Introduction
Microsoft released Technical Preview 2102 and it’s got a bunch of new updates as usual, including some updates for BitLocker Management via the cloud management gateway. To get some ideas about how BitLocker Management via a CMG works please see my blog posts below.
- BitLocker management via a cloud management gateway (CMG) in ConfigMgr 2010
- Improvements to BitLocker management in Endpoint Manager update 2010
In current branch version 2010, you can manage BitLocker policies and escrow recovery keys over a cloud management gateway (CMG). This support included a couple of limitations. Starting in this technical preview release, BitLocker management policies over a CMG support the following capabilities:
- Recovery keys for removable drives
- TPM password hash, otherwise known as TPM owner authorization
So Let’s take a look at the new BitLockers Management abilties on a newly deployed Surface. After I installed Windows 10 version 20h2 on it I disconnected it from the LAN and the ConfigMgr client agent switched over to a connection type property of Currently Internet as shown here.
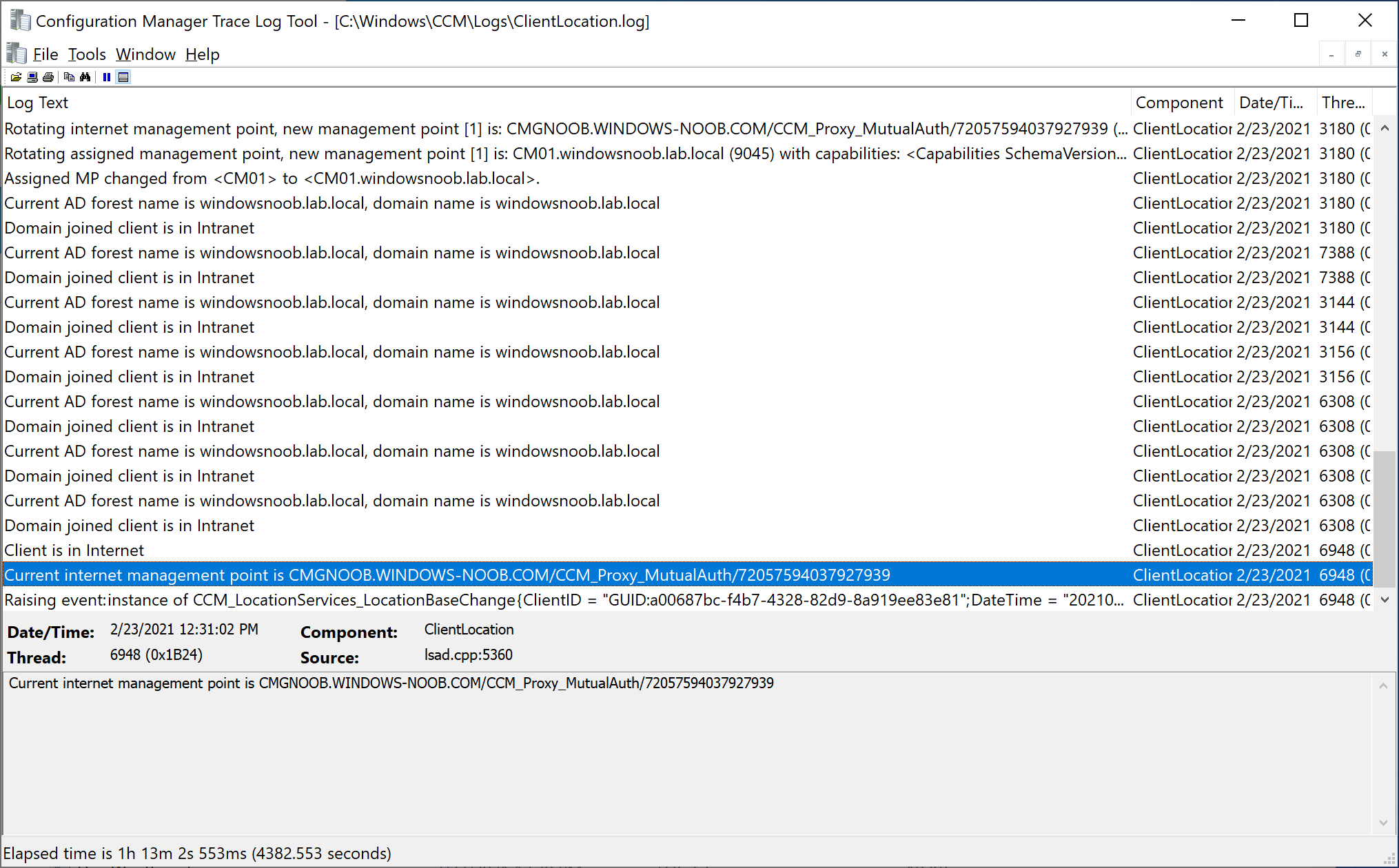
 And the switch from on-premises management to management via the CMG is seen in the ClientLocation.log as shown here.
And the switch from on-premises management to management via the CMG is seen in the ClientLocation.log as shown here.
This particular computer was not managed in relation to BitLocker Management as no policy was deployed to it. So I went ahead and created some new policy in the TP2102 console.
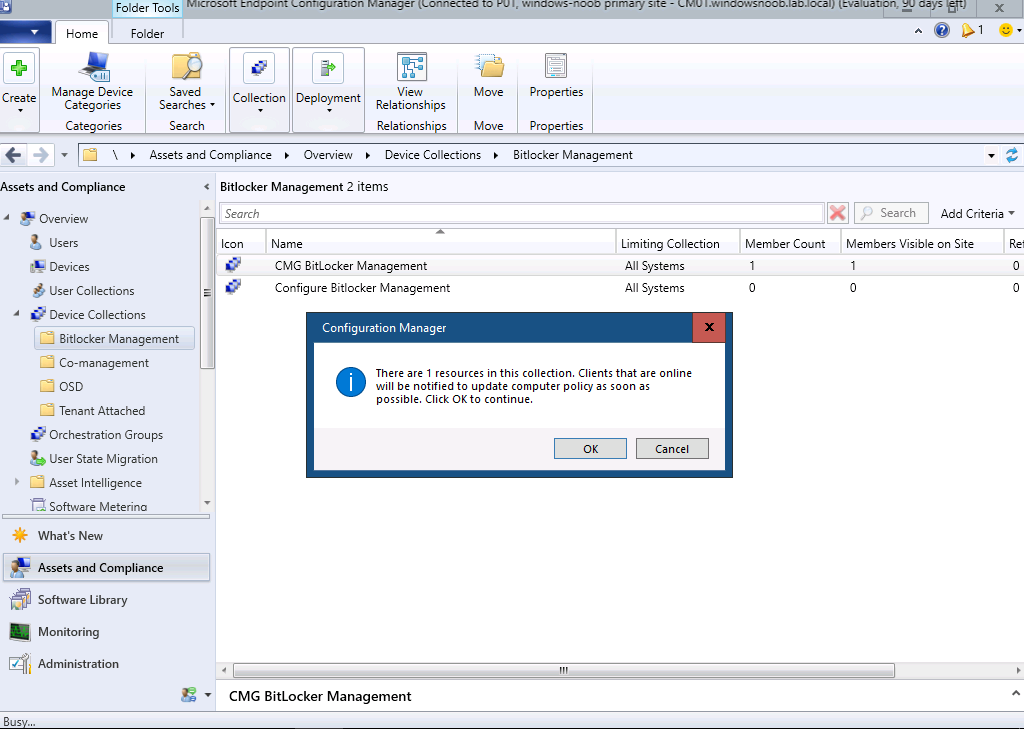
 Next, I added my newly deployed Surface to the CMG BitLocker Management collection, and triggered it to download machine policy.
Next, I added my newly deployed Surface to the CMG BitLocker Management collection, and triggered it to download machine policy.
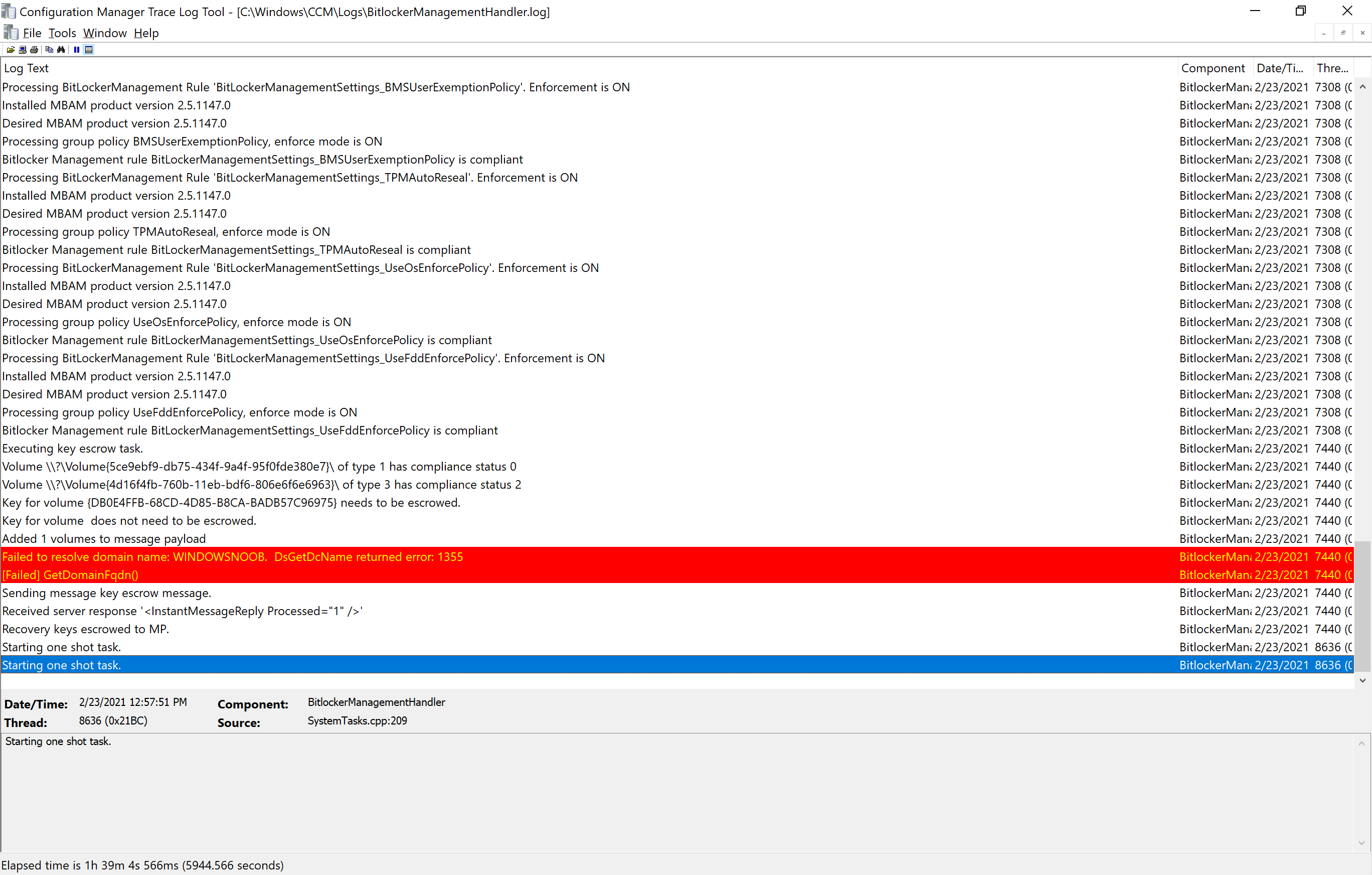
This computer has a removable drive attached (sd hc card). Within literally seconds the device got policy and the BitLockerManagmentHandler.log started reporting about recovery keys being escrowed to the management point (via the CMG). Notice the:
Starting one shot task
I haven’t seen that one before.
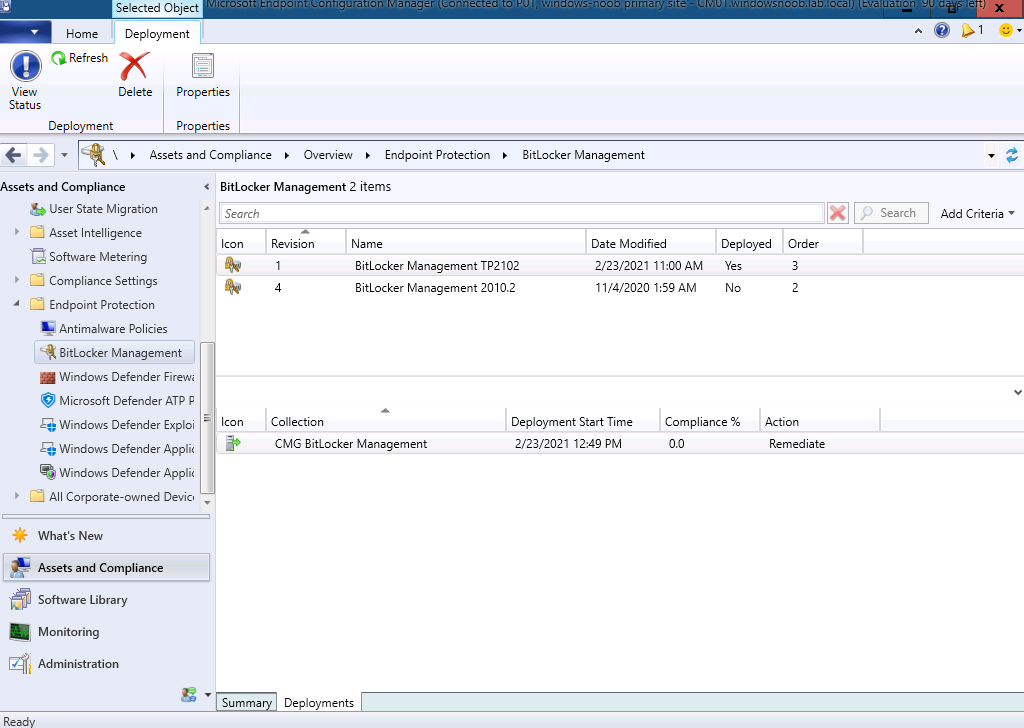
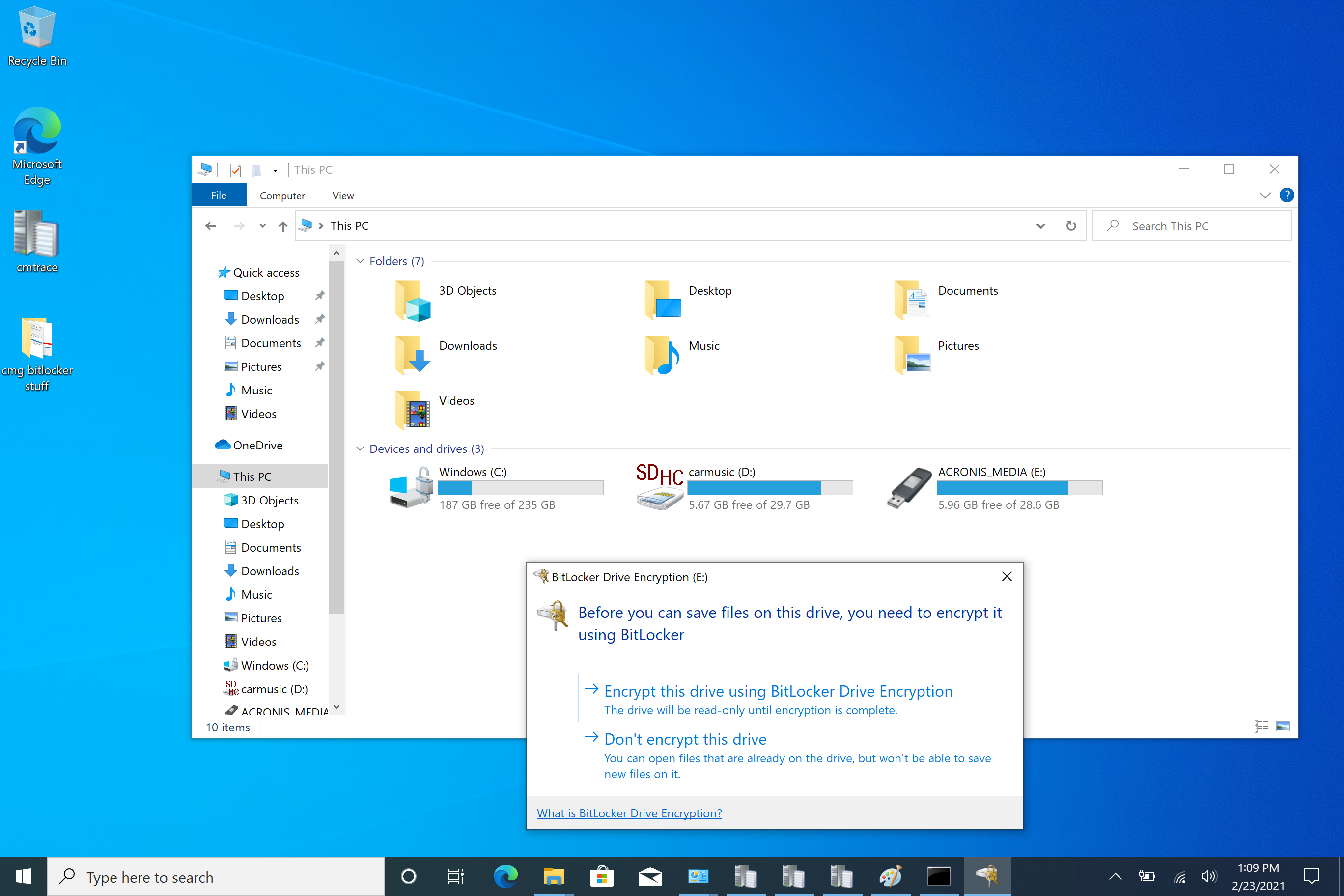
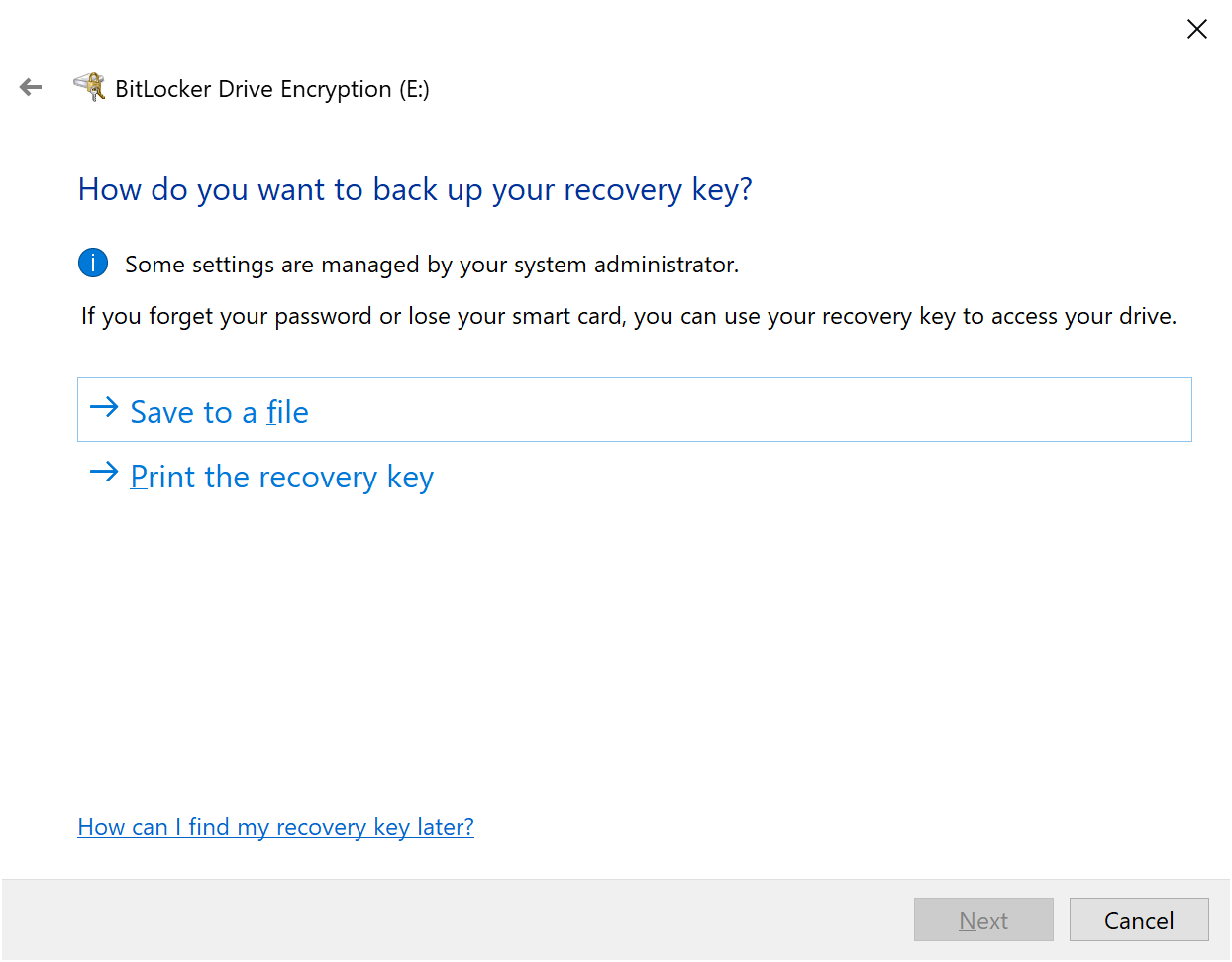
After inserting a usb key I got the following popup
I chose to encrypt and then it asked me for a password. I entered one and then it asked me where to store the keys, which was odd as I assumed they would be stored in the MP (via the CMG).
But, I selected Save to a file and then encryption started and the keys were escrowed to the MP via the CMG. Job done !
After encrypting the disc I ejected it, reinserted it and was informed to enter my password. I entered my password and I could freely browse the disc. I then tried to write to it and got the following message.
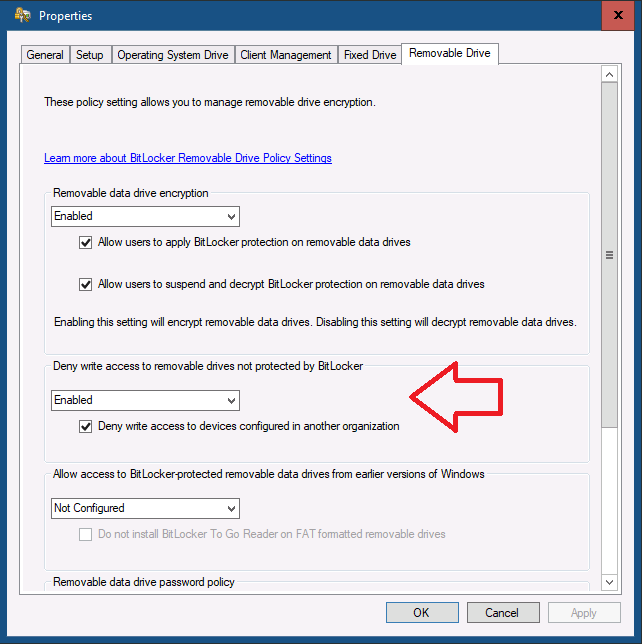
 This might be a mis-configuration on my part, I’ve asked Microsoft for comment. Here are my settings.
This might be a mis-configuration on my part, I’ve asked Microsoft for comment. Here are my settings.
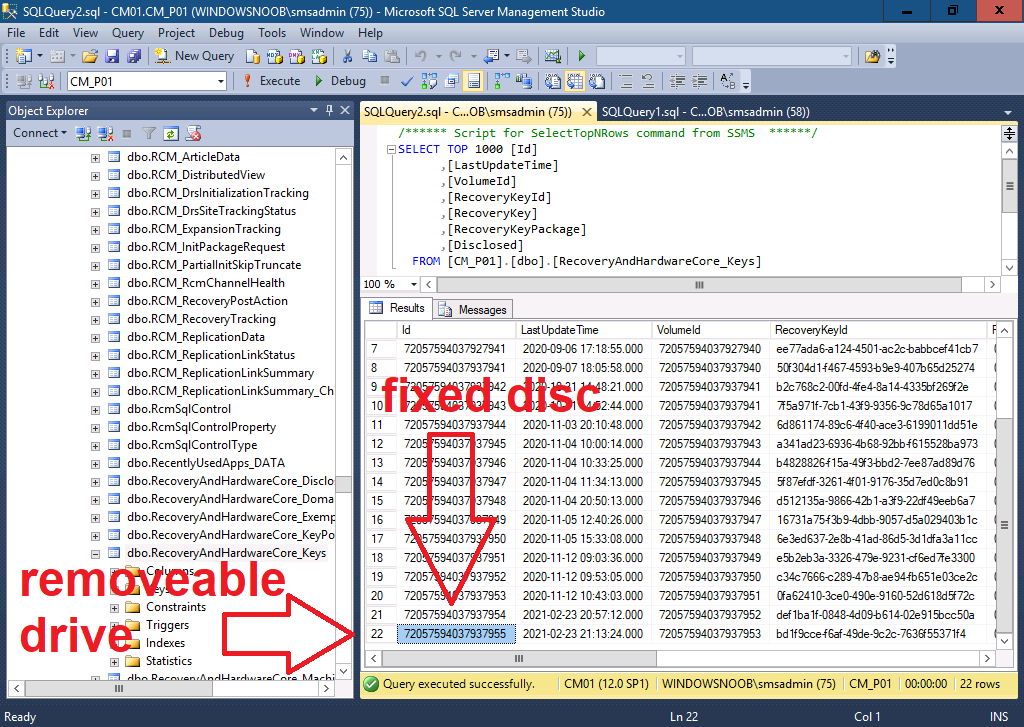
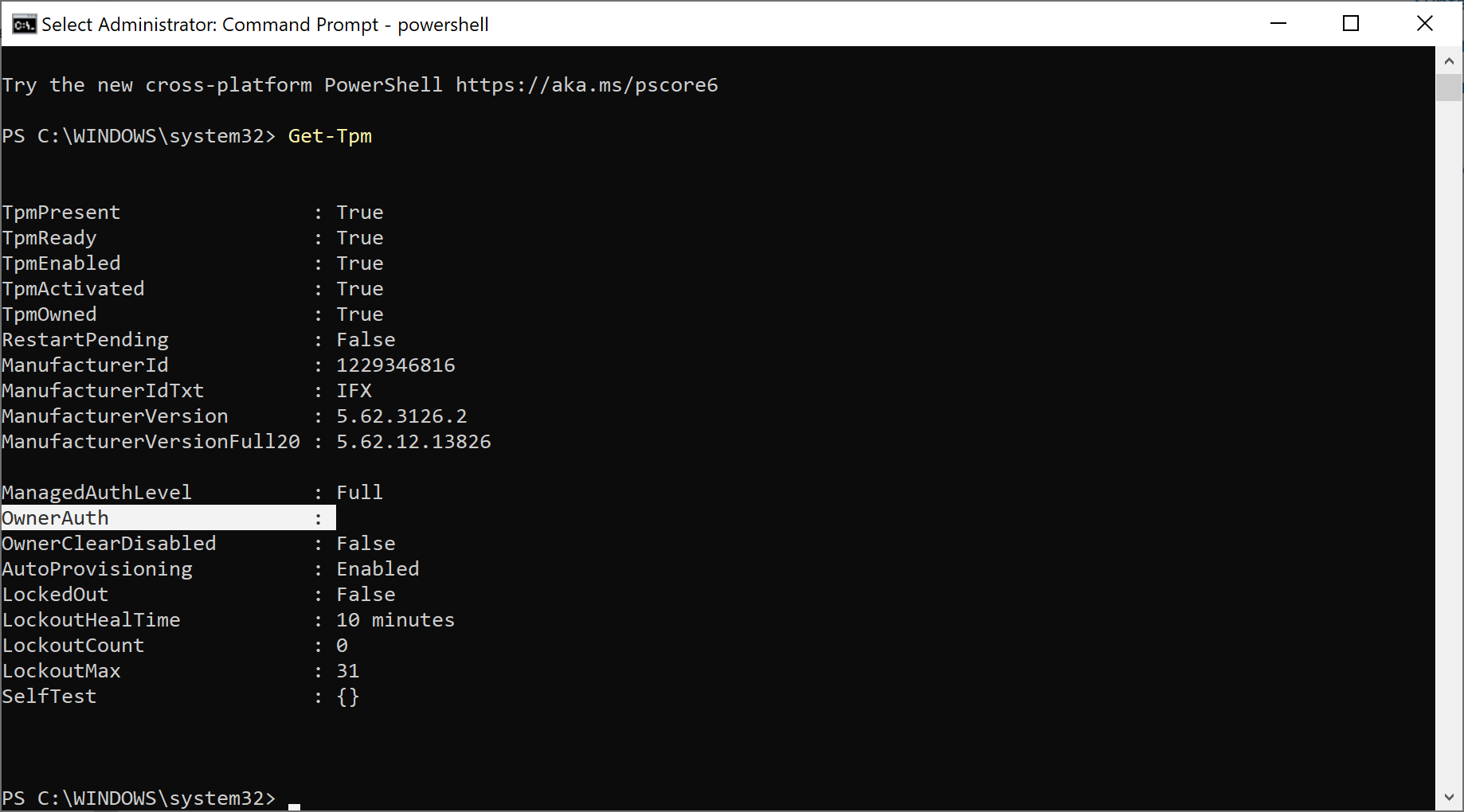
 Finally I checked in SQL for the TPM owner auth (or TPM password hash).
Finally I checked in SQL for the TPM owner auth (or TPM password hash).
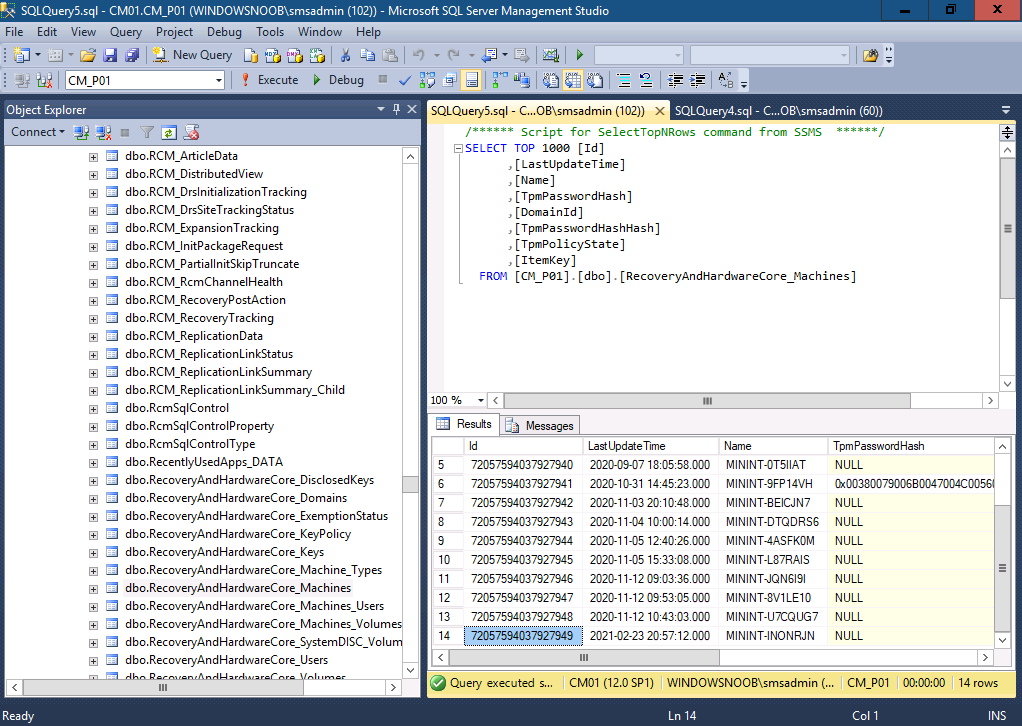 Which stated null, but checking on the client revealed that it wasn’t configured, so hopefully that’s correct in SQL.
Which stated null, but checking on the client revealed that it wasn’t configured, so hopefully that’s correct in SQL.
Nice work Microsoft !
cheers
niall



Niall, thanks for the article. I have been playing with MBAM after upgraded our MECM 20 10. I deployed a policy to encrypt the OS drive to my test collection. Everything works when the client is on the intranet. If the client is on internet, they still get the bitlocker policy and encryption works but the key escrow over CMG isnt working. The key is not escrowed back to MECM DB until i connect the machines to VPN. Did you see such behavior while testing this. My site is in HTTPS only mode. I looked at the CCM\BLM UseKeyRecoveryService registry value and it is already set to 1. I can also see the value for UseKeyRecoveryService in Policies\Microsoft\FVE\MDOPBitLockerManagement changing back and forth(1 on intranet and 0 on internet) while switching the client between intranet and internet.
bitlocker log shows the below error
Processing MP MYCMG FQDN.
Management point MYCMG FQDN did not meet one of the following criteria
Version (9040) greater than 8820: TRUE
MP type (Internet) is Assigned type: FALSE
Write access to SQL database: TRUE
Enumeration of MP endpoints did not find a single endpoint.
Unable to find suitable Recovery Service MP. Forcing policy non-compliant
Bitlocker Management rule BitLockerManagementSettings_BMSClientConfigureCheckIntervalPolicy is compliant
Processing BitLockerManagement Rule ‘BitLockerManagementSettings_BMSFDVEncryptionPolicy’. Enforcement is ON
let me know if you have seen this in your testing
hi, it worked fine for me, have you seen this > https://www.youtube.com/watch?v=wWJS4hj8iQE
I did. Since I already have my MECM on HTTPS, there is nothing special I have to do to get this working according to MS documentation. So I am not sure why the key escrow not working for me. The error I mentioned above is only error I can see on the client bitlocker logs. No errors on MBAM\Operational logs either
did you create the policy from scratch after upgrading to 2010 ? if not, try that
thanks Niall. I refreshed the policy after upgrading to 2010 as Microsoft asked. Also tried creating a new policy and both haven’t helped. The encryption is happening over the CMG (I believe that also didn’t work before 2010) but its just the key escrow part that is broken at the moment.
Did you find a solution to this? Running into the exact same issue. Key doesn’t escrow via the CMG.
Seeing the same error in logs:
MP type (Internet) is Assigned type: FALSE