Introduction
If you are using my Windows 10 UEFI FrontEnd HTA to encrypt UEFI devices when installing Windows 10, and if you are using the MBAM 2.5 SP1 hotfix 2 to enable support for XTS-AES encryption, then you might have noticed a problem getting the recovery key into MBAM 2.5 SP1 when using either XTS 128 or XTS 256 encryption algorithms.
Problem
When doing a new computer install of Windows 10 1607 using System Center Configuration Manager (Current Branch) with an MBAM 2.5 SP1 backend, you may notice that if either the XTS 128 or XTS 256 encryption algorithms are selected in the HTA, that the BitLocker recovery key never makes it into the MBAM database, and that means you cannot do a refresh.
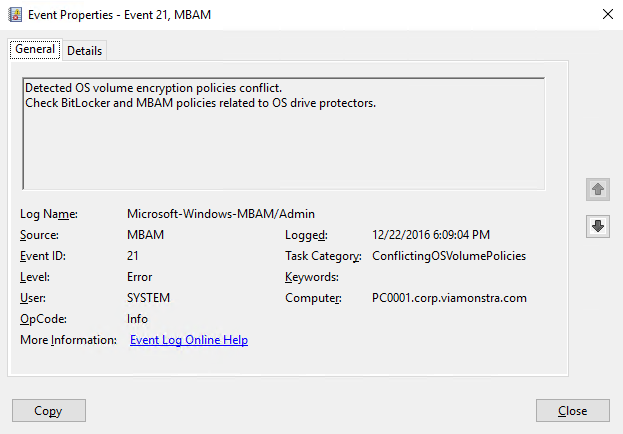
The device is encrypted but MBAM reports Event ID 21 in Event Viewer which basically means that the detected Operating System volume encryption policies are conflicting with each other.
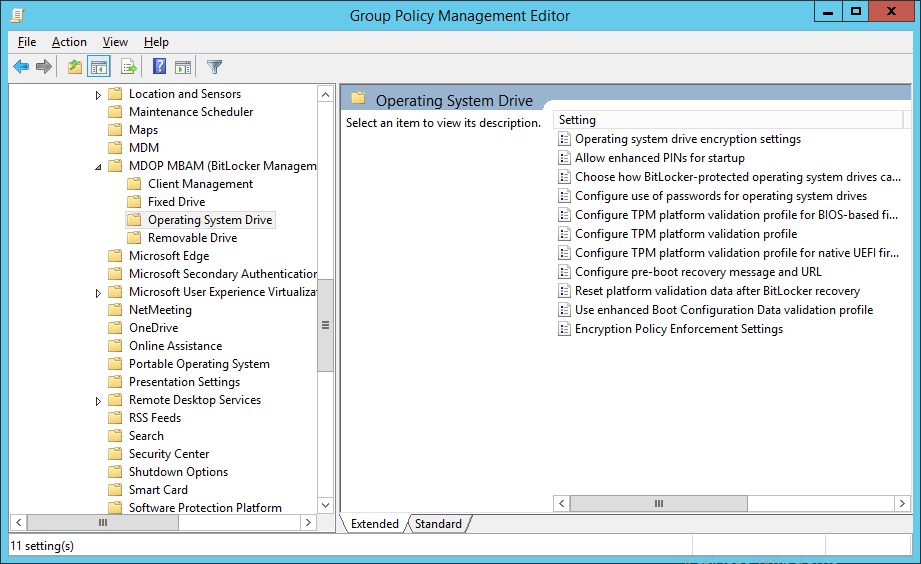
Here’s the actual MBAM GPO’s for Operating System Volume.
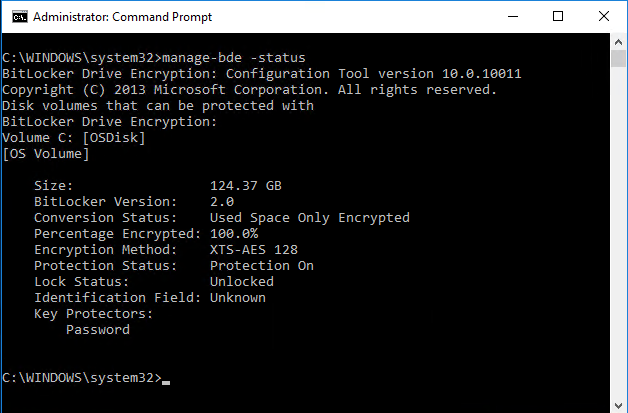
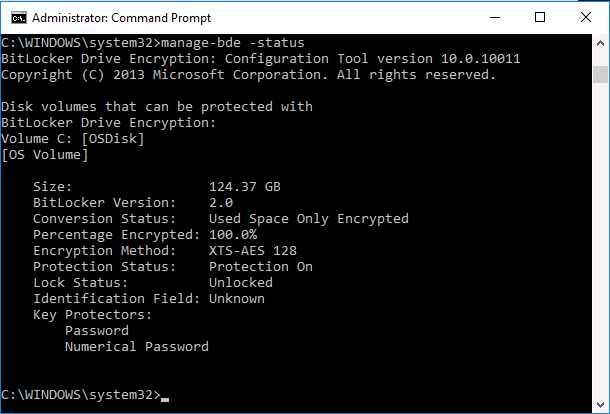
In addition to this error, when doing manage-bde -status you see something like the following:
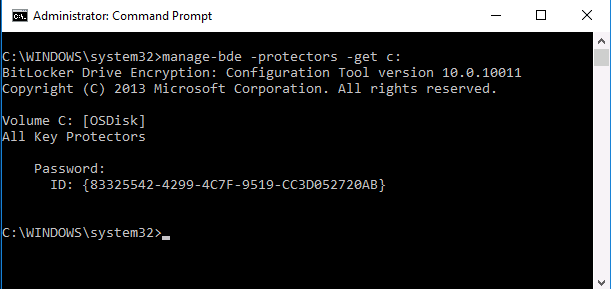
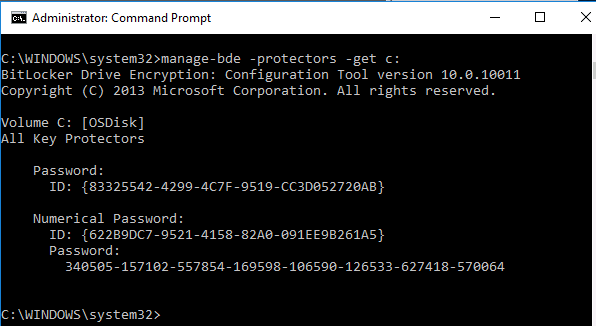
and manage-bde -protectors -get c: will also look like it’s missing info
This problem does not occur with either of the AES encryption algorithms.
Solution
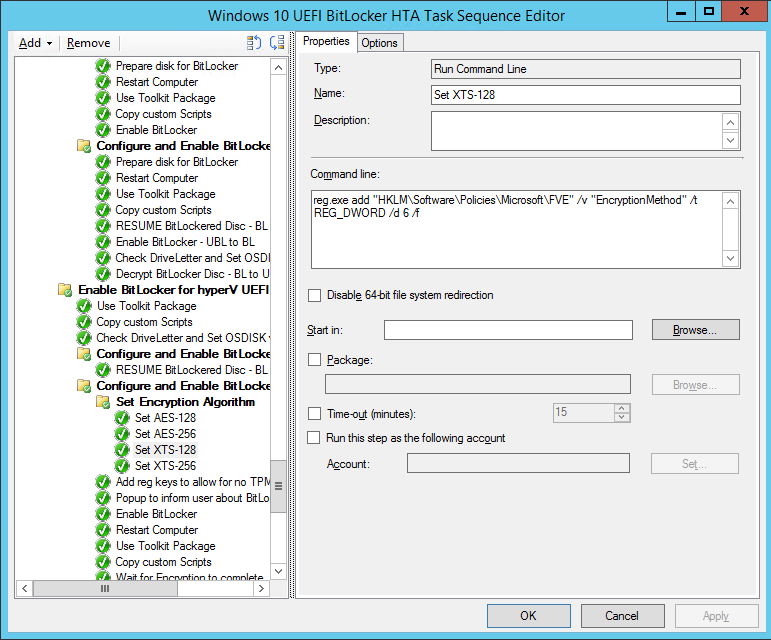
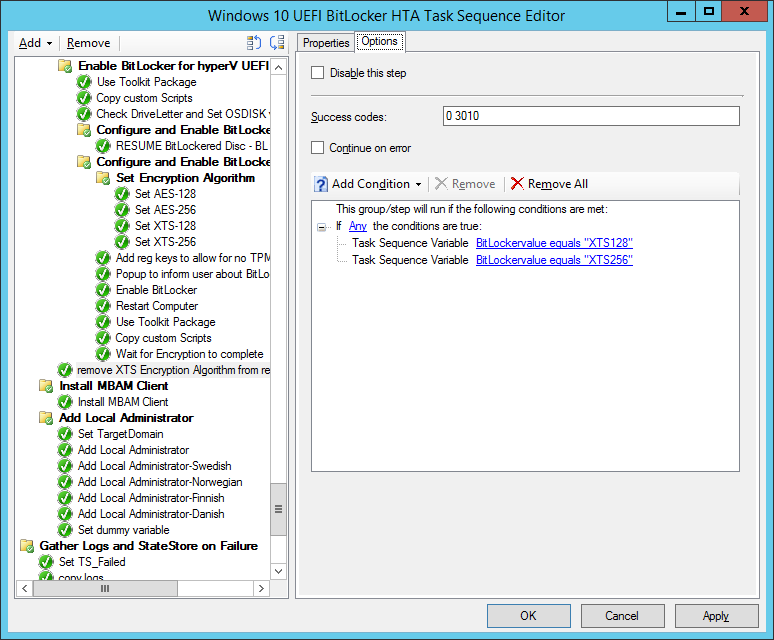
The problem was that the Group Policy settings for MBAM were conflicting with the registry settings used in the FrontEnd HTA to force the XTS encrytpion method before Enabling BitLocker after the task sequence is done laying down the Operating System. Here’s where those steps take place.
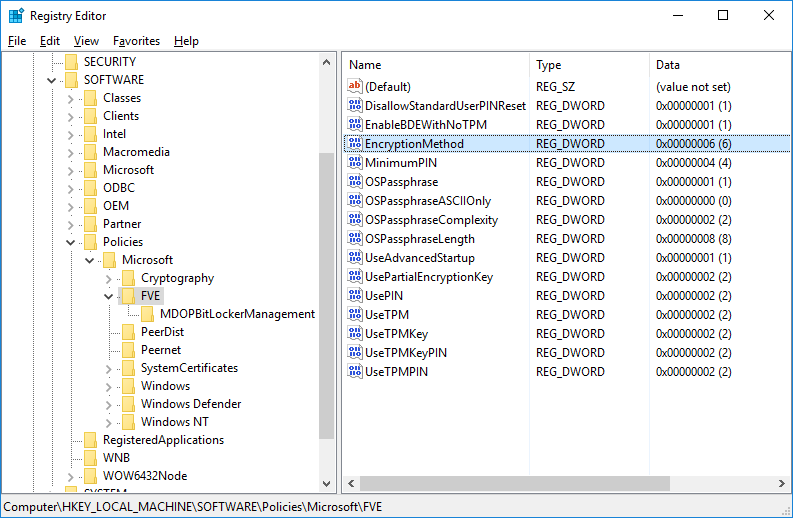
To resolve this, simply delete the following registry key HKLM\Software\Policies\Microsoft\FVE\EncryptionMethod shown below:
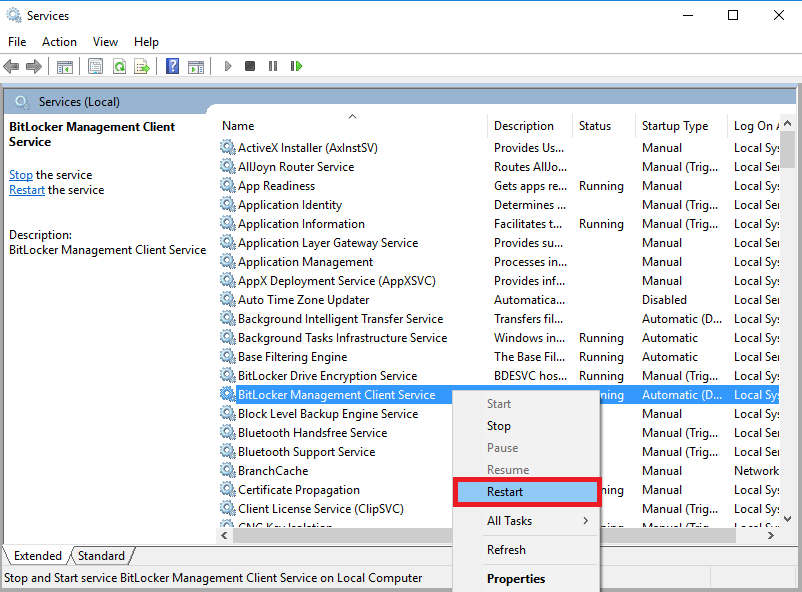
and then restart the MBAM Client agent service (note: to speed up this process you can use NoStartupDelay.reg in the lab)
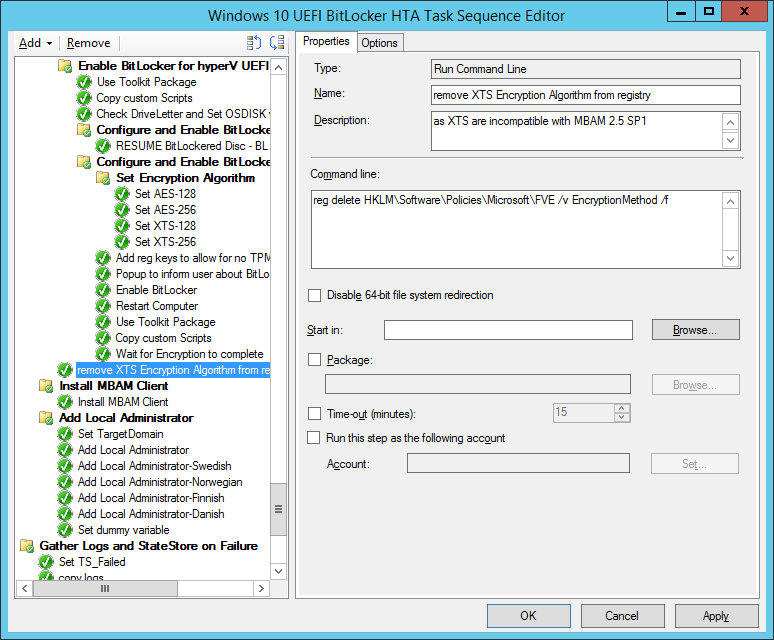
To automate this add a run command line step in the task sequence that does the following:
The command used in that step is:
reg delete HKLM\Software\Policies\Microsoft\FVE /v EncryptionMethod /f
where the options for that step are like so:
After doing the above you’ll see that the manage-bde -status outputs more details (like Numerical Password) such as below:
and the manage-bde -protectors -get c: output…
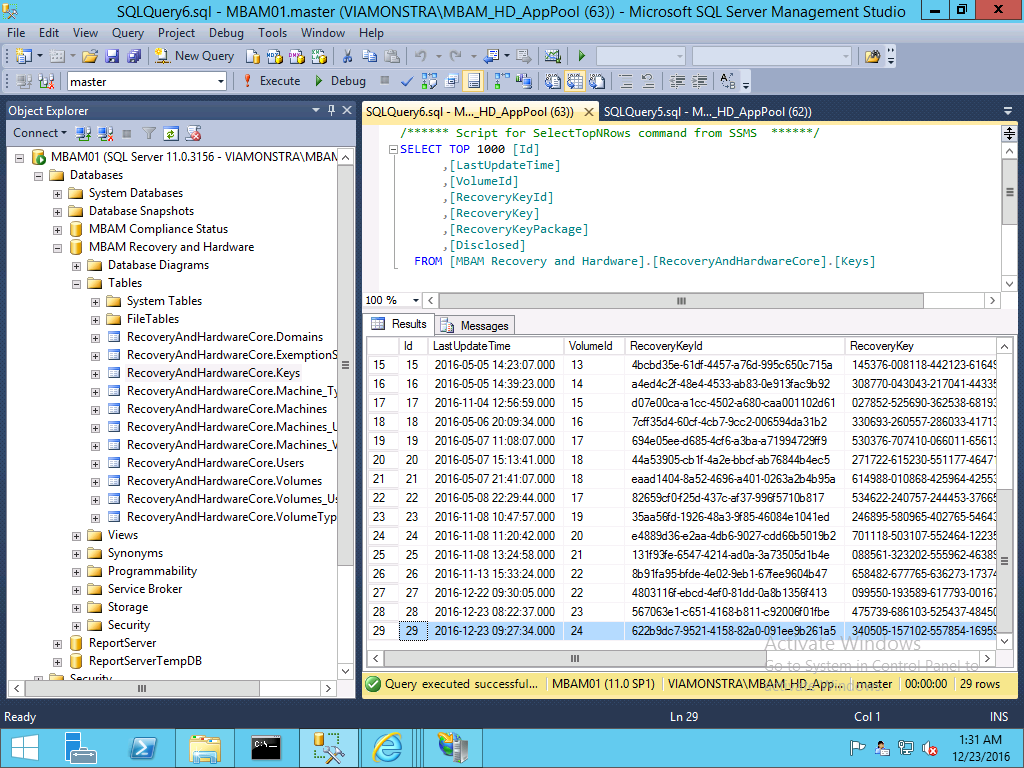
and of course, the MBAM key is now correctly stored in MBAM’s database



Pingback: Introducing the Windows 10 UEFI BitLocker Frontend for System Center Configuration Manager (Current Branch) | just another windows noob ?