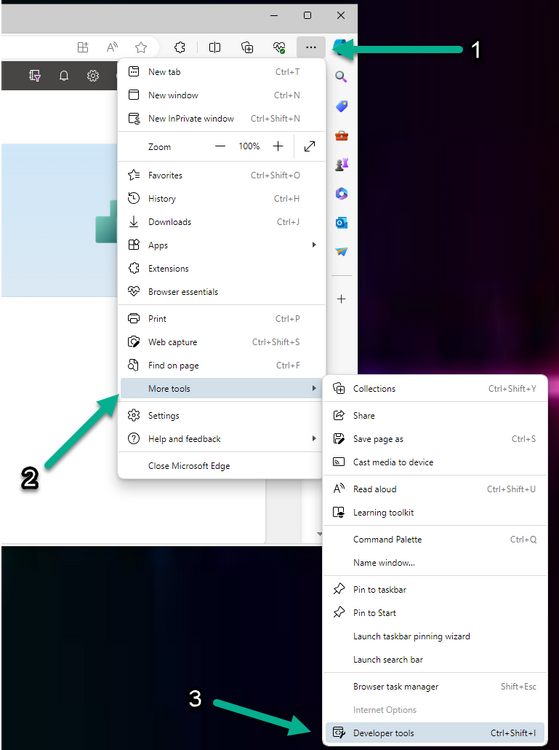
After installing the extension (in Edge in our example), you can access it via Developer Tools by using the shortcut keys CTRL+SHIFT+I or by clicking on the 3 dots or ellipses (1) and then selecting More Tools (2) and finally clicking on Developer Tools (3) as per the picture below.
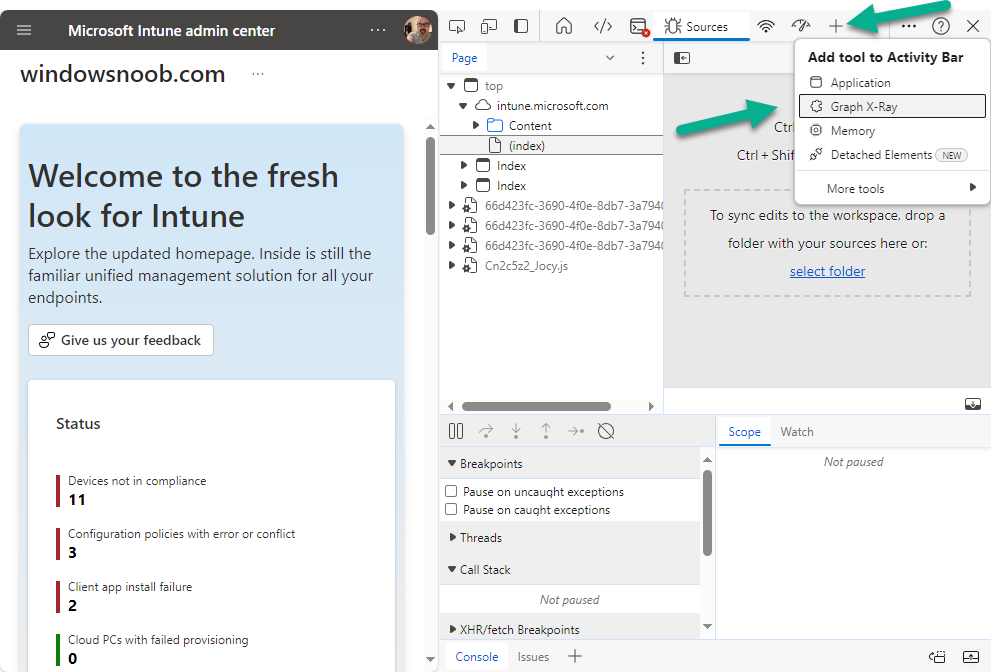
Once done, click on + and then select the Graph X-Ray extension.
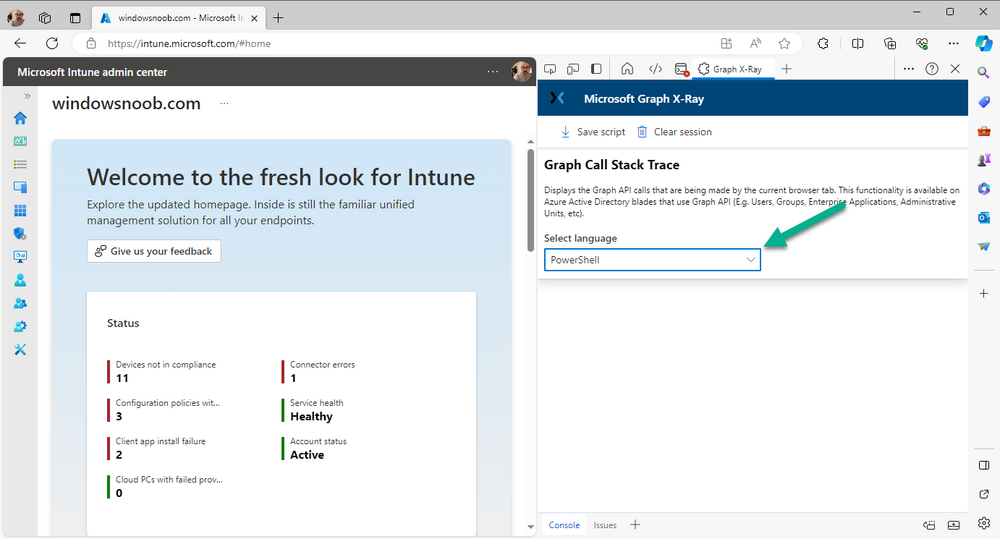
The Graph X-Ray developer tool is now available in your web-browser. Once enabled, you can select the chosen language (PowerShell, C#, Java, JavaScript, Objective C or Go) by clicking on the drop down, we will focus on PowerShell examples only for this mini-series.
As Graph X-Ray is focused on revealing hidden gems in apps/portals that use the Graph API, you can start seeing it’s power by launching a portal such as Microsoft Intune (which uses the Graph API) to review some of the data it reveals about your Windows 365 Cloud PC’s. So let’s get started. Below we browsed to the Intune console and launch Graph X-Ray as shown above, next we clicked on the Windows 365 Provisioning node in Intune.
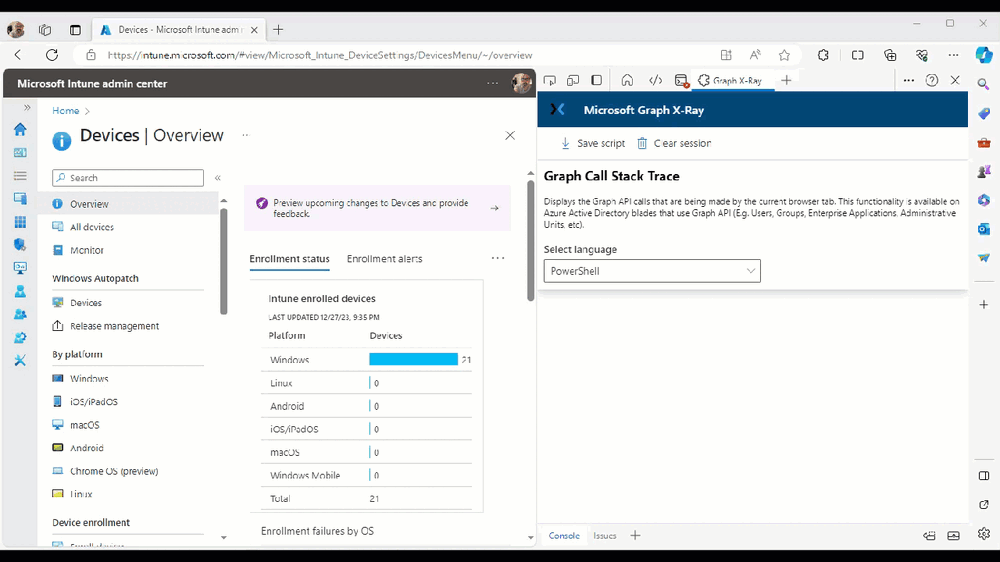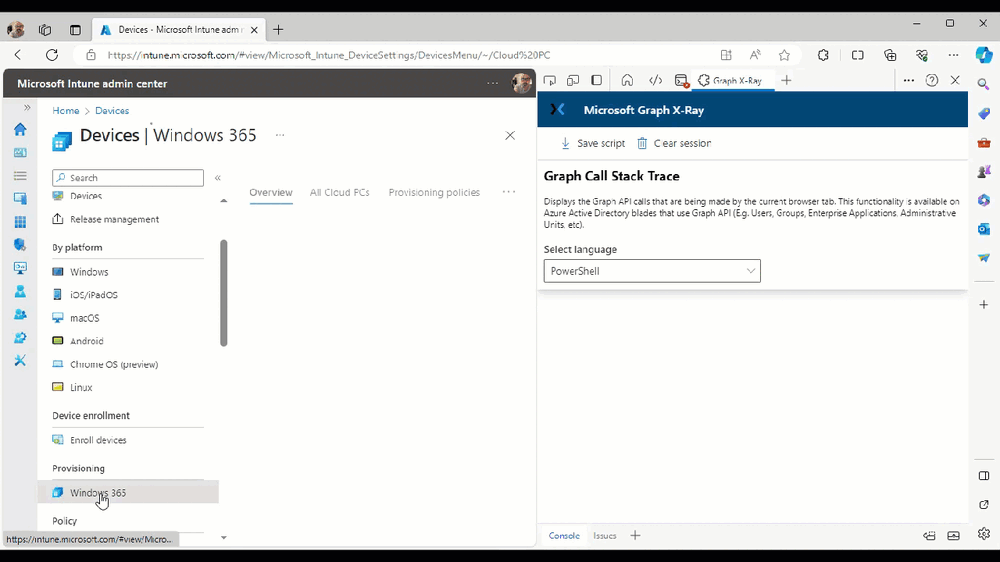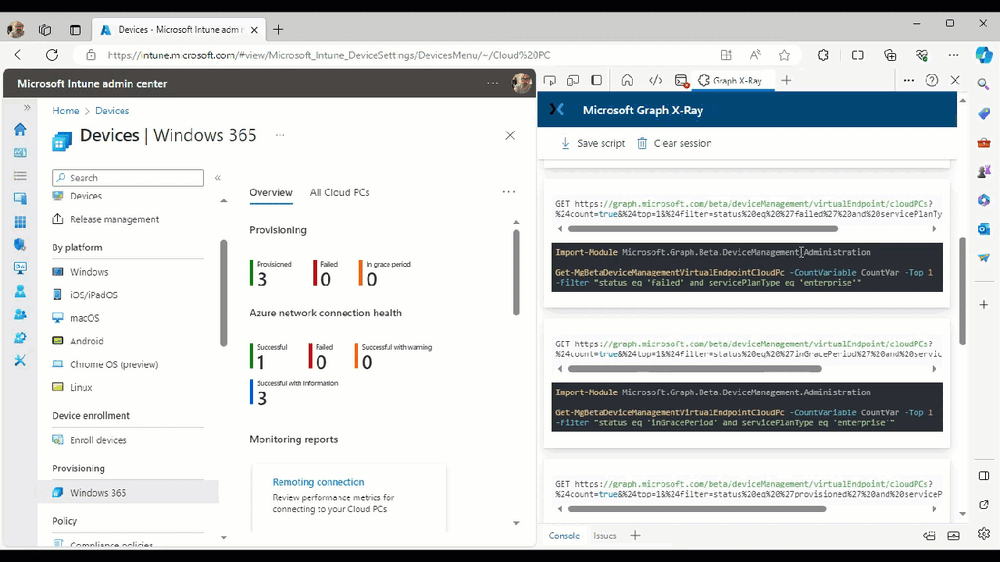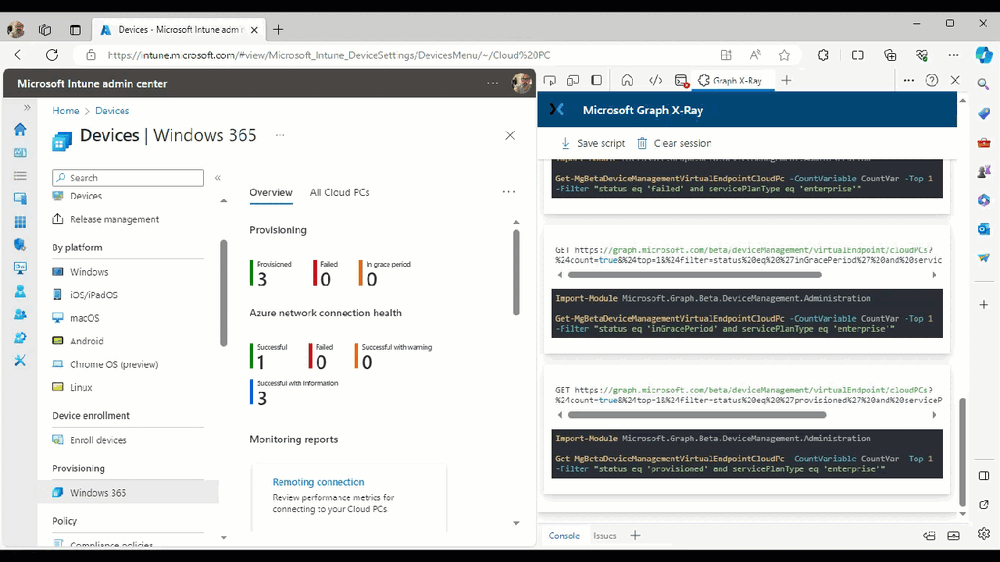
The amount of data revealed is shown in the Graph X-Ray window.
From that window you can copy snippets of code that interest you
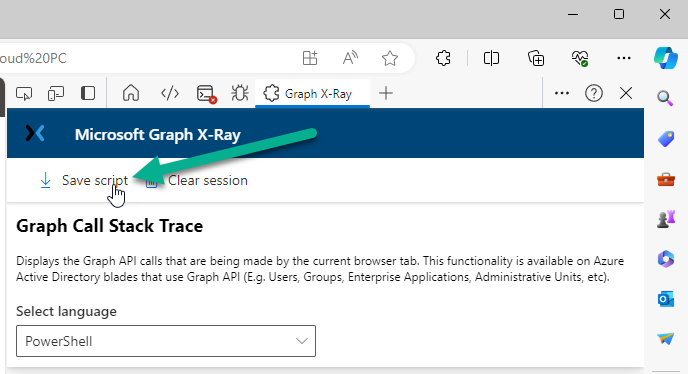
or save the entire script by clicking on Save script.
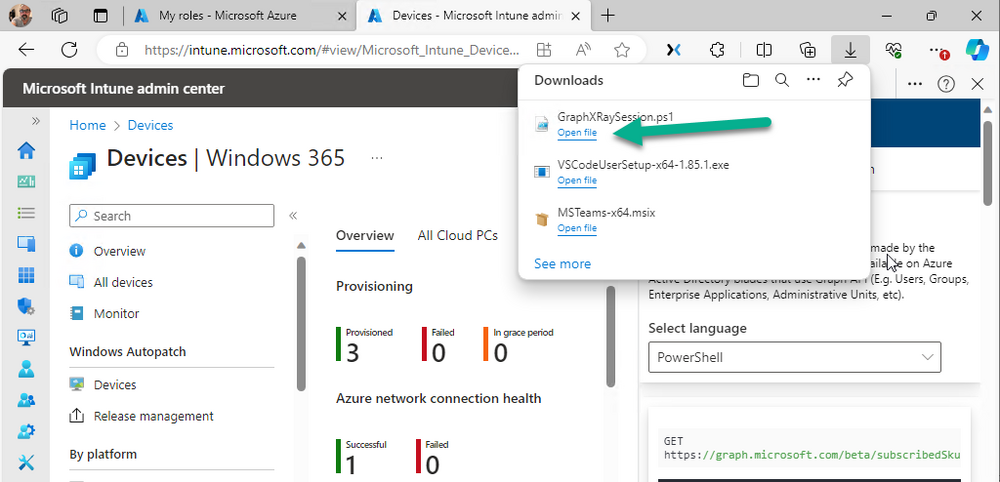
And then you can open that script in Visual Studio Code
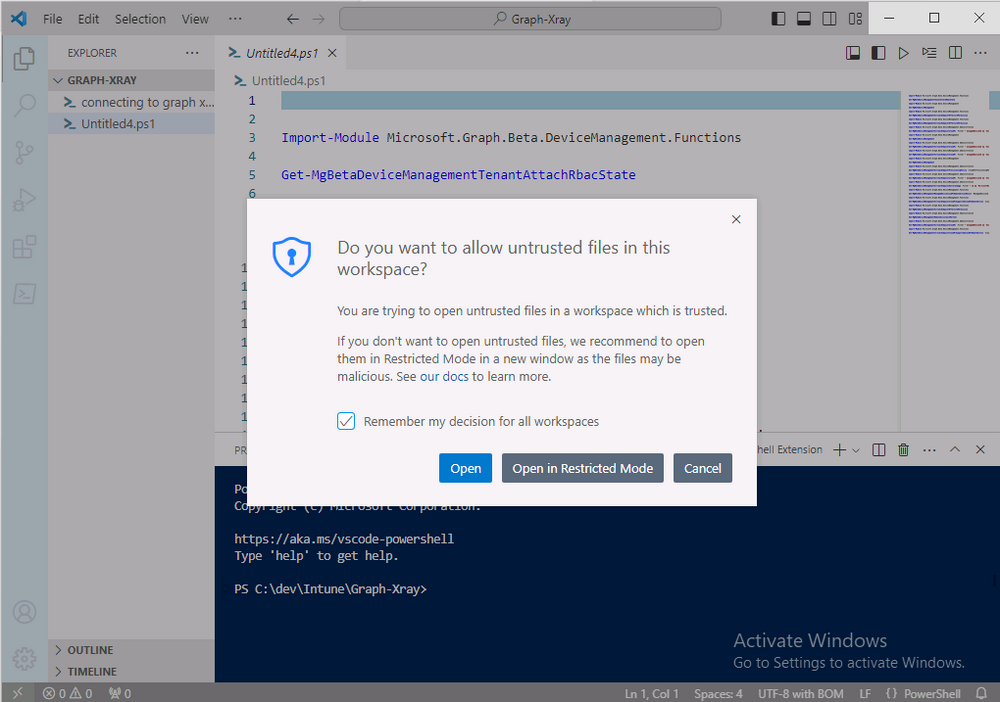
If you get a warning about restricted spaces, make your choice to continue
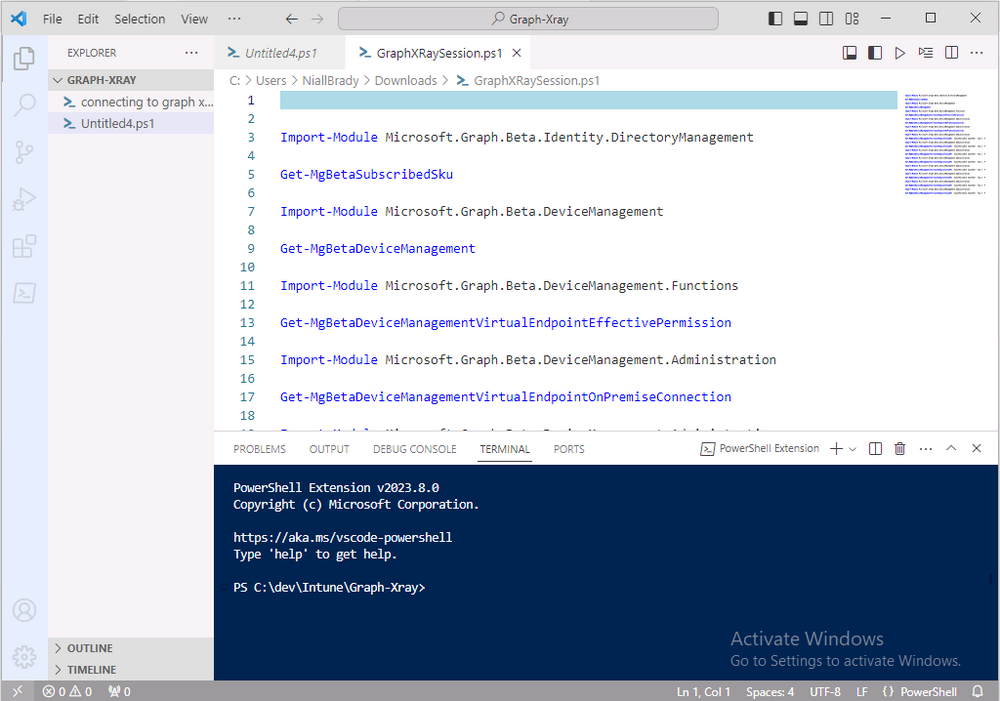
and the Graph X-Ray session script opens in Visual Studio Code.
But remember even though we saved a script of what we were doing at the time (reviewing the Windows 365 node in Intune) it won’t be enough to do everything that you just revealed. So let’s dig deeper.
Running code produced by Graph X-Ray
Next, let’s try and run some of the code produced by Graph X-Ray to see how it helps us.
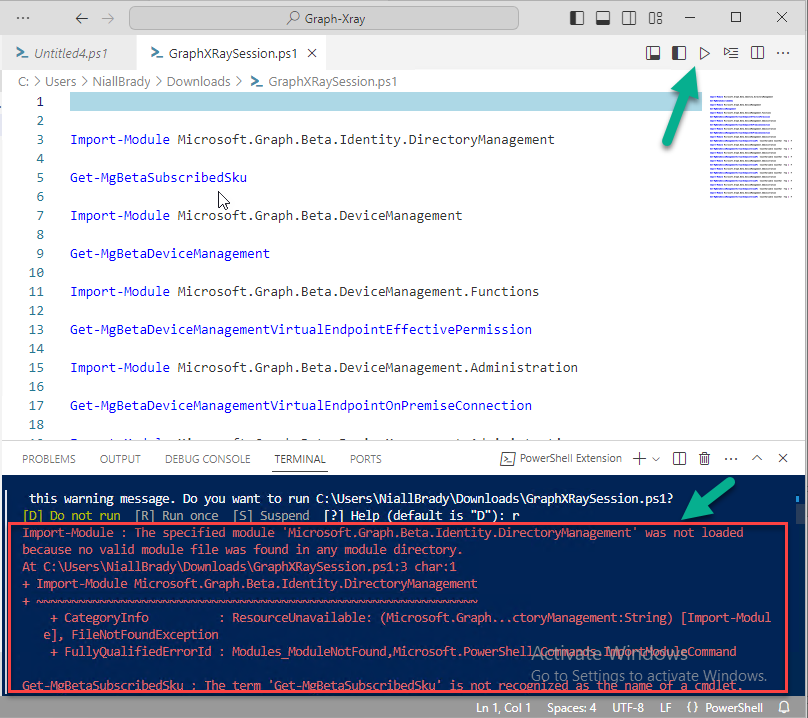
If we simply run the script downloaded above, the following occurs. Lots of errors in red highlighted in the screenshot below.
As we said before, Graph X-Ray helps you but doesn’t do everything. In the example errors highlighted above, we can see it’s trying to import a module that isn’t already installed, so to fix that you’ll need to first install any module that is used in the script you are creating.
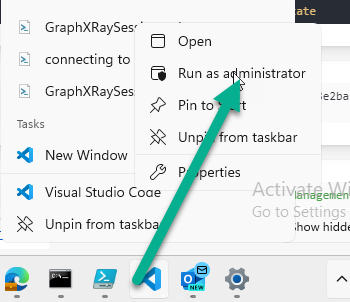
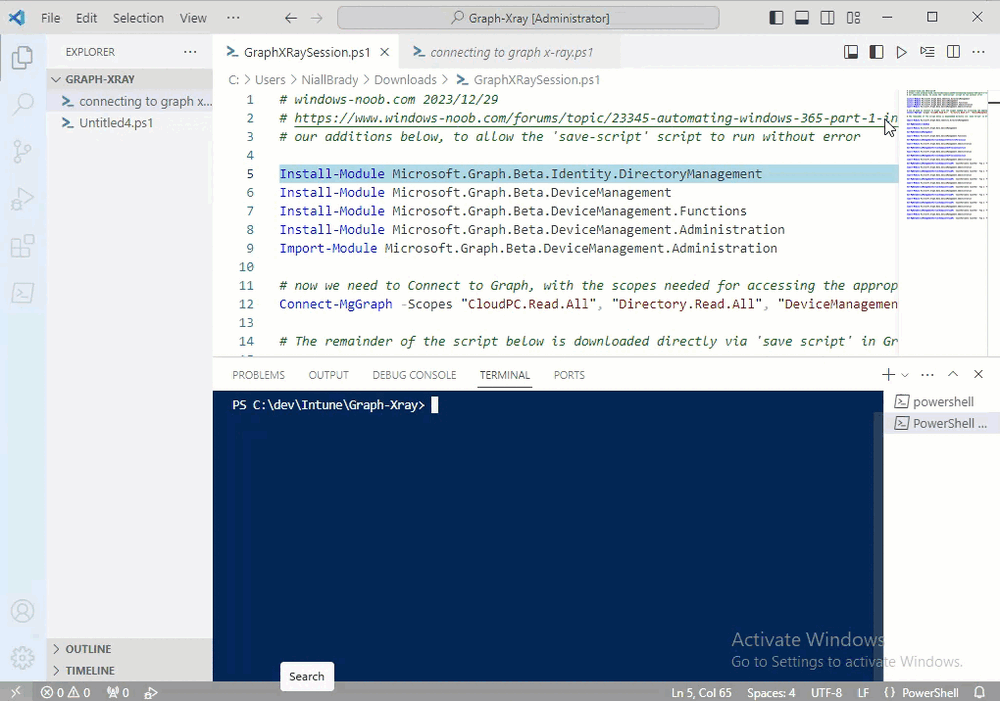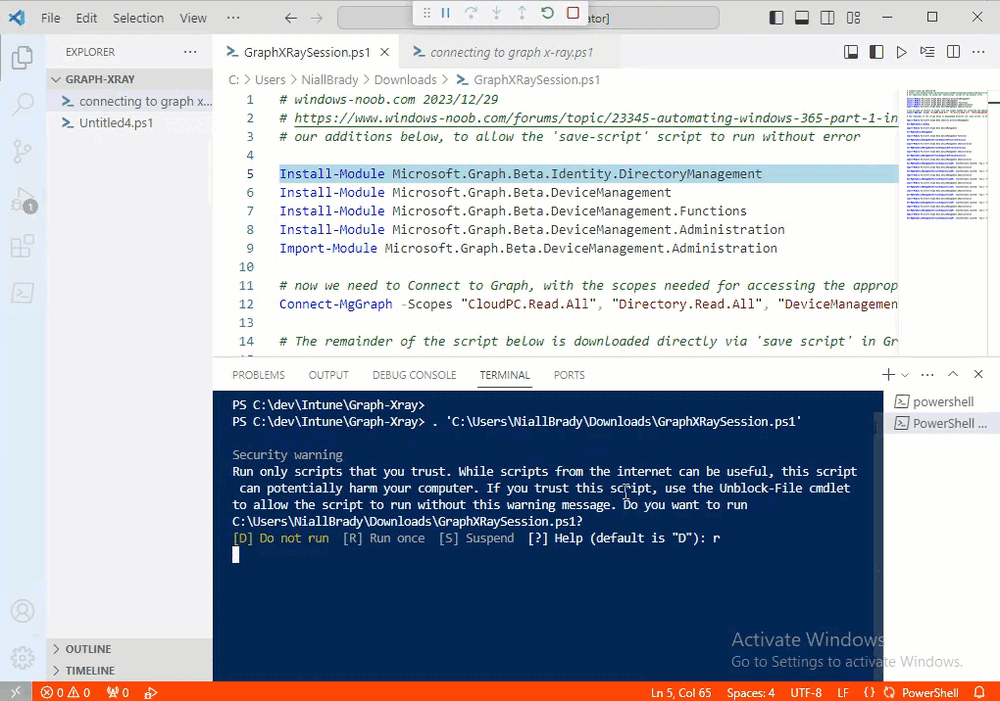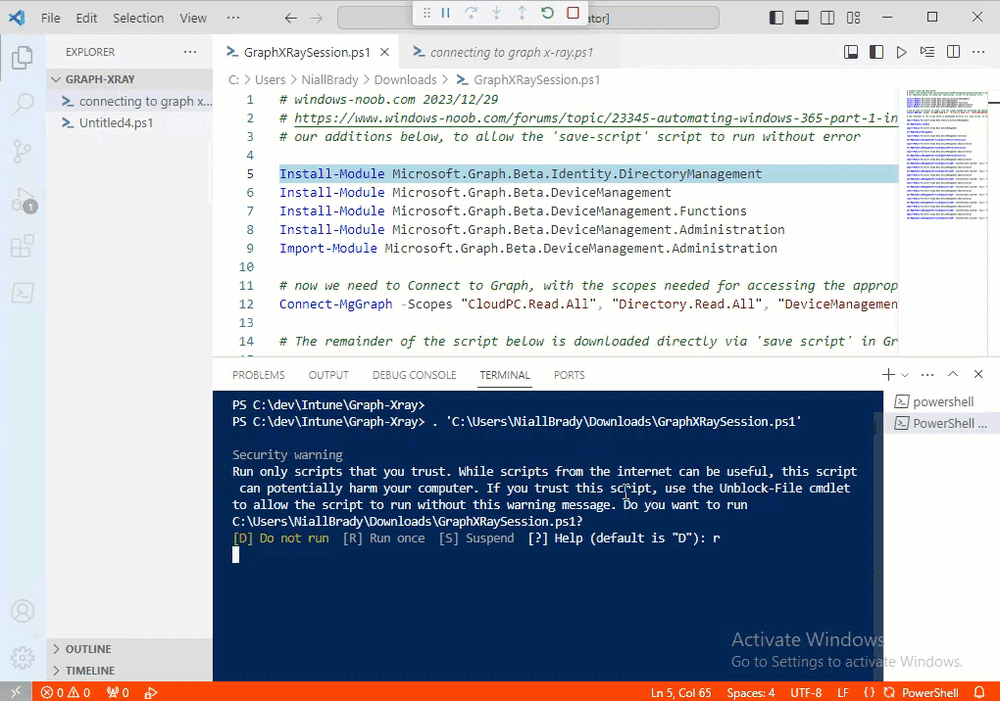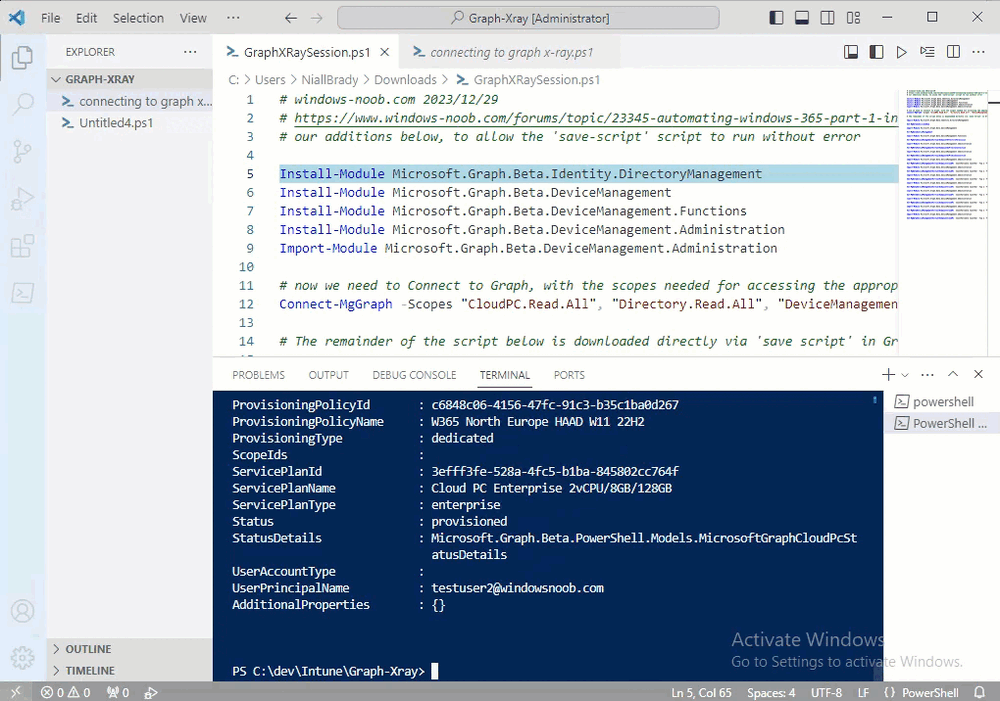
To fix things in the downloaded script, close Visual Studio Code and restart it as Administrator, this is only needed to install those missing PowerShell modules.
Once done, the edited script is shown below, note that we had to run it a few times and browse the output to see if there were any missing scopes.
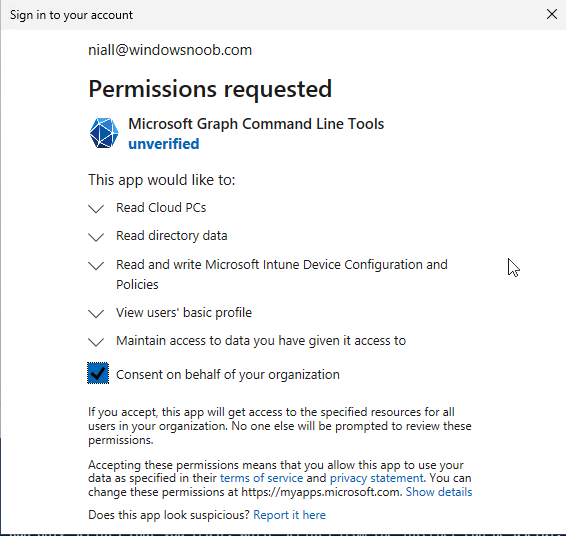
The scopes are added one after another in the script and when added, you’ll be prompted to accept those new permissions.
After Approving that, and running the script the output below shows all the data generated from the edited ‘save script’ content.
Success !
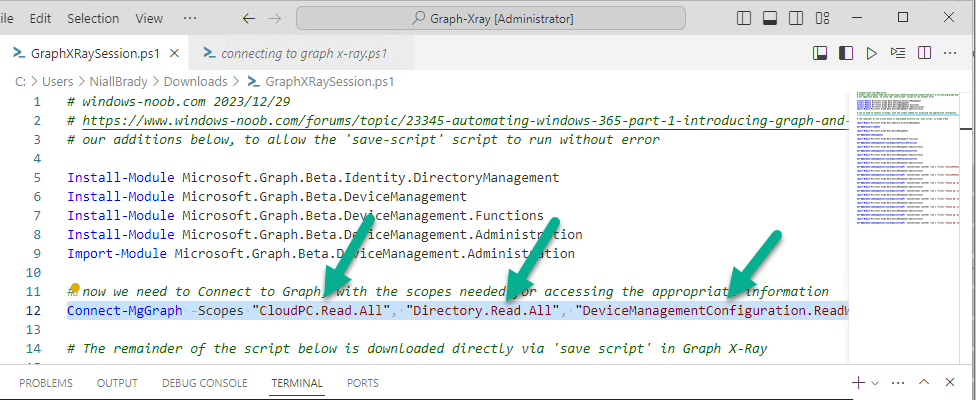
Below is a copy of the script we edited in the GIF above.
# windows-noob.com 2023/12/29 # https://www.windows-noob.com/forums/topic/23345-automating-windows-365-part-1-introducing-graph-and-setting-up-visual-studio-code/ # our additions below, to allow the 'save-script' script to run without error Install-Module Microsoft.Graph.Beta.Identity.DirectoryManagement Install-Module Microsoft.Graph.Beta.DeviceManagement Install-Module Microsoft.Graph.Beta.DeviceManagement.Functions Install-Module Microsoft.Graph.Beta.DeviceManagement.Administration Import-Module Microsoft.Graph.Beta.DeviceManagement.Administration # now we need to Connect to Graph, with the scopes needed for accessing the appropriate information Connect-MgGraph -Scopes "CloudPC.Read.All", "Directory.Read.All", "DeviceManagementConfiguration.ReadWrite.All" # The remainder of the script below is downloaded directly via 'save script' in Graph X-Ray Import-Module Microsoft.Graph.Beta.Identity.DirectoryManagement Get-MgBetaSubscribedSku Import-Module Microsoft.Graph.Beta.DeviceManagement Get-MgBetaDeviceManagement Import-Module Microsoft.Graph.Beta.DeviceManagement.Functions Get-MgBetaDeviceManagementVirtualEndpointEffectivePermission Import-Module Microsoft.Graph.Beta.DeviceManagement.Administration Get-MgBetaDeviceManagementVirtualEndpointOnPremiseConnection Import-Module Microsoft.Graph.Beta.DeviceManagement.Administration Get-MgBetaDeviceManagementVirtualEndpointOnPremiseConnection Import-Module Microsoft.Graph.Beta.DeviceManagement.Administration Get-MgBetaDeviceManagementVirtualEndpointCloudPc -CountVariable CountVar -Top 1 -Filter "servicePlanType eq 'enterprise'" Import-Module Microsoft.Graph.Beta.DeviceManagement.Administration Get-MgBetaDeviceManagementVirtualEndpointCloudPc -CountVariable CountVar -Top 1 -Filter "servicePlanType eq 'enterprise'" Import-Module Microsoft.Graph.Beta.DeviceManagement.Administration Get-MgBetaDeviceManagementVirtualEndpointCloudPc -CountVariable CountVar -Top 1 -Filter "status eq 'provisioned' and servicePlanType eq 'enterprise'" Import-Module Microsoft.Graph.Beta.DeviceManagement.Administration Get-MgBetaDeviceManagementVirtualEndpointCloudPc -CountVariable CountVar -Top 1 -Filter "status eq 'inGracePeriod' and servicePlanType eq 'enterprise'" Import-Module Microsoft.Graph.Beta.DeviceManagement.Administration Get-MgBetaDeviceManagementVirtualEndpointCloudPc -CountVariable CountVar -Top 1 -Filter "status eq 'failed' and servicePlanType eq 'enterprise'" Import-Module Microsoft.Graph.Beta.DeviceManagement.Administration Get-MgBetaDeviceManagementVirtualEndpointCloudPc -CountVariable CountVar -Top 1 -Filter "status eq 'inGracePeriod' and servicePlanType eq 'enterprise'" Import-Module Microsoft.Graph.Beta.DeviceManagement.Administration Get-MgBetaDeviceManagementVirtualEndpointCloudPc -CountVariable CountVar -Top 1 -Filter "status eq 'provisioned' and servicePlanType eq 'enterprise'" Import-Module Microsoft.Graph.Beta.DeviceManagement.Administration Get-MgBetaDeviceManagementVirtualEndpointCloudPc -CountVariable CountVar -Top 1 -Filter "status eq 'failed' and servicePlanType eq 'enterprise'"
Keep in mind that you might want to edit the -Top 1 references to -Top 5 or some other figure to increase the output when making your own scripts based on the above.
Related reading
- Introduction to Graph X-Ray
- Microsoft Graph Overview – https://learn.microsoft.com/en-us/graph/overview
- Microsoft Graph X-Ray Edge add-on – https://microsoftedge.microsoft.com/addons/detail/graph-xray/oplgganppgjhpihgciiifejplnnpodak
Summary
The Graph X-Ray extension is a fantastic tool to help you find out what is going on behind the scenes for Graph API tasks. Using the Graph X-Ray extension in your web browser makes it easier to automate many tasks for your Windows 365 Cloud PC’s using PowerShell.



Love the detailed write up with all the illustrations!
thanks Merill ! that means a lot coming from you