Introduction
These are my notes from a session @ Microsoft Ignite 2020, the session was hosted by Steve Dispensa (Director of Program Management at Microsoft Endpoint Manager) and Ramya Chitrakar (Director of Engineering at Microsoft Endpoint Manager).
For the last couple of years at Ignite I blog my notes for sessions I’m interested in as I always find it nice to later refer to this reading material and punctuate it with content I’ve covered, and sometimes the videos just flow by too fast and you miss out on important points. Where appropriate I’ll link to content that I’ve covered that is referred to in the video.
This is part 2 of a two part series:
- What’s new in Microsoft Endpoint Manager – part 1
- What’s new in Microsoft Endpoint Manager – part 2 (this part)

As a reminder, Microsoft Endpoint Manager let’s you manage your entire endpoint estate whether cloud native or on premise. On your cloud management journey if you’ve just started out or you’ve deployed co-management or you are completely in the cloud Microsoft Endpoint Manager is truly your hub to unify security, apps, access,compliance and end user experience across your entire technology estate.

MEM delivers analytics and data to keep you ahead of change so you can keep your cost down, no matter what change brings.
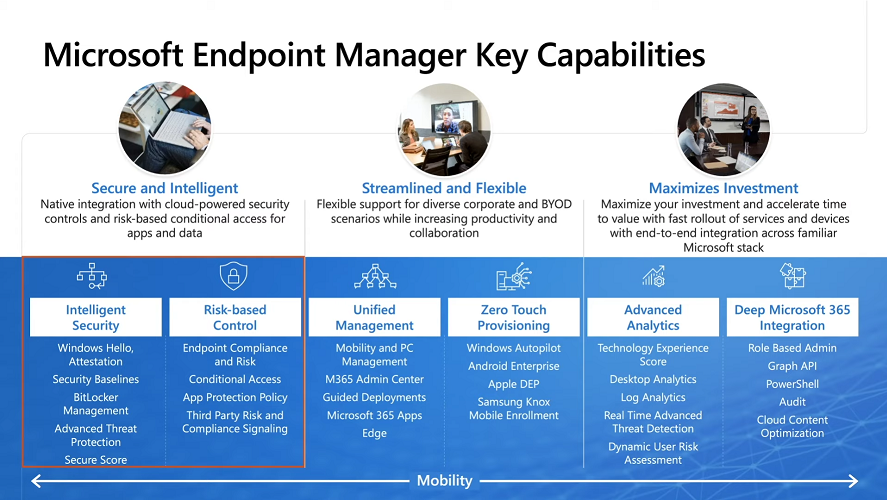
Focus on Security
With Covid, almost all businesses in the world are dealing with remote productivity, where users are working from home and other remote locations and that means it’s never been more important to ensure uniform security policy. MEM provides a rich portfolio of capabilities to assist you with keeping your organization safe and sound.
“Start with Security Baselines to ensure your organization is following best practices and to ensure you have uniform application policy across your organization.”
You can start with Security Baselines to ensure your organization is following best practices and to ensure you have uniform application policy across your organization. You can manage a host of security specific policies across devices including platform specific capabilities like encryption and firewall rules and advanced threat protection from Microsoft Defender ATP.
Then you can move on to risk-based access control where MEM can monitor the compliance of devices real time and that can be fed into Azure AD Conditional Access (powerful access control system). Additional you can deploy app control policies to provide compliance without fully managing a device, for example with BYOD devices.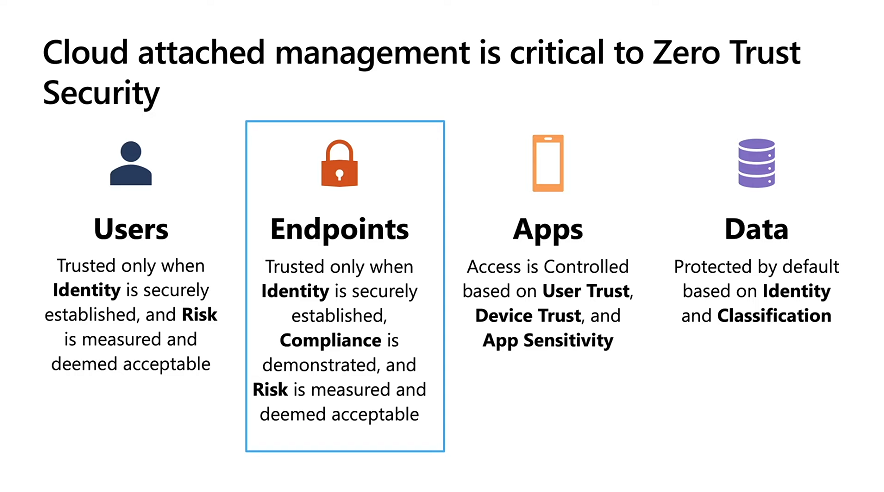
With users working from so many locations organizations need to deploy consistent policy either inside or outside corporate firewalls, is the foundation of Zero Trust. MEM can ensure that your Zero Trust policy is deployed to all your devices. Cyber threats and phising attacks are increasing between 3 and 5 times and in a recent survey 89% of businesses see cyber security as a top priority yet 62% say they lack the in-house skills to deal with it.
“In a recent survey 89% of businesses
see cyber security as a top priority
yet 62% say they lack
the in-house skills to deal with it.”
Read the rest of this blog post over at windows-noob.com