Introduction
I’m currently blogging about a series of DEM in 20 webinars from 1E, you can find each episode that I’ve blogged about (including this one) below:
- Episode 1. How to find and fix Slow Endpoints
- Episode 2. That crashy app
- Episode 3. Dealing with annoying admin requests
- Episode 4. That Change Management Success Rate Struggle
- Episode 5. Will Printer Audits continue to exist?
- Episode 6. Are non compliant devices dangerous ? <- you are here
In this DEM in 20 video, Alexander Adams (Product Manager, 1E) and Michael Wright (Director of Product Marketing, 1E) are joined by guest speaker Rob Key (Senior Solutions Engineer, 1E) and talk about non compliant devices and whether they are dangerous or not in your environment.
Rob demonstrates the act of quarantining affected devices (both reactively and proactively) to minimize damage within your organization.
 Device compliance is always a big topic at any organization. Users should by now be aware that Windows patches come on a monthly basis, and they’ll get prompted to reboot to remain compliant. They also understand that keeping their computer updated with patches helps to keep it compliant.
Device compliance is always a big topic at any organization. Users should by now be aware that Windows patches come on a monthly basis, and they’ll get prompted to reboot to remain compliant. They also understand that keeping their computer updated with patches helps to keep it compliant.
However device compliance can go much further, for example making sure certain software titles are not installed on the device by enforcing rules for specific applications, or by enforcing individual settings within the Windows operating system itself.
Defining a non compliant device
A device is marked as non-compliant if its out of spec according to what the company has defined as required compliance rules for use within the organization. This can become dangerous when for example that non-compliant device gets infected with a zero day exploit and spreads it to other vulnerable devices in the organization.
There are many different aspects that can influence compliance, such as whether it has the latest virus definitions, whether it has the hard drive encrypted to protect company data at rest or whether it has the latest Windows updates installed on time to protect from zero day vulnerabilities.
This becomes harder to manage when users use their own hardware in a BYOD (Bring Your Own Device) type of scenario, as these devices are used both at home as well as in the office, and perhaps the users’ kids could install an application on that device that pushes it out of compliance and can potentially endanger the organization.
BYOD can of course be controlled by having the 1E Tachyon client installed on those devices. Using Tachyon Explorer, you can query installed software on computers to generate a list of computers with the software that is installed on them.
Acting on vulnerable software
Some companies limit the web browsers that their users use. This example scenario involves a certain software title Mozilla Firefox. Let’s imagine that a version of Mozilla Firefox is vulnerable to a zero day exploit and we need to remove it or inform the users that this version of the browser is not approved software.
Side note: Mozilla Firefox is my personal favorite web browser, thank you Mozilla for all that you do !
To query the software installed on computers in your organization simply start Tachyon Explorer and in the I want to know text box, enter List installed software.
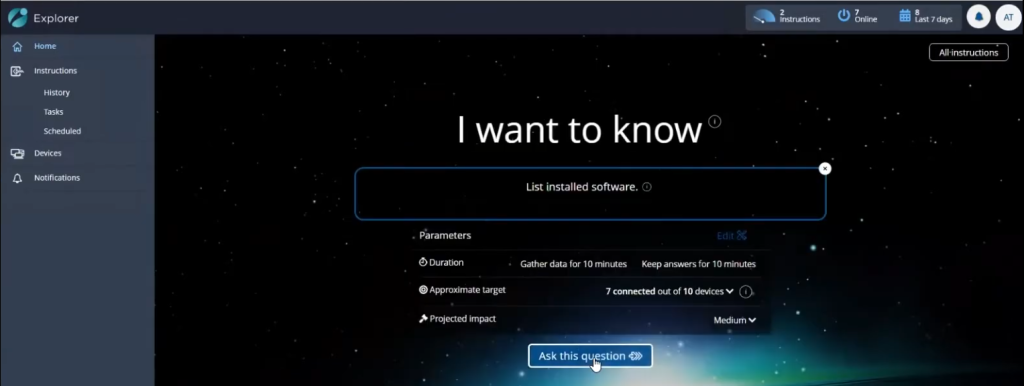 Clicking on Ask this question will generate a list of computers and the associated software that they have installed on them sorted by device name, publisher, product, version, architecture and install date.
Clicking on Ask this question will generate a list of computers and the associated software that they have installed on them sorted by device name, publisher, product, version, architecture and install date.
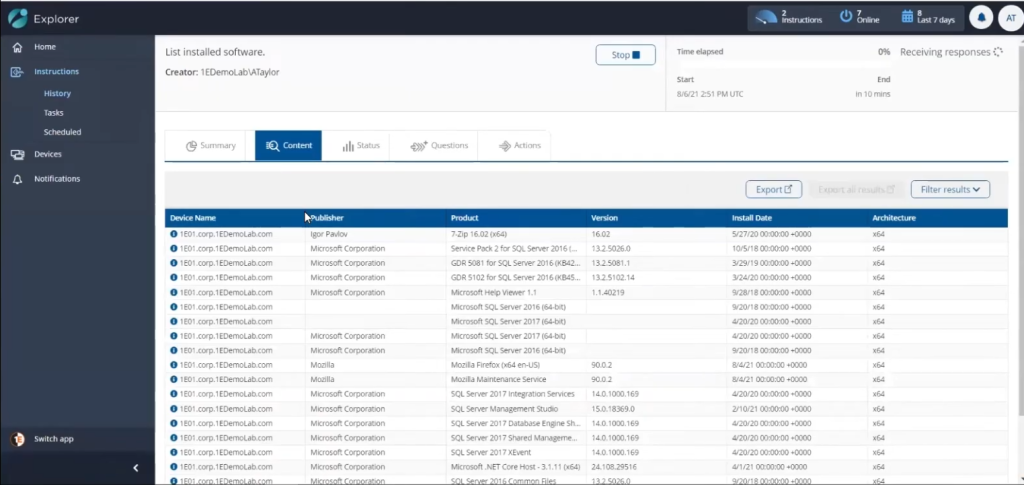 To query for that software in just a few clicks, select a device with Mozilla listed in the Publisher field, then click on search.
To query for that software in just a few clicks, select a device with Mozilla listed in the Publisher field, then click on search.
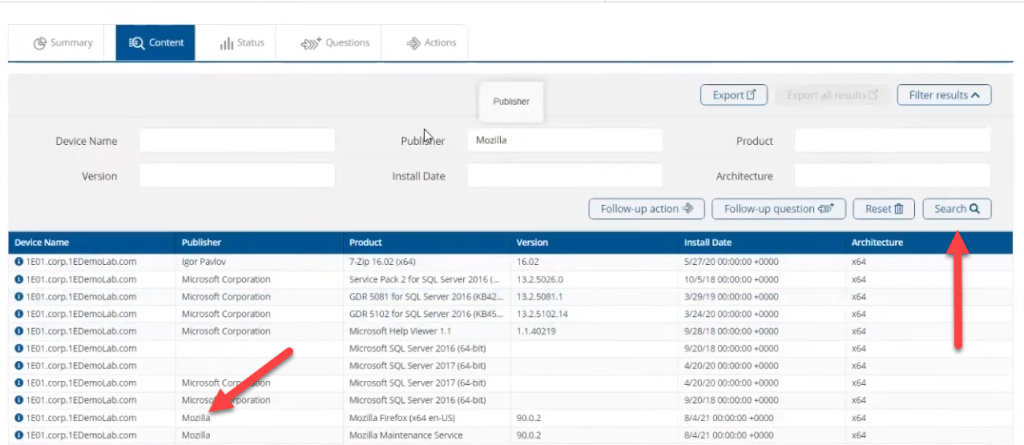 That will generate a new list of devices with software installed from the publisher Mozilla. Notice how the product column lists the different software titles from this publisher.
That will generate a new list of devices with software installed from the publisher Mozilla. Notice how the product column lists the different software titles from this publisher.
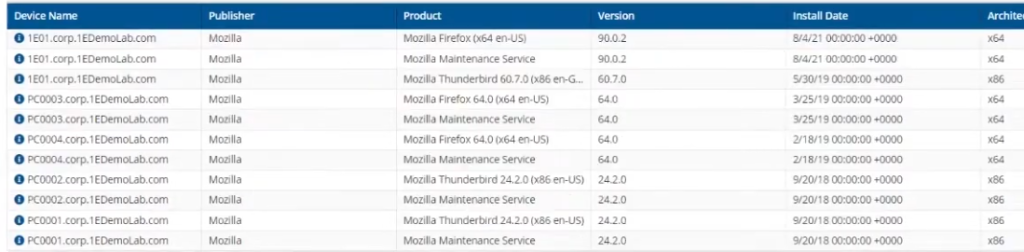 To fine tune this further, you could click in the product column itself and select Mozilla Firefox and start a new search with results containing devices that have that specific software installed. The question is how deep do you want to go ? With Tachyon Explorer you have the power to find what you want easily and instantly.
To fine tune this further, you could click in the product column itself and select Mozilla Firefox and start a new search with results containing devices that have that specific software installed. The question is how deep do you want to go ? With Tachyon Explorer you have the power to find what you want easily and instantly.
Reactively quarantining devices
In this scenario you know what you are looking for, and you found it using Tachyon Explorer as shown above. Now you are going to quarantine those devices that have the software installed. These devices already have the Configuration Manager client installed but let’s imagine that there are devices where the Configuration Manager client is not working properly and you need to close that gap to keep the organization safe.
To do that, you could select a device you are interested in (in this case PC003) and click on Follow-up action.
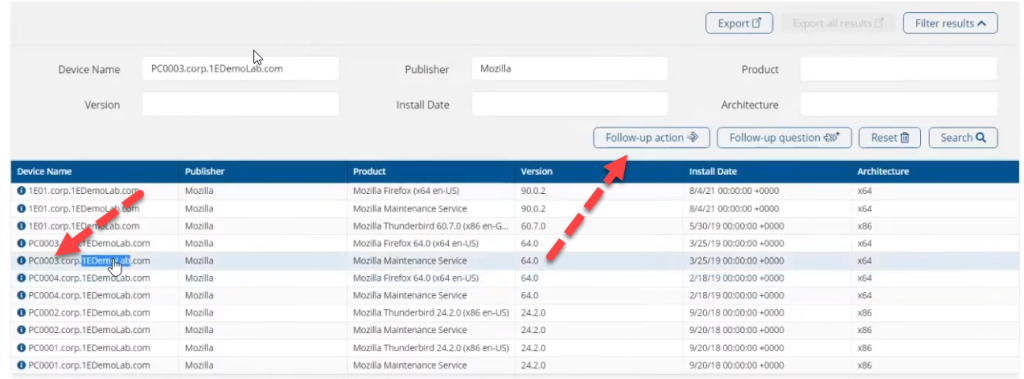 In the Follow-up actions search field that appears
In the Follow-up actions search field that appears
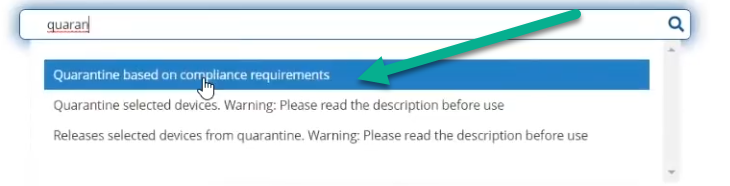
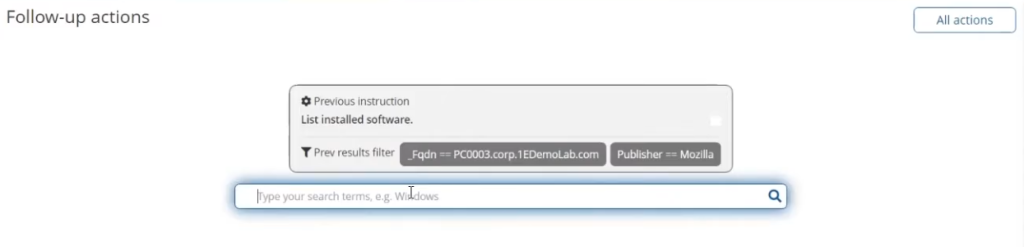 Enter quarantine as the search term and from the list of available choices select Quarantine based on compliance requirements.
Enter quarantine as the search term and from the list of available choices select Quarantine based on compliance requirements.
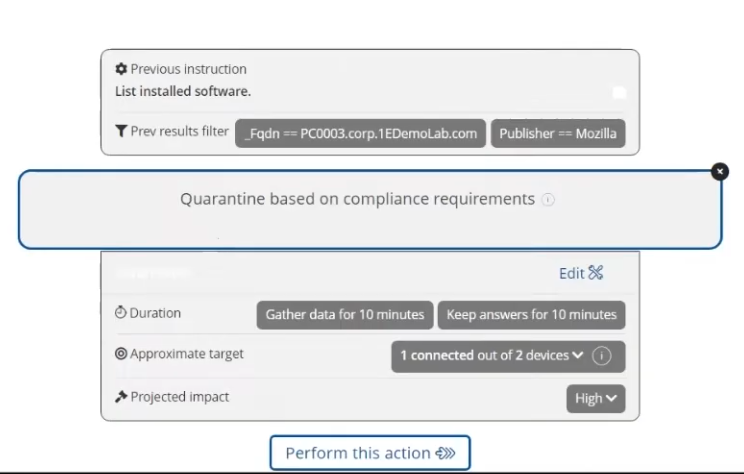
Once selected you get more options, and once you’ve made your choices and click Perform this action, you’ll be prompted to confirm your credentials to verify that you are authorzied to perform the action.
On the targeted client, the change is instant and they can no longer browse the local network or the internet while quarantined. But rather than leave the user clueless as to why they cannot browse networks, they will see a popup from the 1E Client informing them that their computer is out of compliance, placed in quarantine and provide them some choices to remediate the problem or to get help.
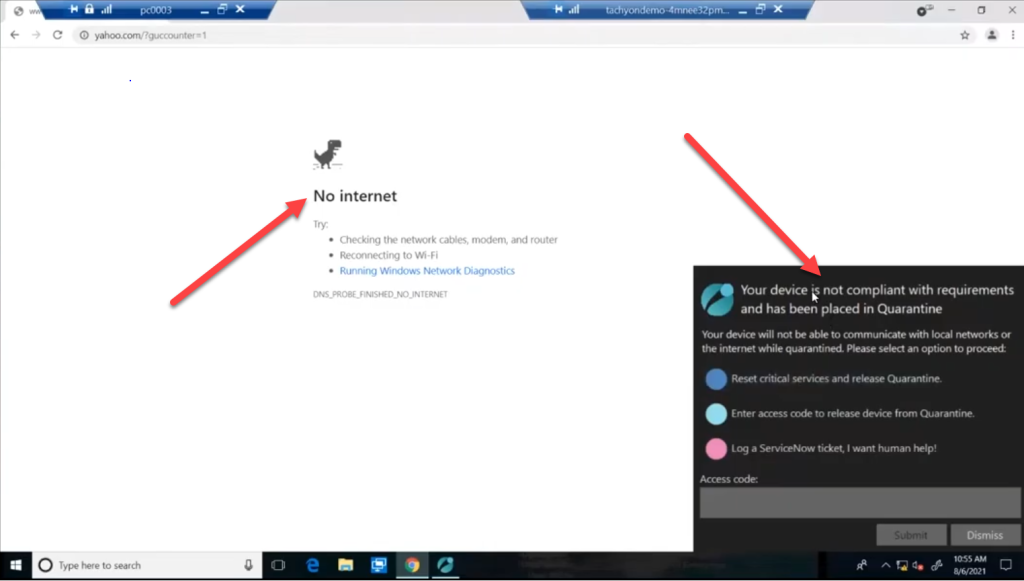 Tachyon Explorer still has a direct connection to these clients while they are quarantined, meaning that they can be repaired, queried or acted upon even while in that state.
Tachyon Explorer still has a direct connection to these clients while they are quarantined, meaning that they can be repaired, queried or acted upon even while in that state.
Proactively quarantining devices based on policy
1E Guaranteed State allows you to define compliance policies that are monitored by the client and made up of built-in or custom rules to proactively quarantine one, ten or several hundred thousand computers to minimize threats being allowed in your organization.
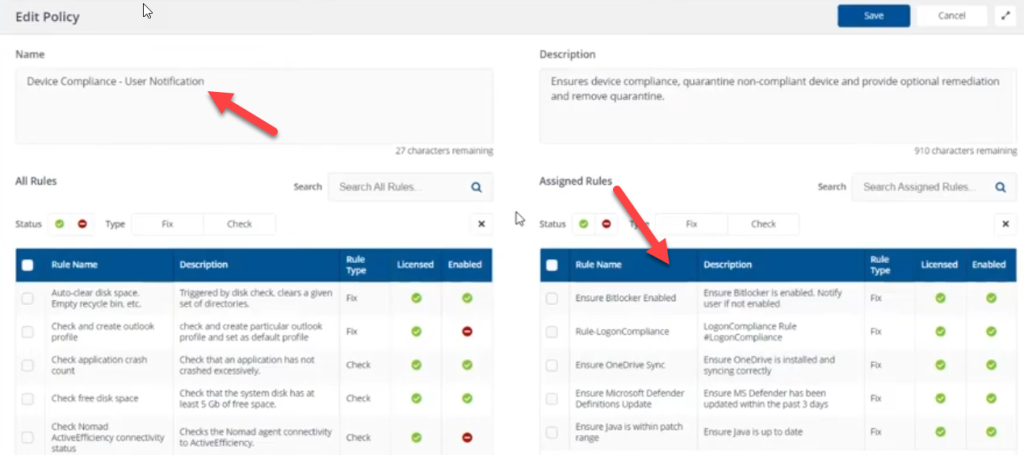 These policies are made up of rules that typically wouldn’t force non-compliance very often as we don’t unnecessarily piss off users, but they are created to keep your organization secure.
These policies are made up of rules that typically wouldn’t force non-compliance very often as we don’t unnecessarily piss off users, but they are created to keep your organization secure.
Enforcing at speed
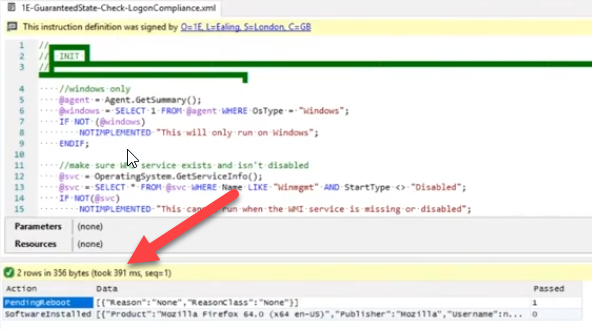
The time needed for applying or querying these rules (and their custom fragments) is in milliseconds which allows Tachyon to very quickly query hundreds of thousands of computers at a time and act accordingly.
Not only is it fast, but it can scale as necessary, for example if you were delivering a payload in addition to the enforcement and didn’t want to impact the network.
 The Colonial pipeline hack, where compromised passwords were used to hack into their systems is a perfect example of where quarantining devices would have made perfect sense, limit the damage as quickly as you can by quarantining them.
The Colonial pipeline hack, where compromised passwords were used to hack into their systems is a perfect example of where quarantining devices would have made perfect sense, limit the damage as quickly as you can by quarantining them.
Tachyon Explorer maintains a direct connection to these clients while they are quarantined so that they can be monitored, repaired or secured.
Conclusion
Non Compliant devices are dangerous if the compliance policies you create allow malicious software to get through, allowing attack vectors from dangerous actors to infiltrate your network and wreak havoc on a potentially massive scale.
With the power of 1E Guaranteed State and Tachyon Explorer, you have access to easy to use (yet powerful) tools to proactively or reactively quarantine affected clients to quickly secure your organization.