Introduction
Windows Information Protection or WIP (formally known as Enterprise Data Protection or EDP) is explained nicely in Microsoft’s own words and i’ve included a quote of that below:-
With the increase of employee-owned devices in the enterprise, there’s also an increasing risk of accidental data leak through apps and services, like email, social media, and the public cloud, which are outside of the enterprise’s control. For example, when an employee sends the latest engineering pictures from their personal email account, copies and pastes product info into a tweet, or saves an in-progress sales report to their public cloud storage. .
Windows Information Protection helps to protect against this potential data leakage without otherwise interfering with the employee experience. WIP also helps to protect enterprise apps and data against accidental data leak on enterprise-owned devices and personal devices that employees bring to work without requiring changes to your environment or other apps.
In other words, you can use WIP to protect enterprise data from leaving the enterprise. The prerequisites for WIP are as follows, you’ll need a Windows 10 operating system (that is version 1607 or later) and you’ll need a management solution such as Intune or SCCM or a 3rd party MDM solution. in addition, you’ll need a license for Azure AD Premium. To gain access to the latest capabilities in Intune you should use Windows 10 Creators Update (version 1703).
In this article I’m going to show you how to set this up with Intune (in Azure) and I’ll give some examples of how enterprise protected data acts when in different scenarios, in addition, I’ll explain how you can audit or review logs about this and have a quick glance at the reporting capabilities in Intune. I’ve already configured Azure for Automatic Enrollment but it’s up to you whether you want to use that option (or not).
In this guide I assume you’ve already got an Azure subscription (trial or otherwise) and Intune. If you don’t have one you can sign up for a 30 day free Intune trial here. I used Enterprise Mobility + Security E3 licenses for the users in this lab.
Making sure Azure is ready for WIP
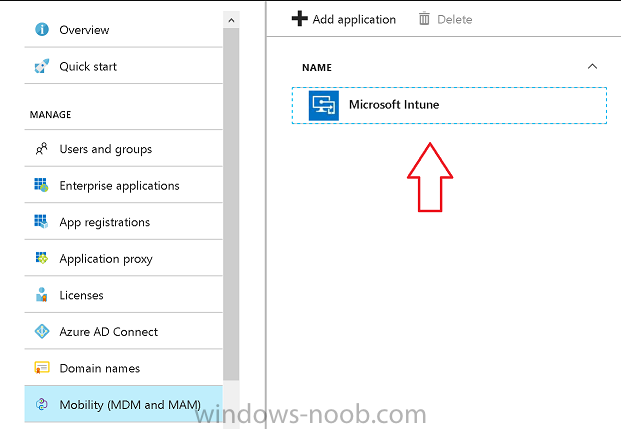
In Azure, select Azure Active Directory from Services and click on Mobility (MDM and MAM).
Next Click on Microsoft Intune
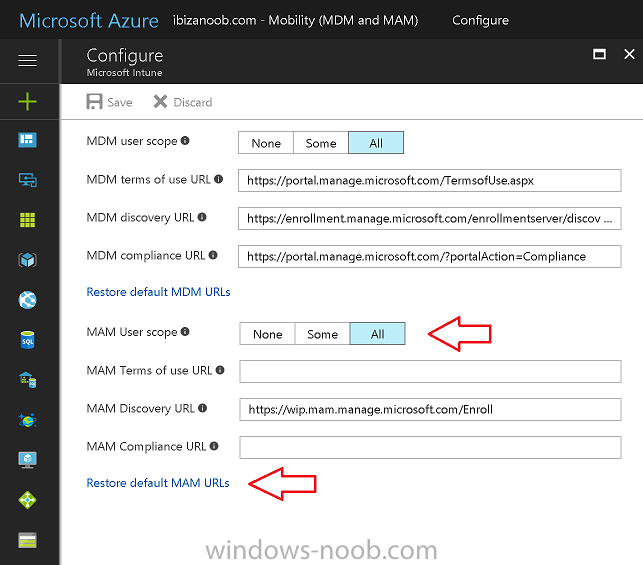
From the choices listed, choose Restore default MAM URLs and then select the scope. You can add your own urls too (for the MAM Terms of use URL and MAM Compliance URL) if you wish but in this example I did not.
Save your settings when done.
Create a WIP Policy
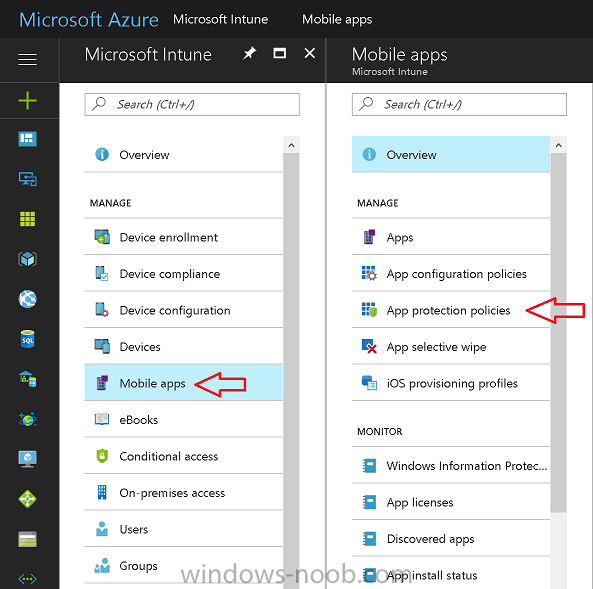
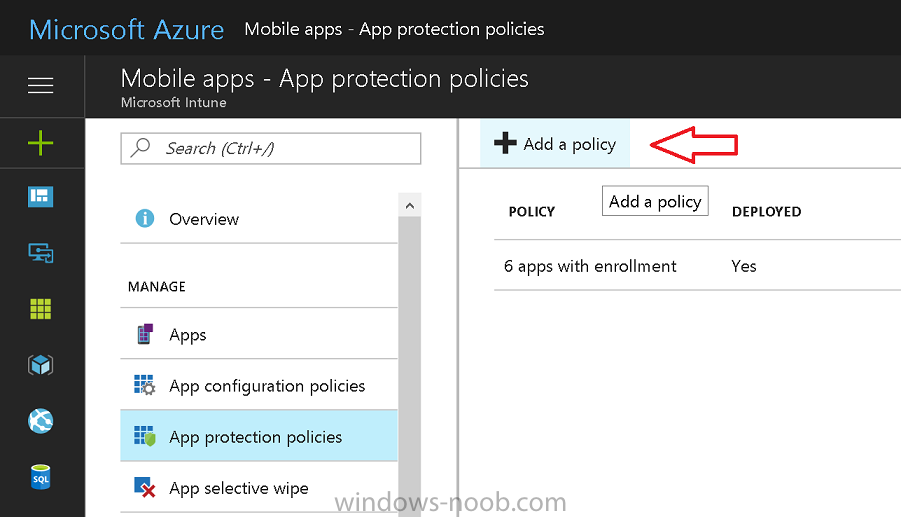
Now that you’ve configured MAM in Azure, it’s time to create your first WIP policy. To do that, in the Microsoft Intune service in Azure, select Mobile Apps then click on App protection policies.
And click on Add a policy.
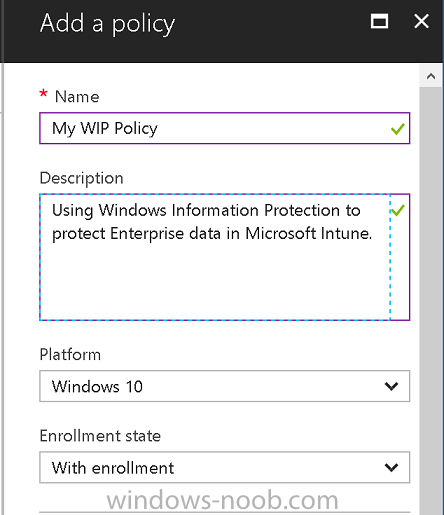
Give the policy a descriptive name, and optionally a description of what it does, in the Platform drop down select Windows 10 from the choices available. Next choose your enrollment option for Enrollment State, select With Enrollment for this guide. In a later guide I will cover Without Enrollment where you can protect data in Enterprise apps (such as outlook) without being MDM enrolled.
Next, there are two sections related to Apps.
- Allowed apps – These are the apps that must adhere to the policy
- Exempt apps – These apps are exempt from the policy and can access enterprise data freely.
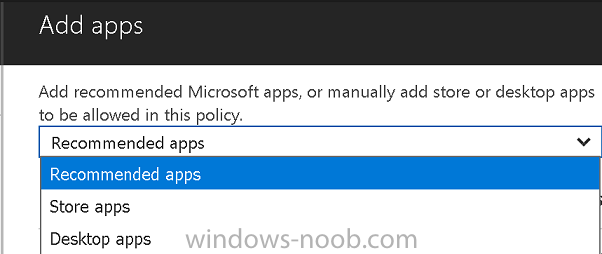
Click on Allowed apps and then click on Add apps to add one or more apps that you want to adhere to the policy. There’s a drop down with Recommended apps selected as default and those apps are listed below the drop down. If you want to add your own Store apps or Desktop apps manually then you’ll need to select the appropriate option and fill in the blanks.
- Recommended apps: a pre-populated list of (mostly Microsoft Office) apps that allow admins easily import into policy.
- Store apps: Admin can add any app from the Windows store to policy.
- Windows desktop apps: Admin can add any traditional Windows desktop apps to the policy (e.g. exe, dll, etc.)
To get information about how to generate the info needed for manually adding Store and Windows desktop apps see this post.
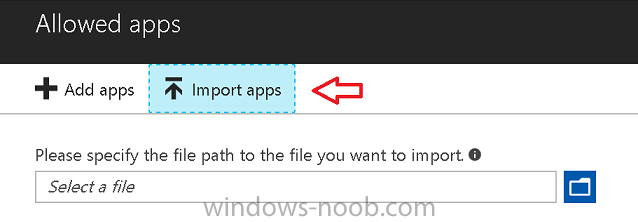
You can also import apps from an XML file generated in AppLocker by clicking on Import Apps. But before doing so you’ll need to create an AppLocker policy and then export the policy. To create an AppLocker policy follow this advice. To export an AppLocker policy to an XML file do as follows:
- Click Start, type secpol.msc in the Search programs and files box, and then press ENTER.
- In the console tree, expand Application Control Policies, right-click AppLocker, and then click Export Policy.
- Browse to the location where you want to save the XML file.
Below you can see the process of selecting some apps from the list of the Recommended apps.
Next you might want to exempt some apps from this WIP policy, to do so click on Exempt apps and add apps the same way as you did above except this time select those apps that you do NOT want the WIP policy to apply to.
Read the rest of this post @ windows-noob.com here