Introduction
Windows Autopilot preprovisioning (WhiteGlove) is the ability to pre-stage content and policies to devices while it’s been installed in the factory. We had a challenge to speed up the overall compliance of Windows Autopilot devices and the obvious solution was to stage as much content as we could during pre-provisioning (WhiteGlove) but to also enable BitLocker encryption during that process, the only problem is that Microsoft don’t officially support BitLocker encryption during the WhiteGlove scenario as the recovery key information is only uploaded when a user logs in.
In our initial testing, encryption itself wouldn’t even start until the user logged in. Not so much of a problem for small content on the hard disc but what if you have hundreds of Gigabytes of data to encrypt which could potentially take hours to encrypt after the user has logged on. As BitLocker encryption is a common Compliance policy setting, this needed to be addressed. The challenge was to do the heavy lifting (pre-provisioning and encryption) during the WhiteGlove process and to only upload the key to Intune once the user actually enrolled the device. That need brought about this solution which is in 3 parts.
In Part 1 you configured your environment and added a Win32 app to enforce encryption during WhiteGlove provisioning leaving the device fully encrypted by BitLocker before the end user enrolls it. You saw how to initiate WhiteGlove provisioning and reseal the device. In this part you’ll add another Win32 App to upload the BitLocker recovery information to Intune after the user has enrolled the device and in particular completed Windows Hello For Business (WHFB) setup which occurs directly at the end of the enrollment.
To see the other parts in this mini-series see below:
- Encrypting devices during Windows Autopilot provisioning (WhiteGlove) – Part 1
- Encrypting devices during Windows Autopilot provisioning (WhiteGlove) – Part 2 <- you are here
- Encrypting devices during Windows Autopilot provisioning (WhiteGlove) – Part 3
The Win32 app in this part actually does a few things namely:
- creates a scheduled task which is triggered on an event id
- extracts a second script which does the following
- removes the BEK protector
- adds a numerical password protector
- uploads the recovery information to Intune
- *if the above is successful*
- removes the users local admin permissions
- adds a runonce regkey for the next login
- adds a reg key to show that all is completed
- deletes the scheduled task
- restart the computer to speed up BitLocker compliance with a 5 second warning
Step 1. Add the Win32 app
Next, using the latest version of the IntuneWinappUtil.exe app, create a Win32 app called Win.AP.CreateScheduledTask_Win.AP.WhiteGlove.UploadBitLockerKeyToIntune. The app is in the attached 7 ZIP file, use 7-Zip to decompress.
Note: Only logged on members of windows-noob.com can download this file.
WhiteGlove – Upload bitlocker key after user login.7z
Configure the app settings as follows:
Name: Win.AP.CreateScheduledTask_Win.AP.WhiteGlove.UploadBitLockerKeyToIntune
Program Install command: install.Win.AP.CreateScheduledTask_Win.AP.WhiteGlove.UploadBitLockerKeyToIntune.cmd
Program uninstall command: install.Win.AP.CreateScheduledTask_Win.AP.WhiteGlove.UploadBitLockerKeyToIntune.cmd
Install behavior: System
Device restart behavior: No specific action
Return codes:
0 Success
1707 Success
3010 Soft reboot
1641 Hard reboot
1618 Retry
Requirements
Operating system architecture: x64
Minimum operating system Windows 10 1903
Registry:HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\windows-noob\WhiteGlove
as per the screenshot below:
Detection rules
Rules format: Manually configure detection rules
Detection rules File: C:\Windows
File or folder: Installed_WhiteGlove_Bitlocker_key_uploader.txt
Detection method: File or folder exists
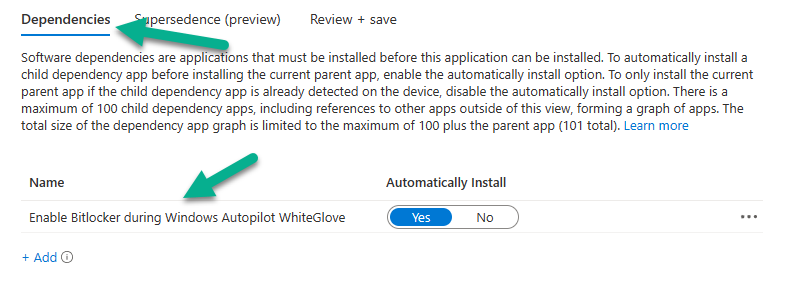
Next, configure the following Dependencies for the Win32 app
finally, assign the Win32 app as Required to our WhiteGlove Computers Azure ad group created in part 1.
Step 2. Enroll a provisioned device
Now that you’ve completed parts 1 and 2, you are ready to review what happens with the new Win32 app. After the user logs on, the ESP does it’s thing and starts Account Setup, during this phased the Windows Hello For Business (WHFB) setup starts. Once completed the end user will see something like this.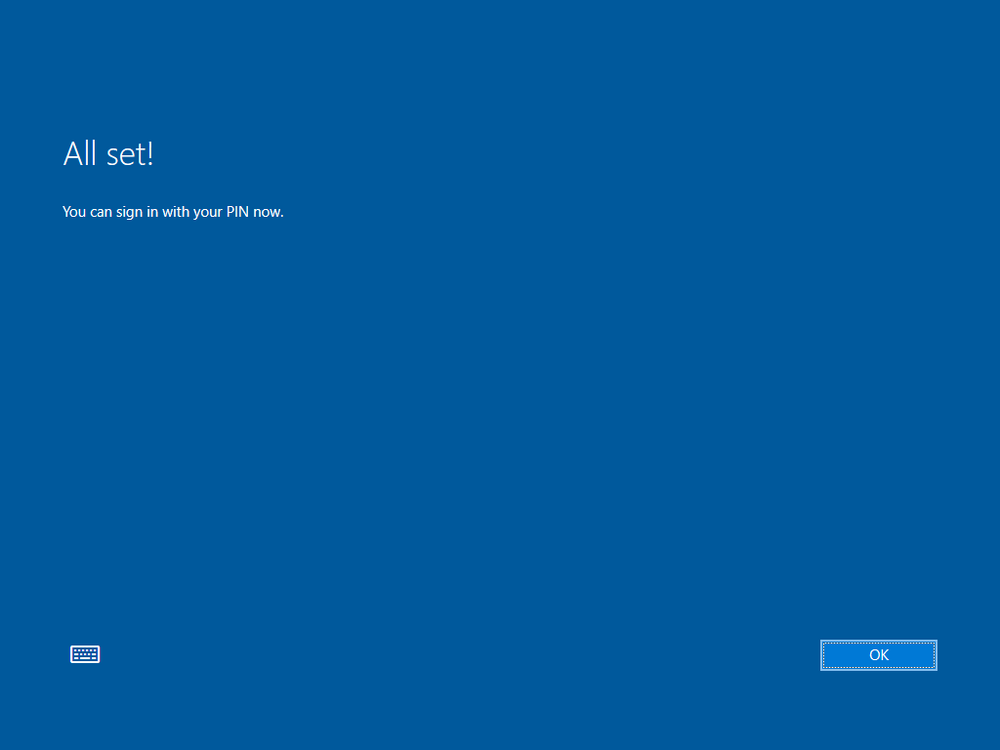
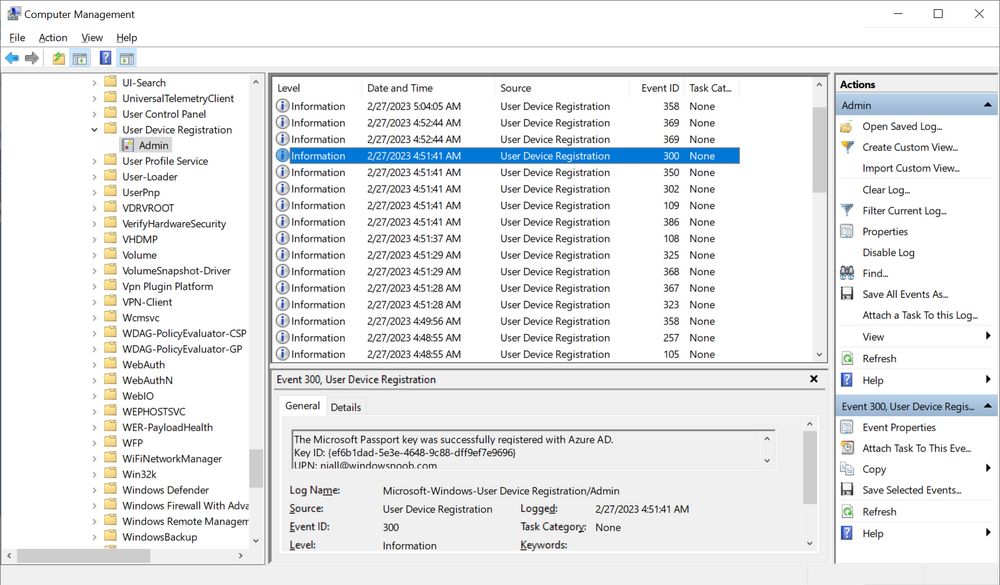
This generates an EventID (Microsoft-Windows-User Device Registration/Admin”>*[System[(EventID=300))
and that event ID triggers our scheduled task to run the associated win.ap.upload.bitlocker.key.after.whiteglove.vbs script which in turn launches the powershell script of the same name. That script does all the points mentioned above and then restarts the computer to enforce compliance quickly.
Troubleshooting
This Win32App creates some files which are extracted to C:\Windows\Temp. Review the log files for the generation of the Scheduled Task. Below is a reference log file, use it to compare to your attempts.
02/27/2023 04:49:16 Starting the 'Win.AP.CreateScheduledTask_win.ap.upload.bitlocker.key.after.whiteglove' version '0.16' script... 02/27/2023 04:49:16 Starting initial checks to determine if we should exit from the script if not... 02/27/2023 04:49:16 Logged on user method#1 detected as: 'AP-5CG03729P0\defaultuser0' 02/27/2023 04:49:16 Logged on user method#2 detected as: 'AP-5CG03729P0$' 02/27/2023 04:49:16 Looking for the following Regpath: 'HKLM:\Software\WOW6432Node\windows-noob\WhiteGlove\'... 02/27/2023 04:49:16 testing reg key 02/27/2023 04:49:16 returning true to reg key check 02/27/2023 04:49:16 The required WhiteGlove registry key was found, continuing script 02/27/2023 04:49:16 Found: 'EncryptedDuringWhiteGlove' 02/27/2023 04:49:16 Logged on user is: AP-5CG03729P0\defaultuser0 02/27/2023 04:49:16 extracting scripts to 'C:\Windows\Temp'... 02/27/2023 04:49:16 decoding BASE64 encoded file...win.ap.upload.bitlocker.key.after.whiteglove.ps1 02/27/2023 04:49:16 decoding BASE64 encoded file...win.ap.upload.bitlocker.key.after.whiteglove.vbs 02/27/2023 04:49:16 Creating windows-noob foldername... 02/27/2023 04:49:16 Creating scheduled task... 02/27/2023 04:49:18 Info: The scheduled task doesn't exist, will create it. 02/27/2023 04:49:18 DEBUG: Using the following values for the scheduled task: 02/27/2023 04:49:18 DEBUG: User: 'AP-5CG03729P0\defaultuser0' Time: '' Script: 'C:\Windows\Temp\win.ap.upload.bitlocker.key.after.whiteglove.vbs' Action: 'MSFT_TaskExecAction' Trigger: 'MSFT_TaskLogonTrigger' Settings: 'MSFT_TaskSettings3' Principal: 'MSFT_TaskPrincipal2' Foldername: 'windows-noob'. 02/27/2023 04:49:18 about to create the scheduled task... 02/27/2023 04:49:18 Succeeded in creating the scheduled task 02/27/2023 04:49:19 DEBUG: task=MSFT_ScheduledTask (TaskName = "Win.AP.WhiteGlove.UploadBitLockerKeyToI..., TaskPath = "\windows-noob\") taskName=Win.AP.WhiteGlove.UploadBitLockerKeyToIntune run=02/27/2023 04:50:18 02/27/2023 04:49:19 DEBUG: settings the scheduled task settings=MSFT_ScheduledTask (TaskName = "Win.AP.WhiteGlove.UploadBitLockerKeyToI..., TaskPath = "\windows-noob\") 02/27/2023 04:49:19 Exiting script.
Below is the log file from the which uploads the key
02/27/2023 04:51:48 Starting script: 'win.ap.upload.bitlocker.key.after.whiteglove' version: '0.14'... 02/27/2023 04:51:48 Checking logged on user to determine if we are still in the ESP or not. 02/27/2023 04:51:49 Not in ESP, will continue! 02/27/2023 04:51:49 Removing BEK... 02/27/2023 04:51:49 removing BEK protector 02/27/2023 04:51:51 DEBUG: BLV = 'C:' 02/27/2023 04:51:51 attempting to remove protector... 02/27/2023 04:51:52 succeeded removing protector! 02/27/2023 04:51:52 DEBUG: BLV = 'C:' 02/27/2023 04:51:52 Adding RK... 02/27/2023 04:51:52 adding recovery password... 02/27/2023 04:51:53 succeeded adding protector ! 02/27/2023 04:51:53 02/27/2023 04:51:53 about to upload key to Azure 02/27/2023 04:51:55 succeeded to upload the BitLocker recovery key to Azure ! 02/27/2023 04:51:55 removing user 'AzureAD\NiallBrady' from Local Admins group 02/27/2023 04:51:55 succeeded to remove the user from the group 02/27/2023 04:51:55 about to remove the Scheduled task 02/27/2023 04:52:00 Info: The 'Win.AP.WhiteGlove.UploadBitLockerKeyToIntune' scheduled task exists, removing the scheduled task... 02/27/2023 04:52:00 About to delete scheduled task: Win.AP.WhiteGlove.UploadBitLockerKeyToIntune 02/27/2023 04:52:01 Succeeded to remove scheduled task: Win.AP.WhiteGlove.UploadBitLockerKeyToIntune 02/27/2023 04:52:01 succeeded removing the 'Win.AP.WhiteGlove.UploadBitLockerKeyToIntune' scheduled task ! 02/27/2023 04:52:01 adding reg key to confirm key upload status 02/27/2023 04:52:01 Creating a RunOnce reg key to trigger intune sync 02/27/2023 04:52:01 succeeded to create the RunOnce registry key 02/27/2023 04:52:01 doing a mandatory shutdown/restart... 02/27/2023 04:52:01 succeeded to issue the shutdown command, will restart in 5 seconds! 02/27/2023 04:52:01 script completed...
That’s it !
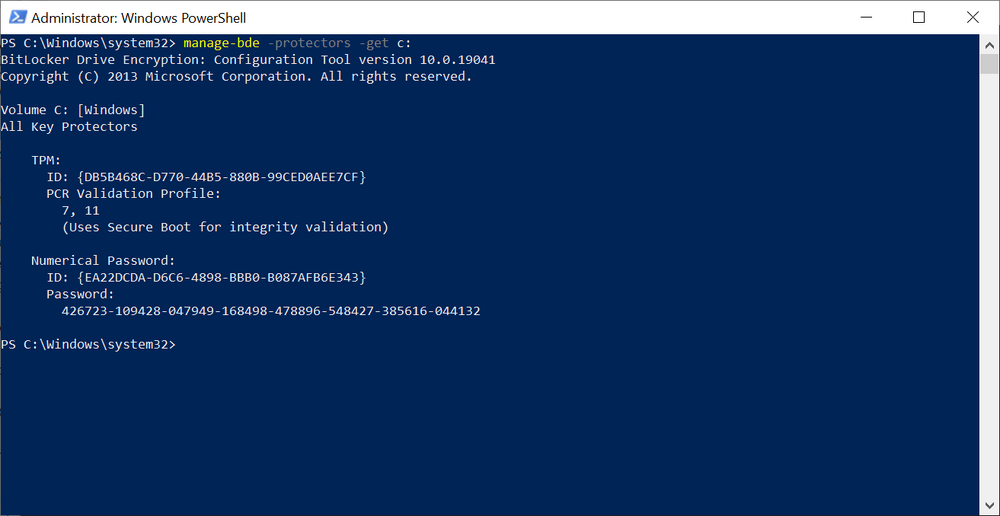
checking on the computer which was just enrolled we can determine the Protectors using
manage-bde -protectors -get c:
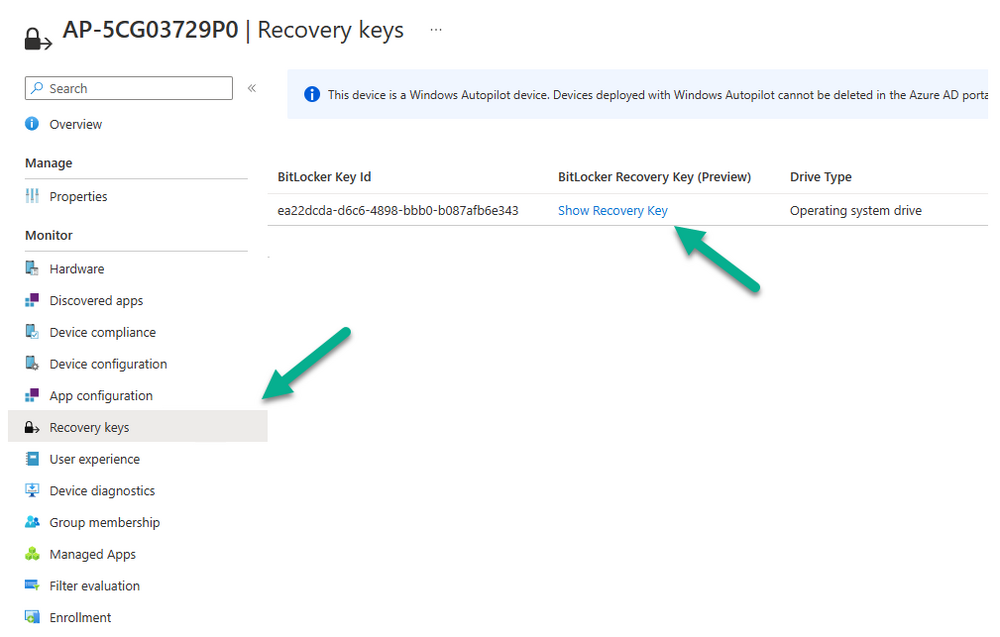
Checking in Intune we can see the key is uploaded, job done i’d say !
Please join me in part 3 where we’ll look at adding our successfully enrolled WhiteGlove computers into an Azure AD group to target them with additional policies (such as BitLocker) so that when the BitLocker recovery key is revealed in Intune or on the device, that the policy will rotate the key and upload it to Intune