Introduction
Previously I blogged about patching my Windows Server 2022 boxes using a PowerShell script from Microsoft in order to install a security patch. You can read all about that here.
That fix is a manual one and it applies to both Windows 10 version 21H2 and Windows 11 version 21H2 (in addition to Windows Server 2022). I wanted to verify if Windows Autopatch could do some magic, or in the worst case, simply report back the failure to apply the patch.
Why do I want to do this ? well if you look at the official docs from Microsoft about What is Windows Autopatch and focus on this line here with the green arrow, I’m hoping that in some way it’ll do some magic to keep security updated, although I understand that this particular patch is a special case scenario, but let’s see what happens anyway!
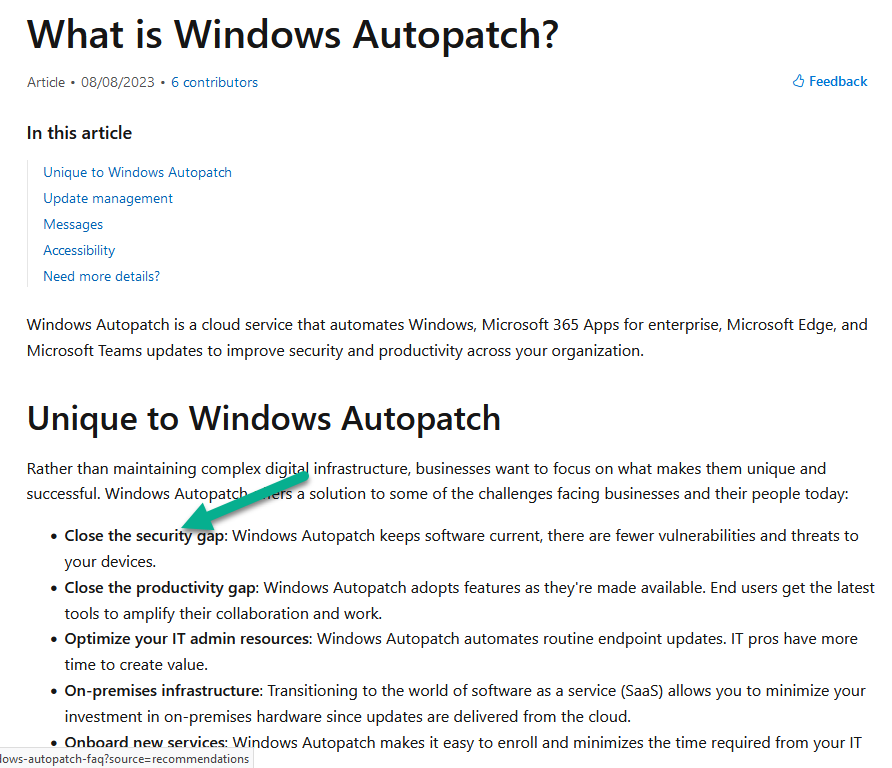
So that’s what this blog post is about, if you want a quick brush up about Windows Autopatch check this earlier blog post from myself & Paul here.
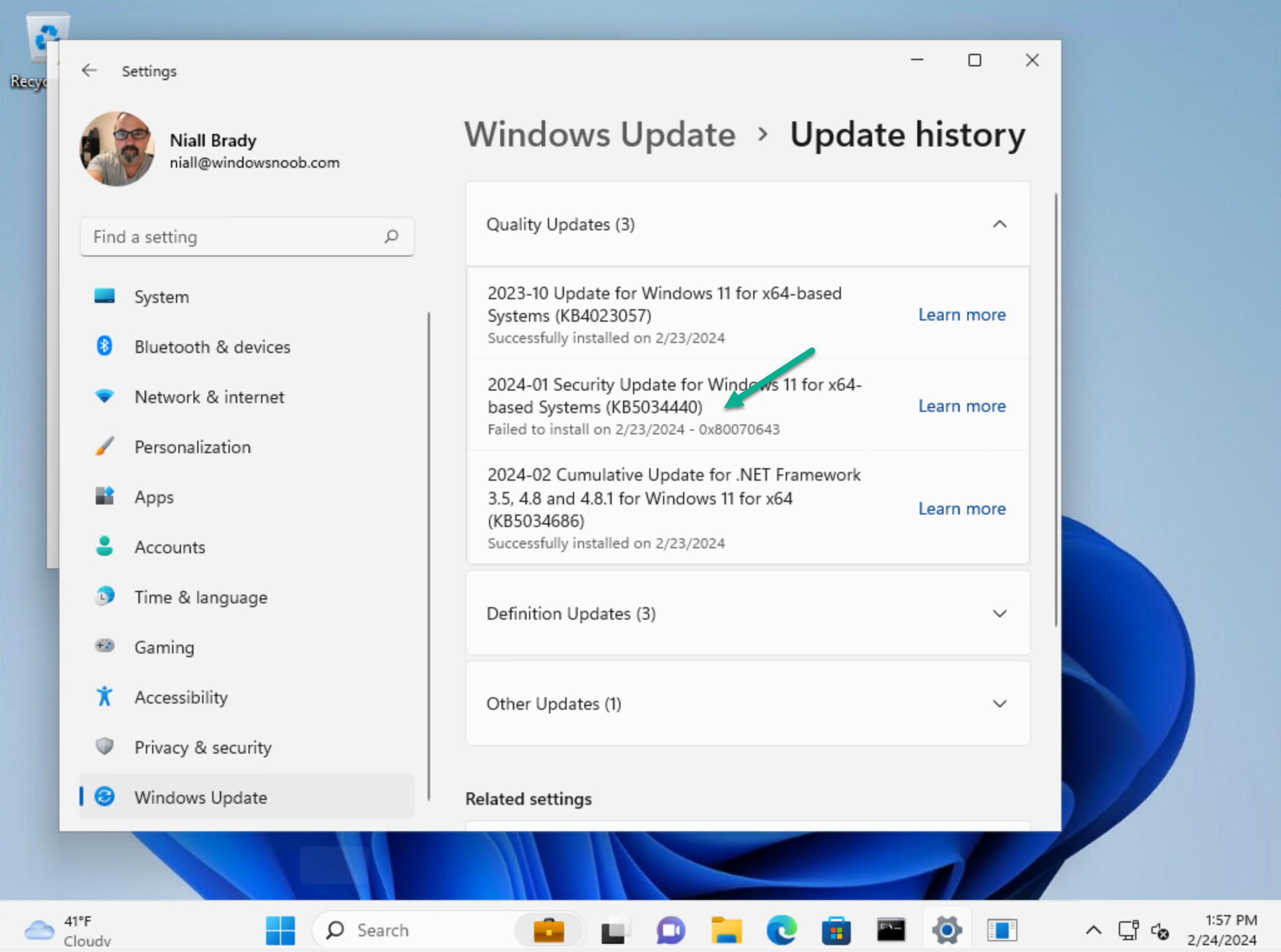
To start off with, I installed a Windows 11 virtual machine with Windows 11 version 21H2 and let windows update patch it to a current release prior to this security patch. I did not yet add it to the Windows Autopatch service.
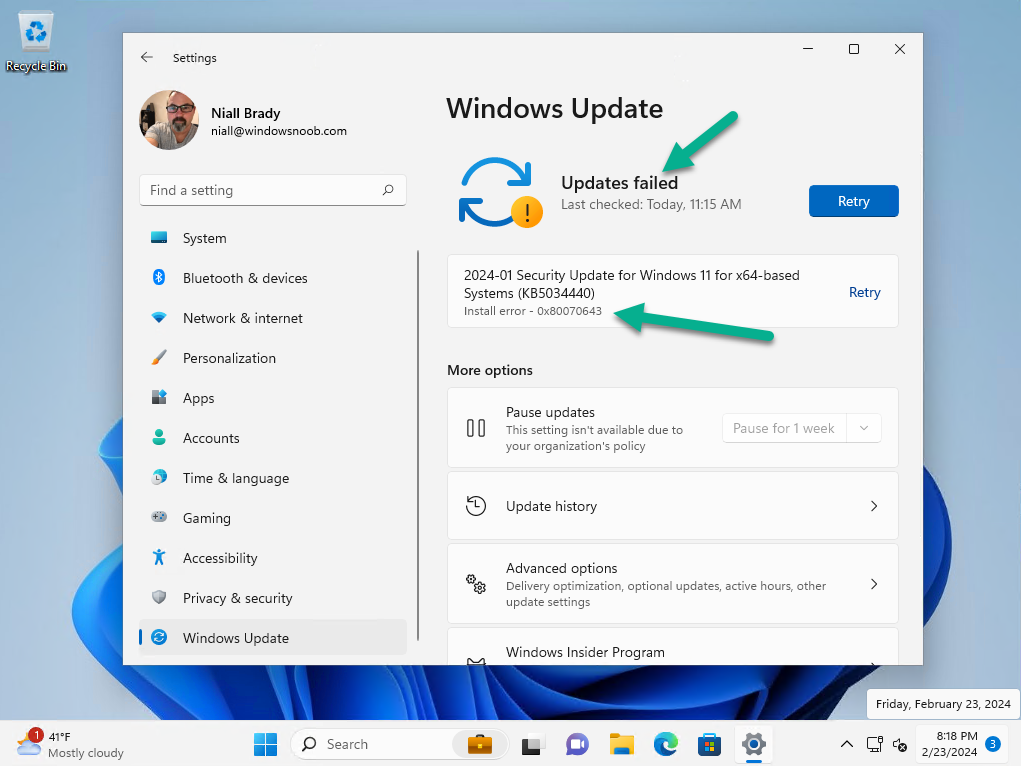
Next I confirmed it had the problem, and it did, as you see here.
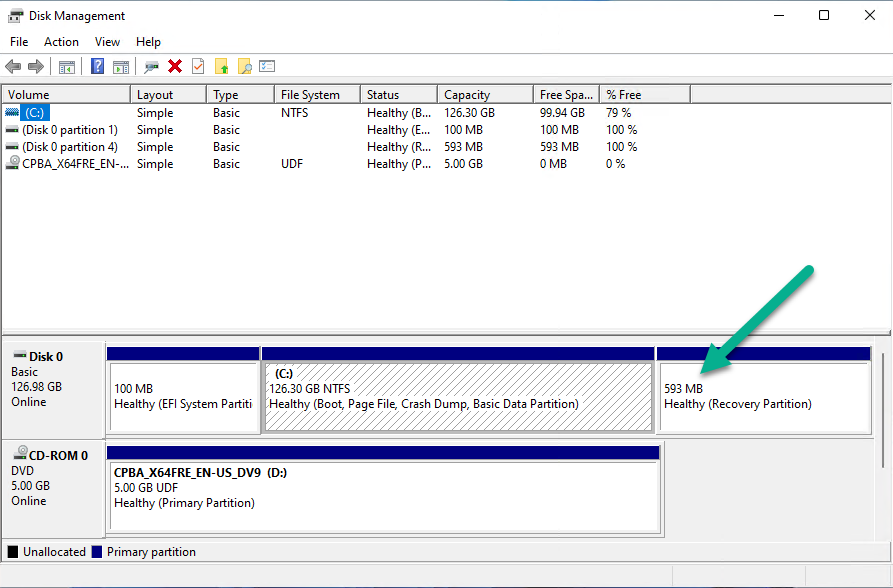
in addition, I verified the size of the Windows Recovery partition on this device. And there you see it’s only 593MB.
OK, so now we know we have a device with the ‘problem’, let’s add it to the Windows Autopatch service and see what if anything happens.
Adding the device to Windows Autopatch
To do that, I added it to the Windows Autopatch device registration group created when the service was setup originally.
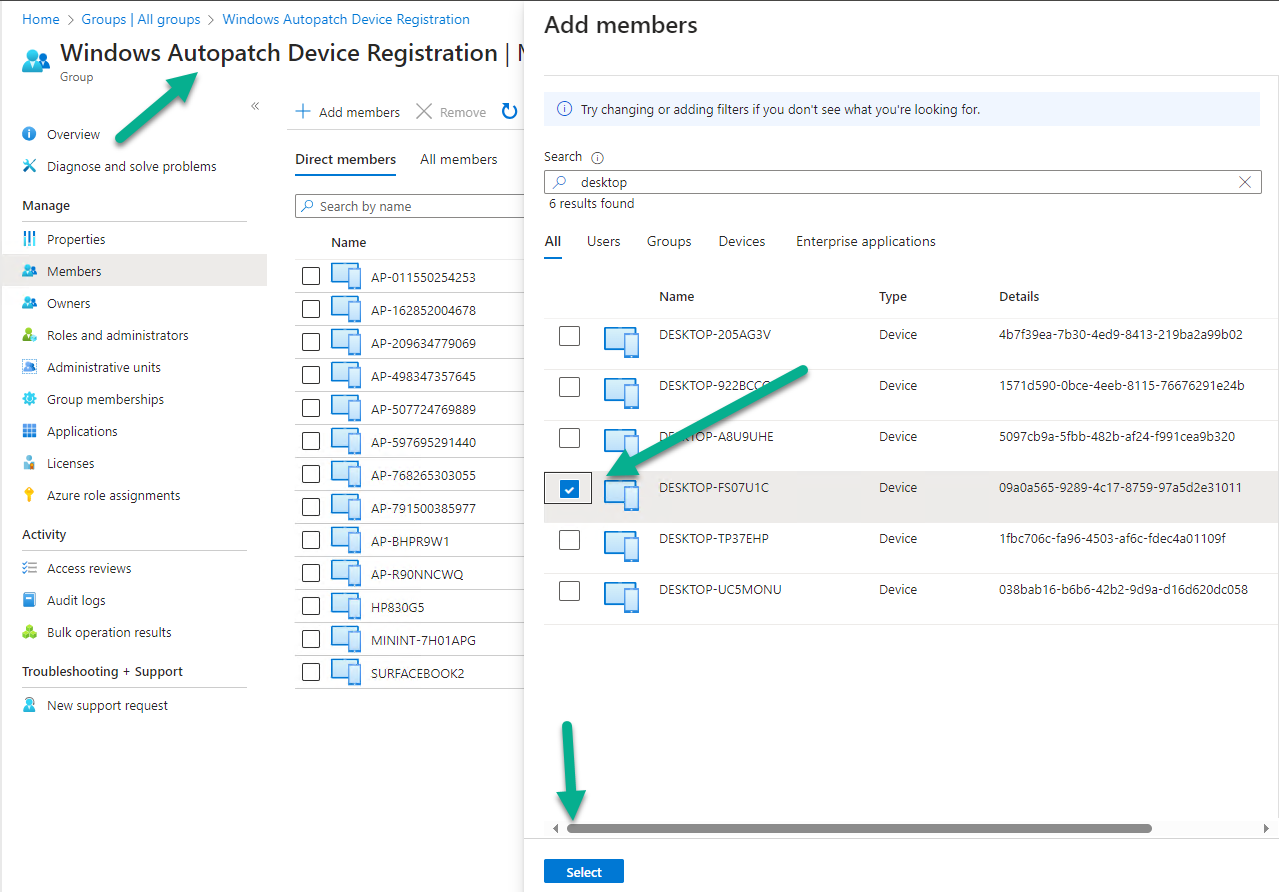
Next, I triggered a Discover devices (followed by Refresh) in the Windows Autopatch devices area until my virtual machine showed up.
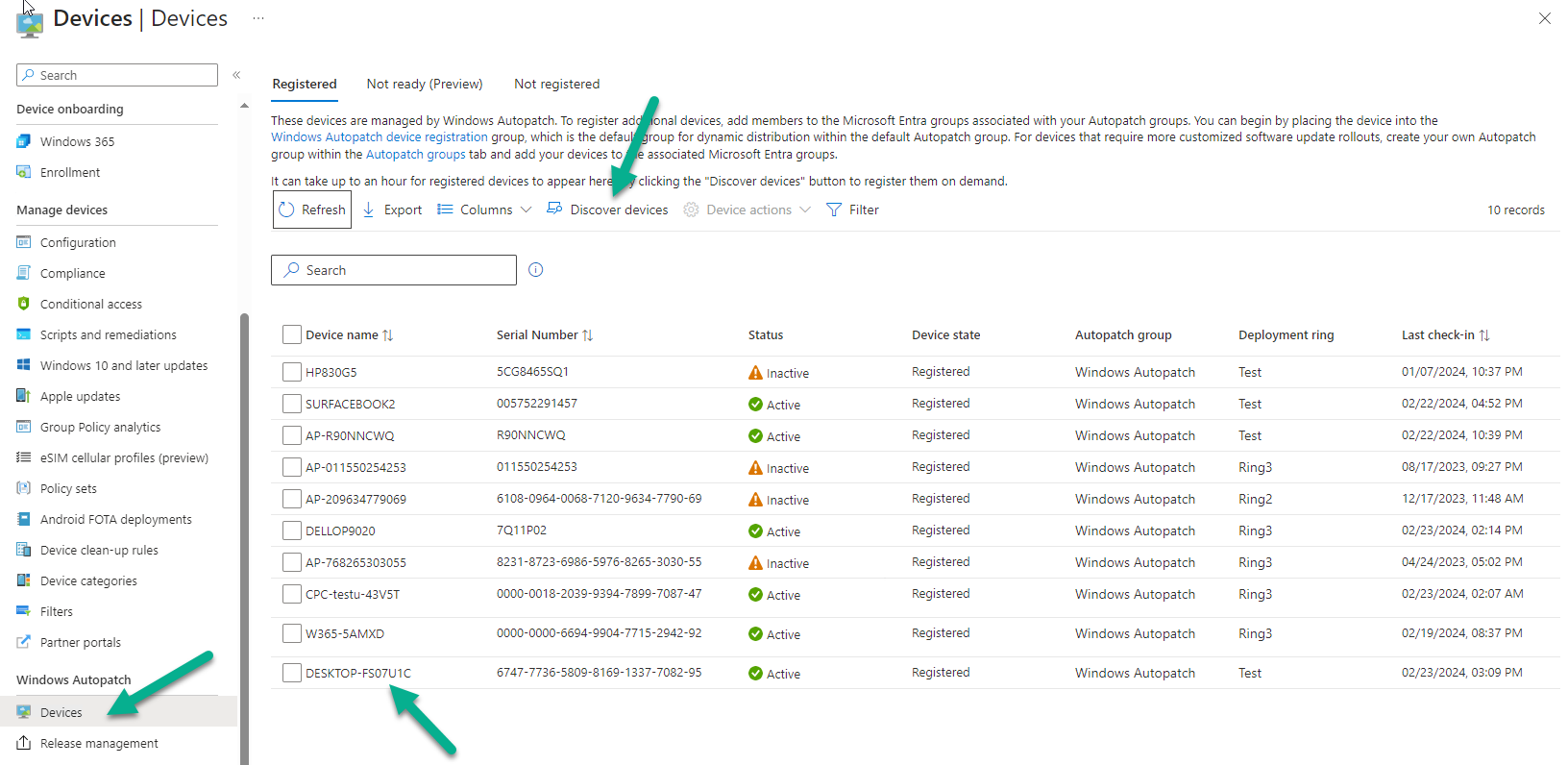
At this point I could see it in the service and it has the Windows Autopatch Test ring applied.
Next, I triggered a policy Sync on the device in Intune.
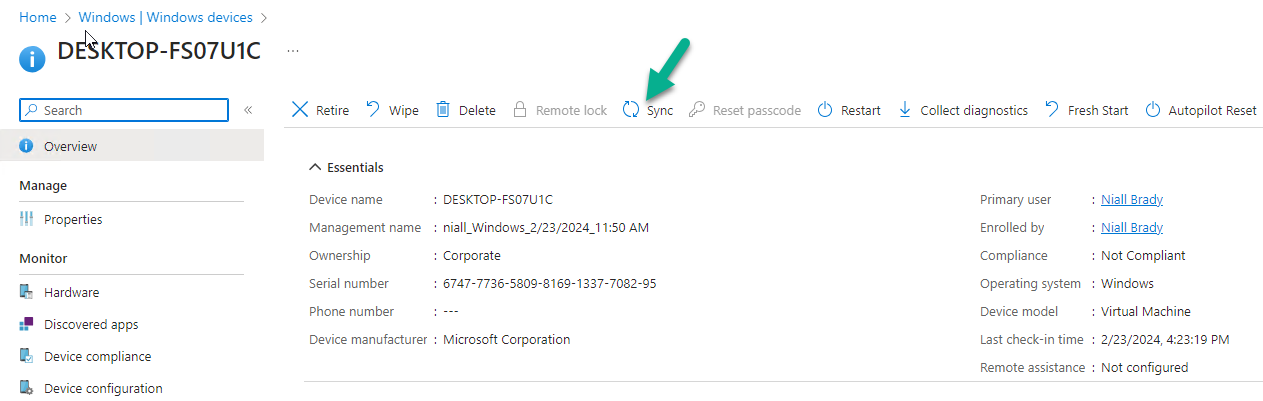
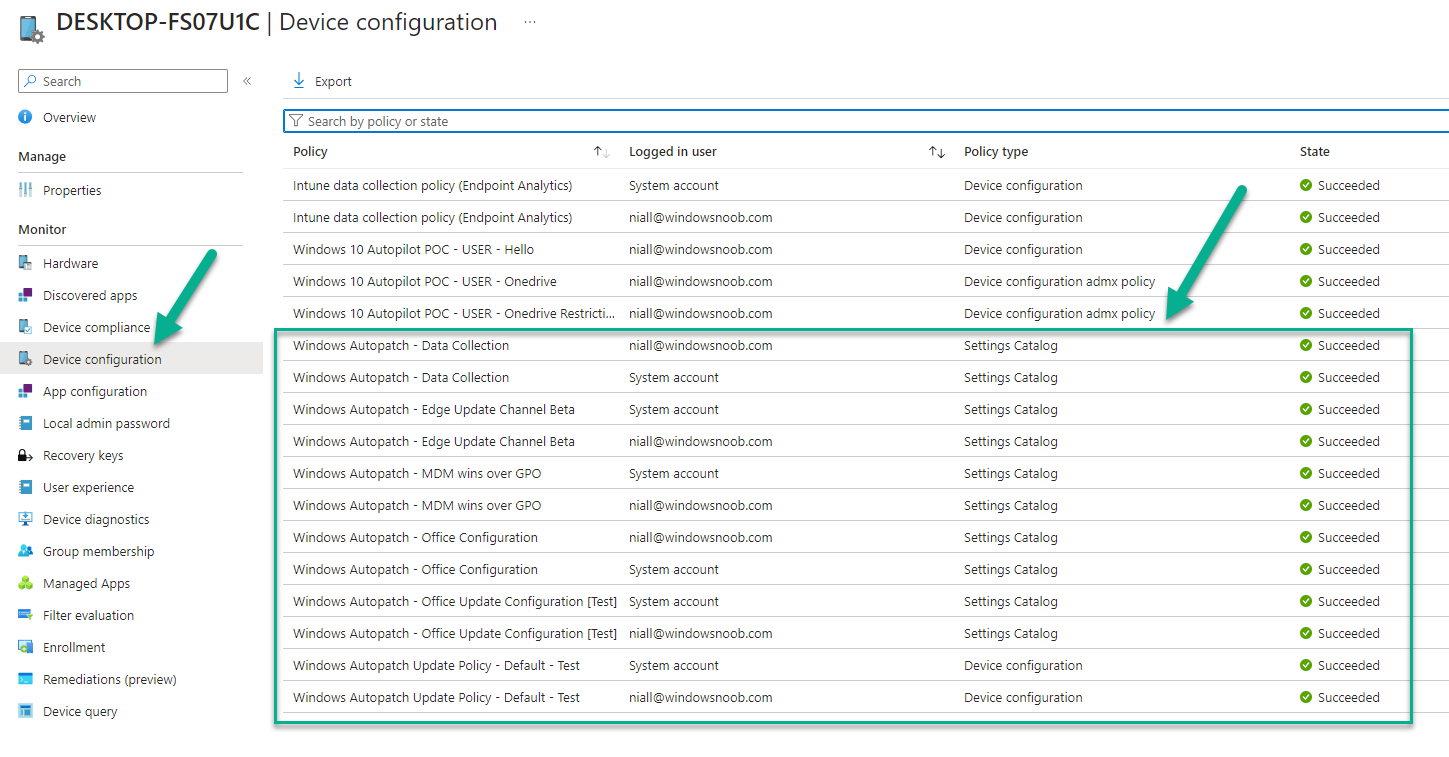
before verifying that it had the Windows Autopatch policies applied successfully.
Reporting
So all good from a Windows Autopatch perspective. What next ? After triggering some more policy Syncs I checked the reports in Windows Autopatch.
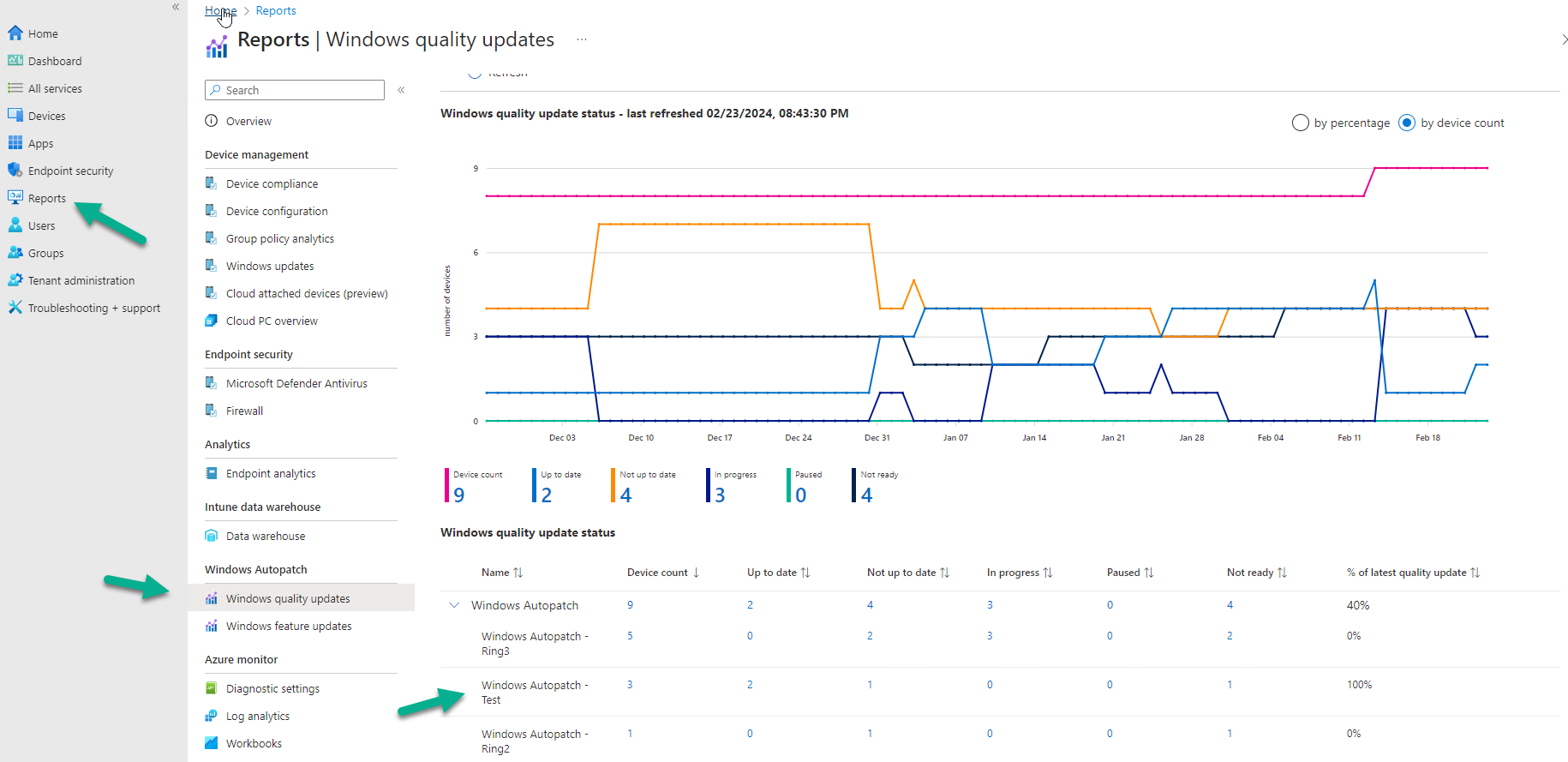
But that didn’t even show my newly added device.
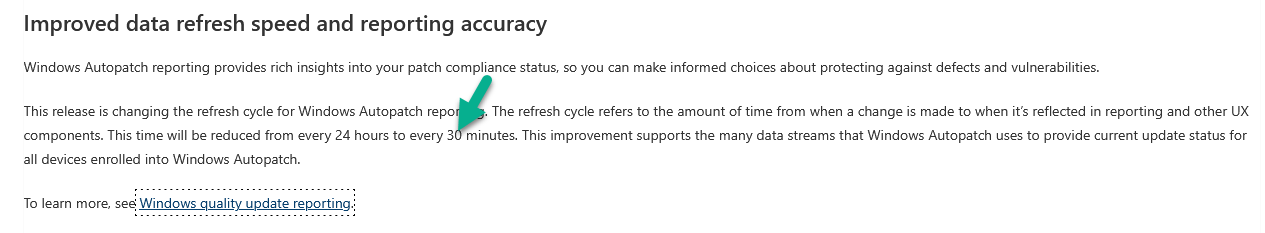
According to What’s new in Windows Autopatch for Februrary 2024 (that’s now in case you are reading this in the future), the reporting timescale and accuracy has been improved from 24 hours down to 30 minutes, and that is fantastic. I guess that change just hasn’t rolled out to my tenant yet.
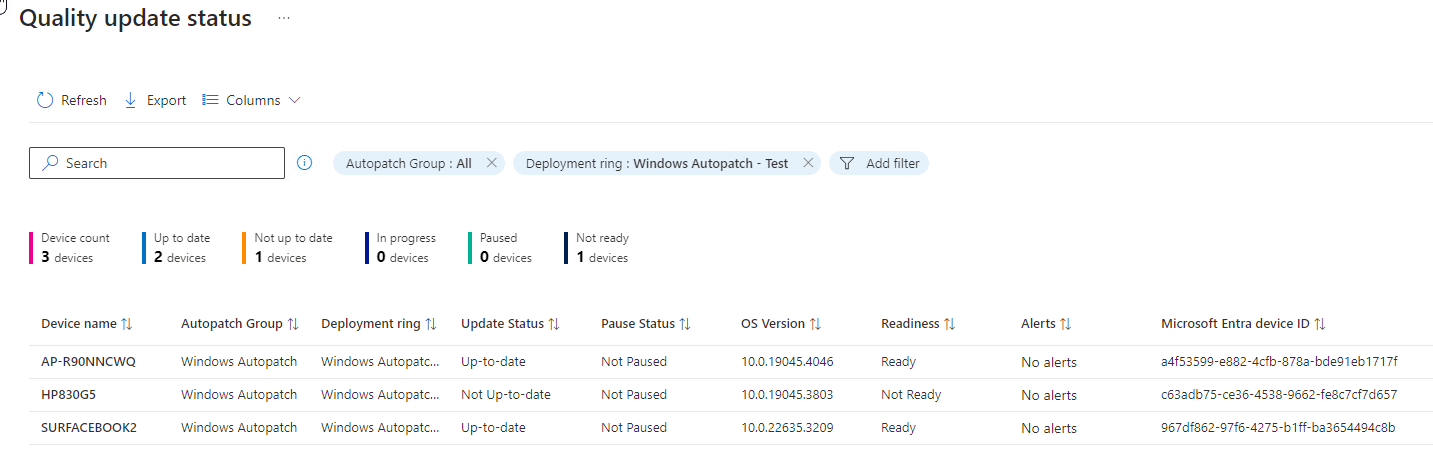
After a good nights sleep I refreshed the report and my computer showed up.
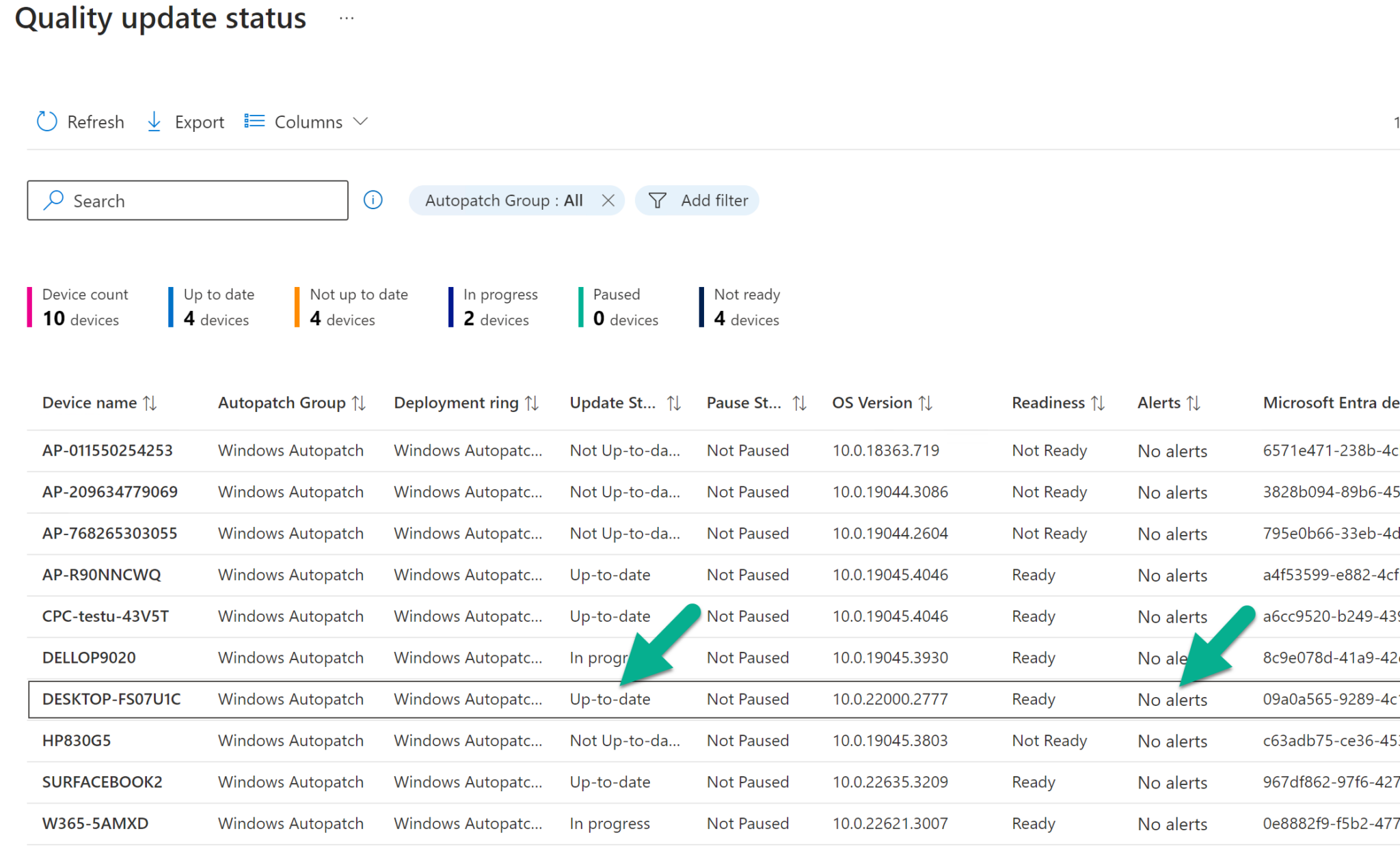
Unfortunately it didn’t highlight the fact that this security update couldn’t install, so there’s room for improvement.
I’ve had an offline chat with a member of the Windows Autopatch team and this is something they are hopefully considering going forward.
until the next time, cya !
Related reading
- Getting started with Windows Autopatch
- Patching Windows Server 2022 with the WinRE security patch
- What is Windows Autopatch
- Whats new in Windows Autopatch February 2024
Summary
To be honest I didn’t expect Windows Autopatch to magically solve this rather complex problem, but I was at least a little bit hopeful.
Until next time, adios !



“Unfortunately it didn’t highlight the fact that this security update couldn’t install”
So did Autopatch then automatically install it and fix the issue? Seems not clear from the wording.
it did NOT automatically fix or install the Security Update, and not only that it didn’t even report the fact that the update is failing to install