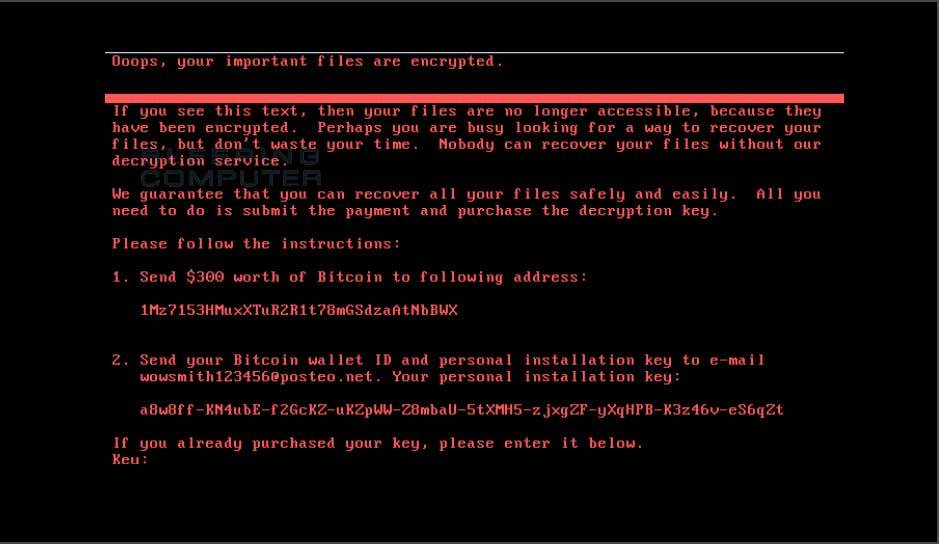
The return of EternalBlue
On June 27th 2017, another RansomWare attack took hold targeting the same eternal blue (SMBv1) vulnerabilities as WannaCry before it. This attack however doesn’t reach out to the internet like WannaCry did, it’s an internal network attack.
However, this attack seems to have deliberately targeted businesses in Ukraine, and as the email address used for encryption keys was disabled almost immediately, there’s no point in anyone paying ransom if their files are encrypted as they’d never get a reply (with the decryption info).
Patch Patch Patch
If you haven’t done it already (and if you have not, why not especially after WannaCry), head over to this Technet link and apply the patches, do it.
Stopping the damage
That said, a security researcher found a way of stopping the ransomware from encrypting machines affected by placing a read-only file called Perfc in the Windows directory, eg:
C:\Windows\Perfc
The presence of that file will be enough to stop the contents of the hard disc from being encrypted by this malware, however the reason this malware spread in the first place is down to vulnerabilities (unpatched) in the operating system. Those vulnerabilities include two from the leaked NSA exploits, so if you’ve patched your operating systems against those known vulnerabilities you should be safe.
Protection against this new ransomware attack
Microsoft have advised the following to keep you protected against this (and similar) RansomWare attacks:
“We recommend customers that have not yet installed security update MS17-010 to do so as soon as possible. Until you can apply the patch, we also recommend two possible workarounds to reduce the attack surface:
- Disable SMBv1 with the steps documented at Microsoft Knowledge Base Article 2696547 and as recommended previously
- Consider adding a rule on your router or firewall to block incoming SMB traffic on port 445
As the threat targets ports 139 and 445, you customers can block any traffic on those ports to prevent propagation either into or out of machines in the network. You can also disable remote WMI and file sharing. These may have large impacts on the capability of your network, but may be suggested for a very short time period while you assess the impact and apply definition updates.
Windows Defender Antivirus detects this threat as Ransom:Win32/Petya as of the 1.247.197.0 update. Windows Defender Antivirus uses cloud-based protection, helping to protect you from the latest threats.
For enterprises, use Device Guard to lock down devices and provide kernel-level virtualization-based security, allowing only trusted applications to run, effectively preventing malware from running.
Monitor networks with Windows Defender Advanced Threat Protection, which alerts security operations teams about suspicious activities. Download this playbook to see how you can leverage Windows Defender ATP to detect, investigate, and mitigate ransomware in networks: Windows Defender Advanced Threat Protection – Ransomware response playbook.”