Introduction
I was busy putting together another BitLocker Management OSD related blog post in one of my PKI enabled ConfigMgr labs (#11) when I noticed that PXE boot no longer worked. The virtual machine would attempt to PXE boot for a while and then time out and boot straight into the operating system.
PXE boot worked just fine the day before and I was nearly done with my blog post, so what was the issue ?
A quick look at the smspxe.log file revealed some details within a sea of red.
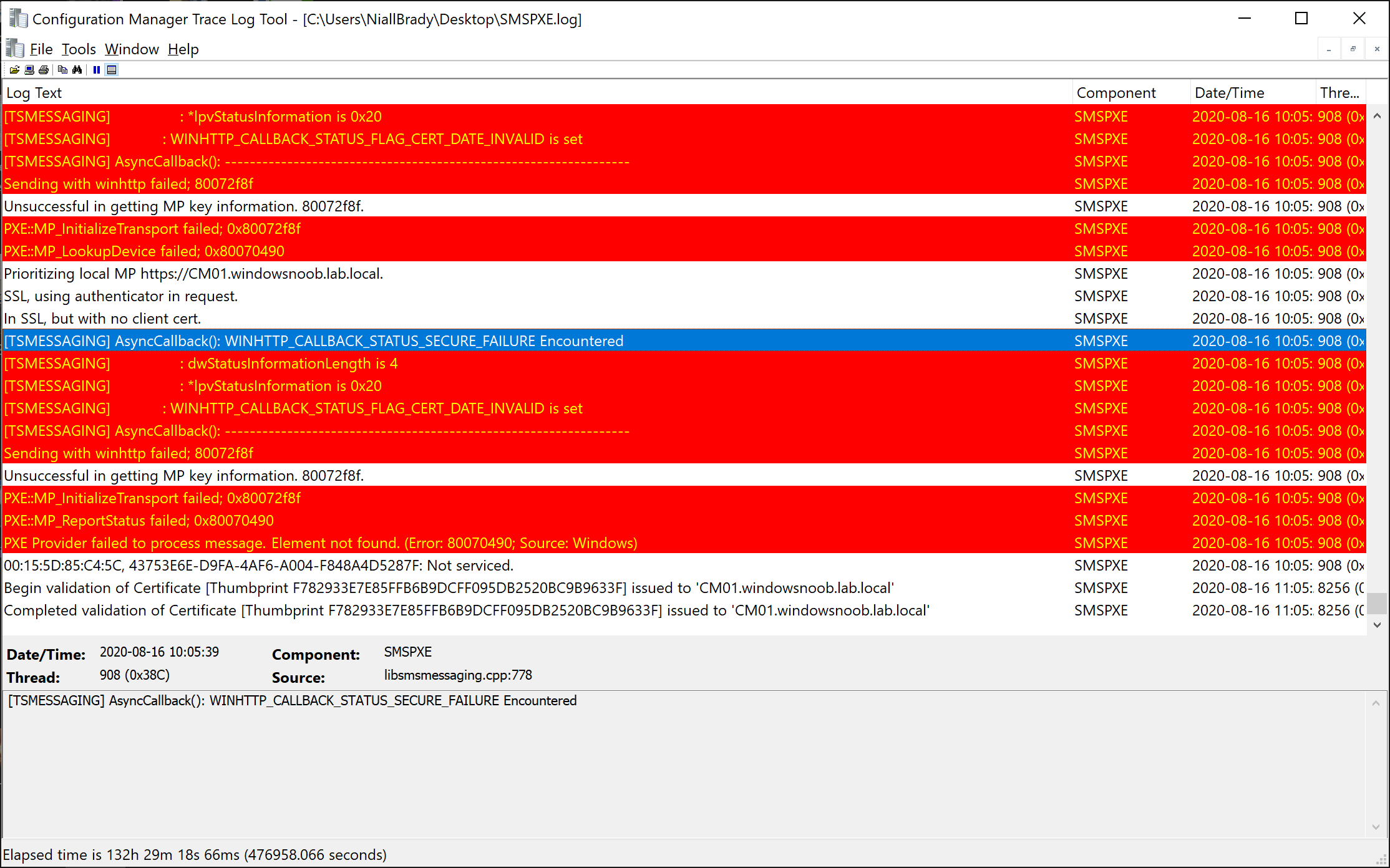 The most interesting line was this one, it’s referring to WINHTTP (that would be IIS) and CERT_DATE_INVALID !
The most interesting line was this one, it’s referring to WINHTTP (that would be IIS) and CERT_DATE_INVALID !
[TSMESSAGING] : WINHTTP_CALLBACK_STATUS_FLAG_CERT_DATE_INVALID is set
Digging deeper
So I guessed I had an expired certificate but a quick glance as pkiview.msc on the IssuingCA server, didn’t reveal any issues.
 Next, I checked certsrv.msc on the IssuingCA to list expired certificates, and I sorted by name so I could easily find my IIS certificate. According to this, it expired yesterday (today is 2020/8/16).
Next, I checked certsrv.msc on the IssuingCA to list expired certificates, and I sorted by name so I could easily find my IIS certificate. According to this, it expired yesterday (today is 2020/8/16).
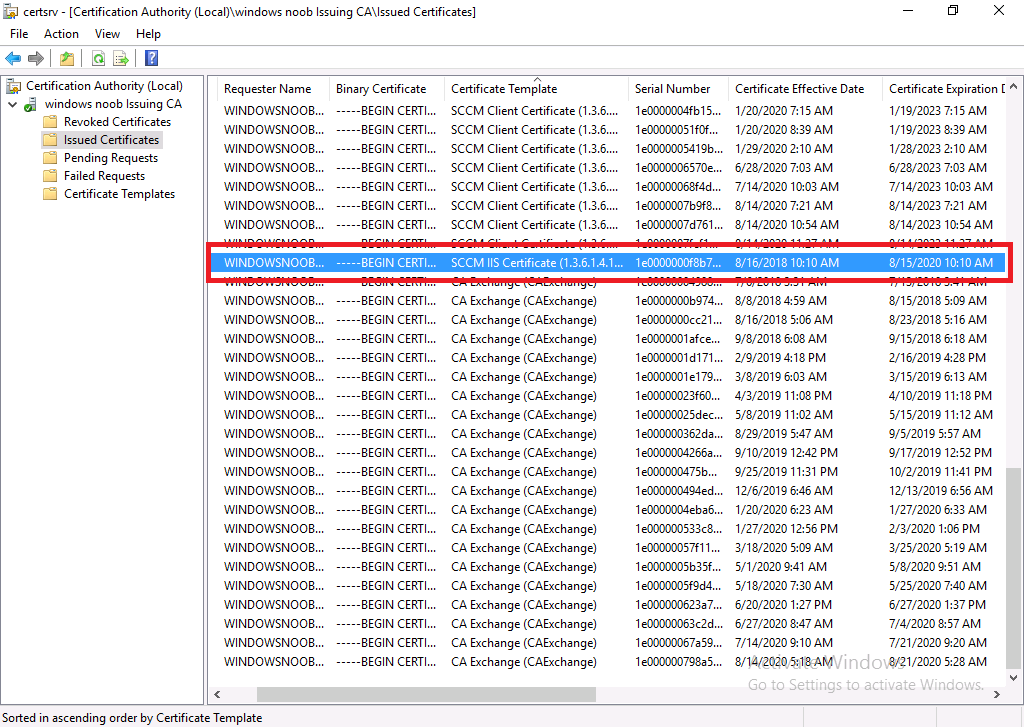 And there you have it, the SCCM IIS Certificate which I deployed 2 years ago, with a lifetime of 2 years is now expired.
And there you have it, the SCCM IIS Certificate which I deployed 2 years ago, with a lifetime of 2 years is now expired.
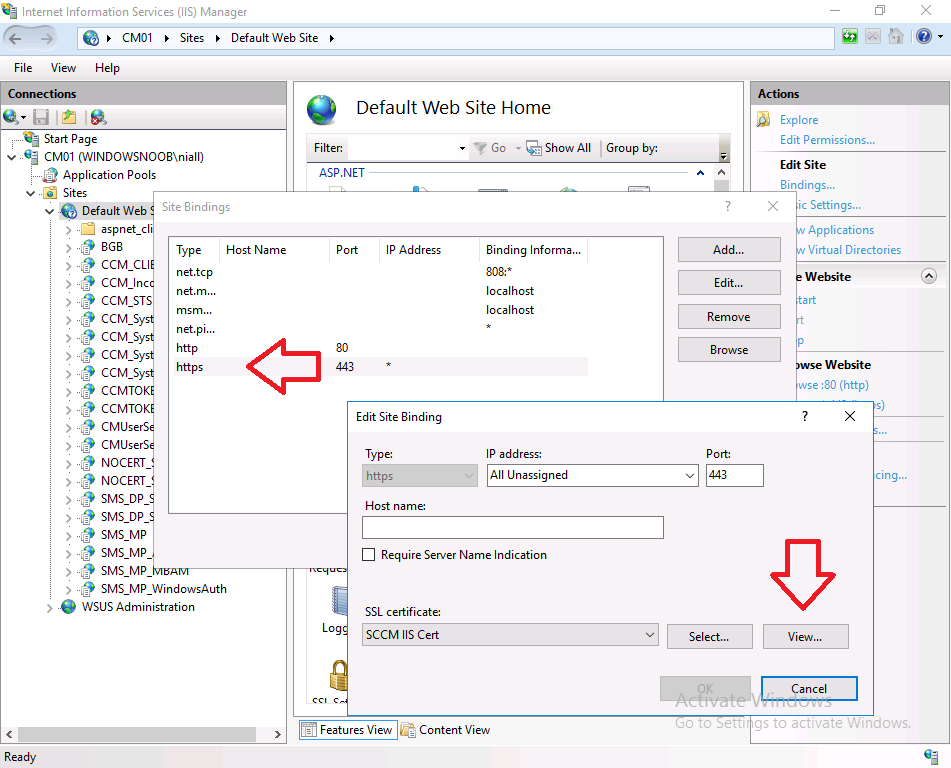
To confirm this, I launched Internet Information Services (IIS) Manager on the ConfigMgr primary server (CM01), and selected Default Web Site, then selected Bindings.
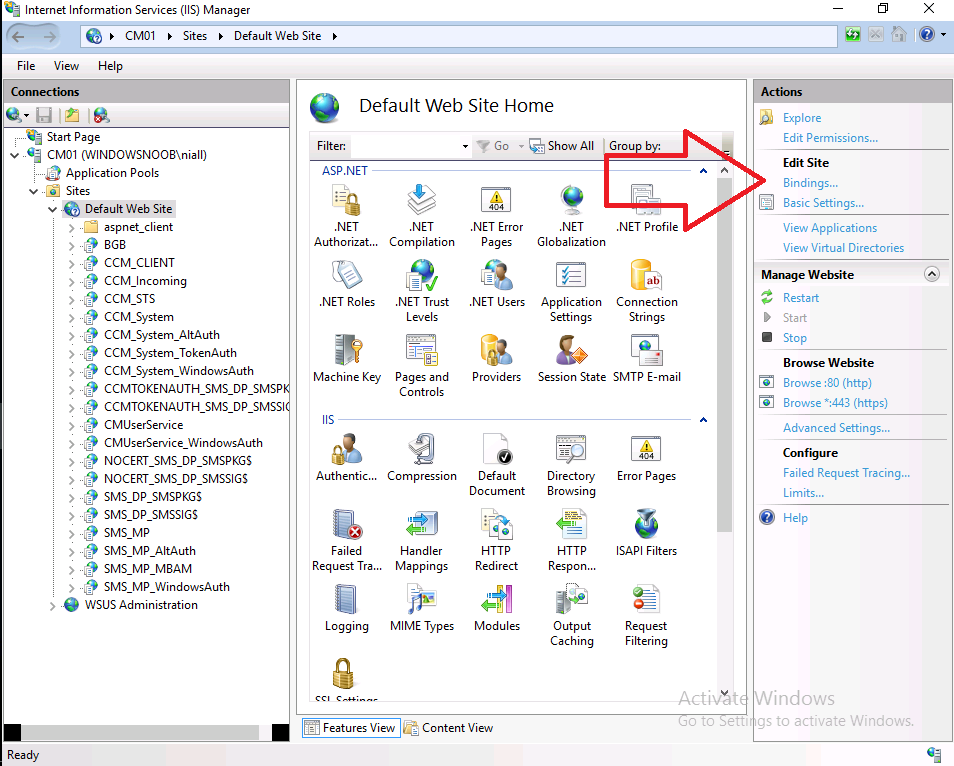 And then I clicked on https and then clicked on View.
And then I clicked on https and then clicked on View.
This certificate has expired or is not yet valid
It expired yesterday right in the middle of another blog post I was putting together, and that caused me to lose focus as I had to figure out this new issue, so one day led to another.. and inevitable delays.
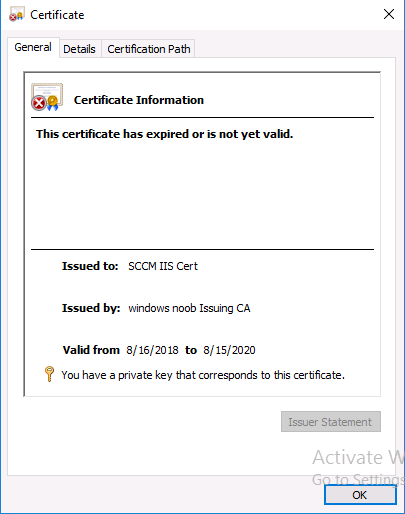 So now we know what the problem is, how do we fix it.
So now we know what the problem is, how do we fix it.
Requesting a new certificate
Note: This environment is one of my labs, so your setup will differ. Use these steps as a guide to fixing your broken production environment 😛
On the ConfigMgr primary server hosting IIS where you verified that the certificate had expired, start certlm.msc. We will use this to request a new certificate to replace the old expired certificate.
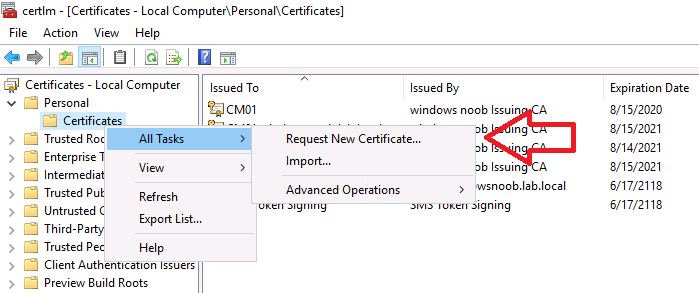
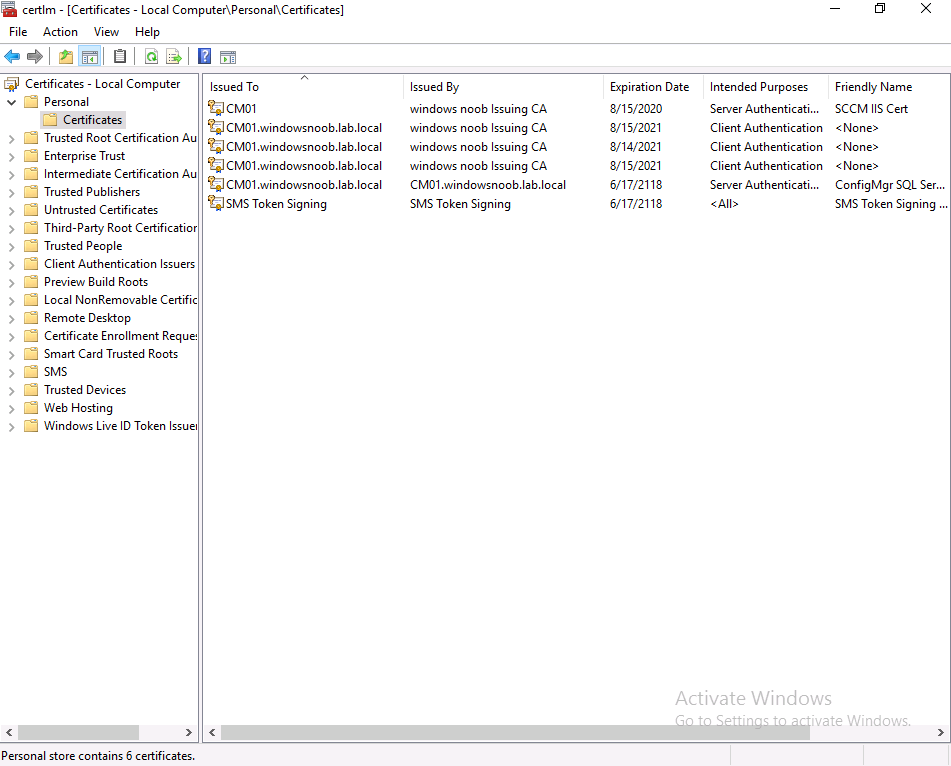 In Personal, Certificates, right click and choose All Tasks and then Request New Certificate.
In Personal, Certificates, right click and choose All Tasks and then Request New Certificate.
 Click Next at the Before you begin screen, and verify that Active Directory Enrollment Policy is selected before clicking Next.
Click Next at the Before you begin screen, and verify that Active Directory Enrollment Policy is selected before clicking Next.
Select the SCCM IIS Certificate from those listed.
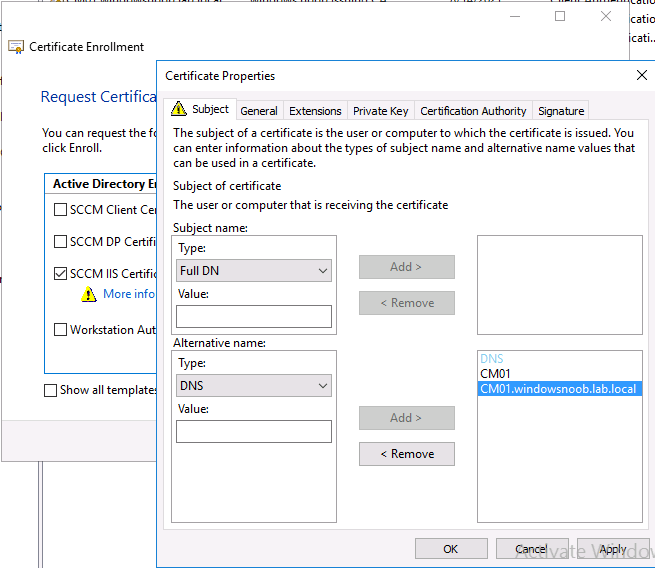
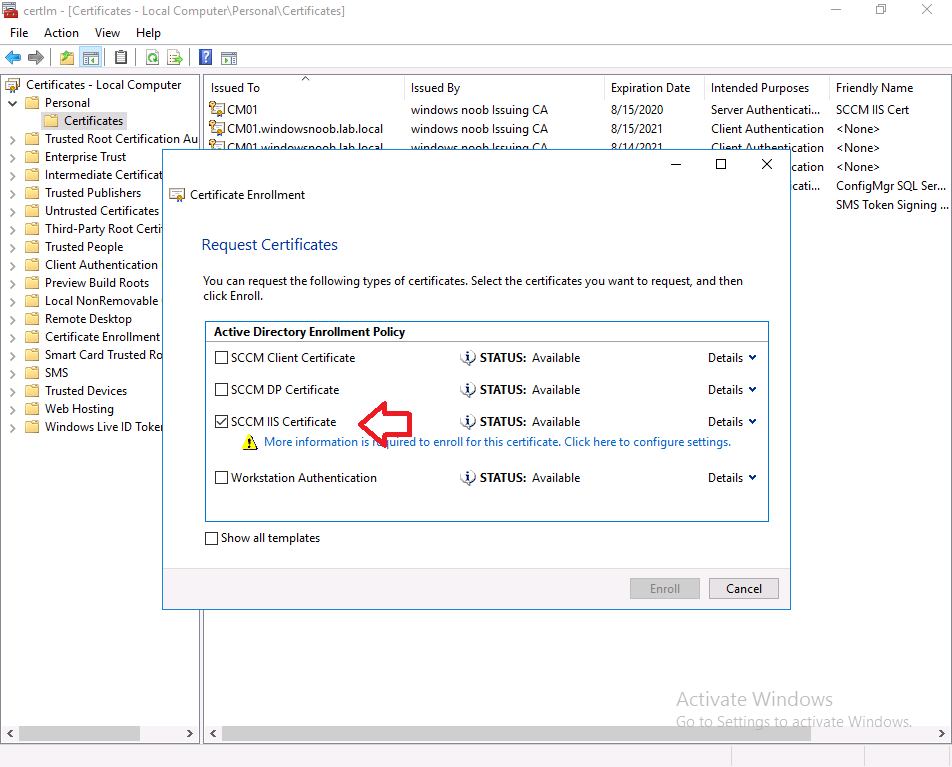 You’ll notice that for the SCCM IIS Certificate, more information is required to enroll, Click on the More information is required to enroll for this certificate message to enter this info.
You’ll notice that for the SCCM IIS Certificate, more information is required to enroll, Click on the More information is required to enroll for this certificate message to enter this info.
For Alternative Name, choose the DNS option and then click on Add to add both the hostname and the fully qualified domain name of your SCCM server (CM01 and CM01.windowsnoob.lab.local).
Next Click on General, and give this cert a friendly name so we can distinguish it in IIS later when we bind it.
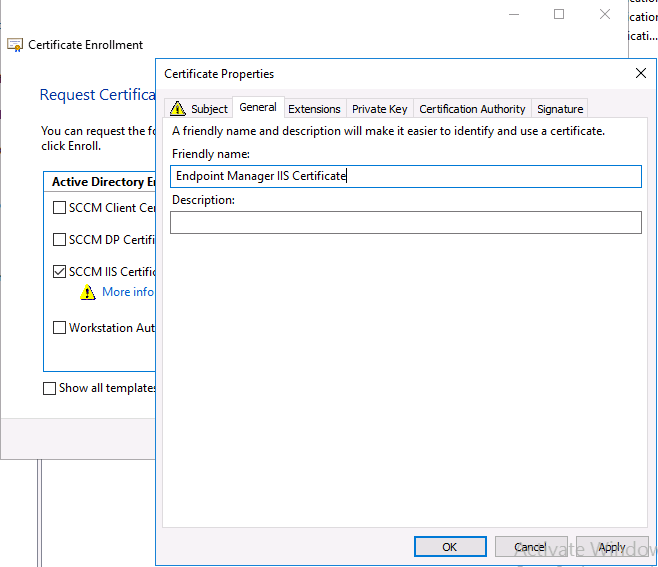 click OK, then click Enroll. Click Finish when done.
click OK, then click Enroll. Click Finish when done.
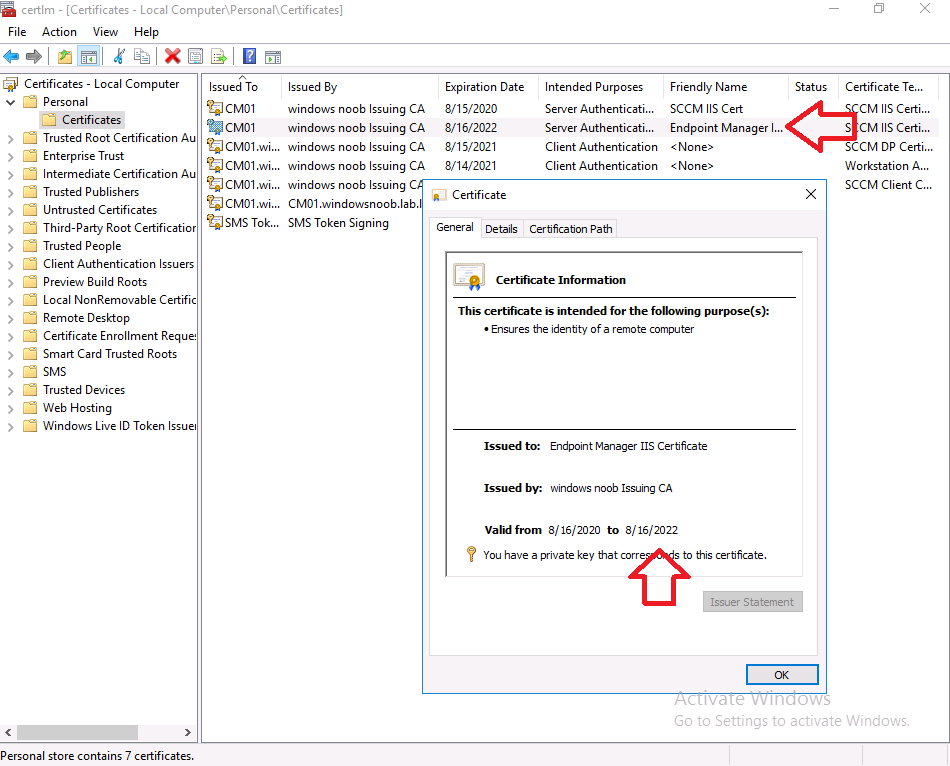
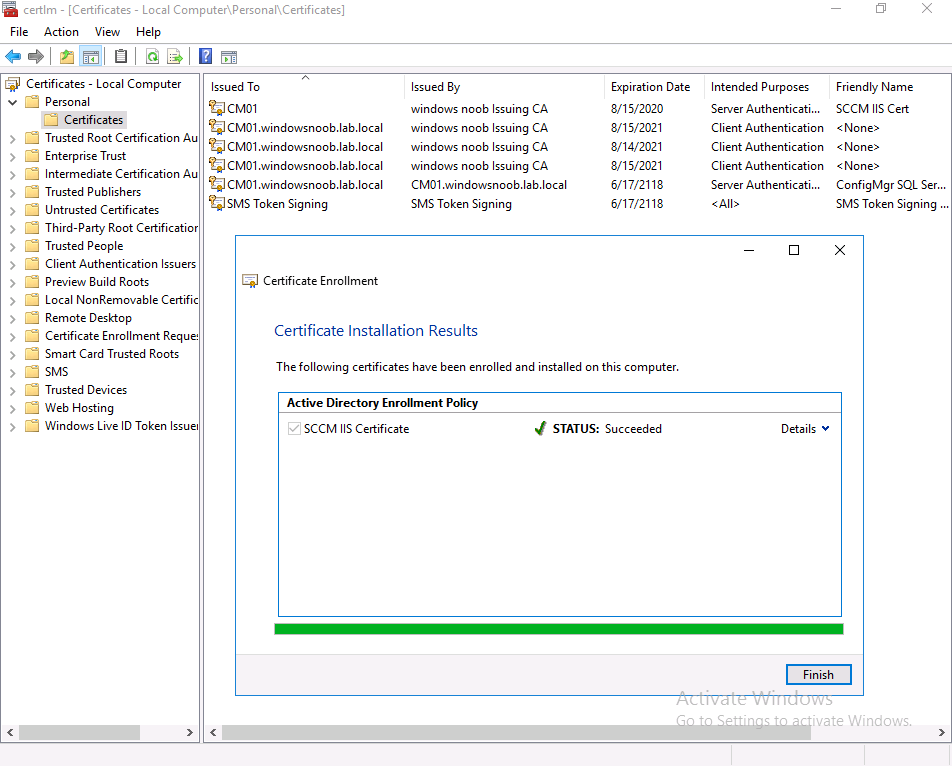 You can now see the new certificate listed, double click on it to bring up it’s details, as you can see it’s now got an additional 2 years before expiry and it has the new Friendly Name.
You can now see the new certificate listed, double click on it to bring up it’s details, as you can see it’s now got an additional 2 years before expiry and it has the new Friendly Name.
Import the new certificate into IIS
On the SCCM server (CM01), start Internet Information Services (IIS) Manager, expand Sites so that you can see the Default Web Site and the WSUS Administration websites listed. Select the Default Web Site, this web site is where the management point, distribution point and other SCCM roles such as Application Catalog can be found (if they are installed).
Right click on the Default Web Site and choose Edit Bindings from the options available. In the window that appears, select the https section (port 443) and choose Edit. In the screen that appears, change the dropdown for certificate from SCCM IIS Certificate (the expired one) to the newly released certificate called Endpoint Manager Certificate.
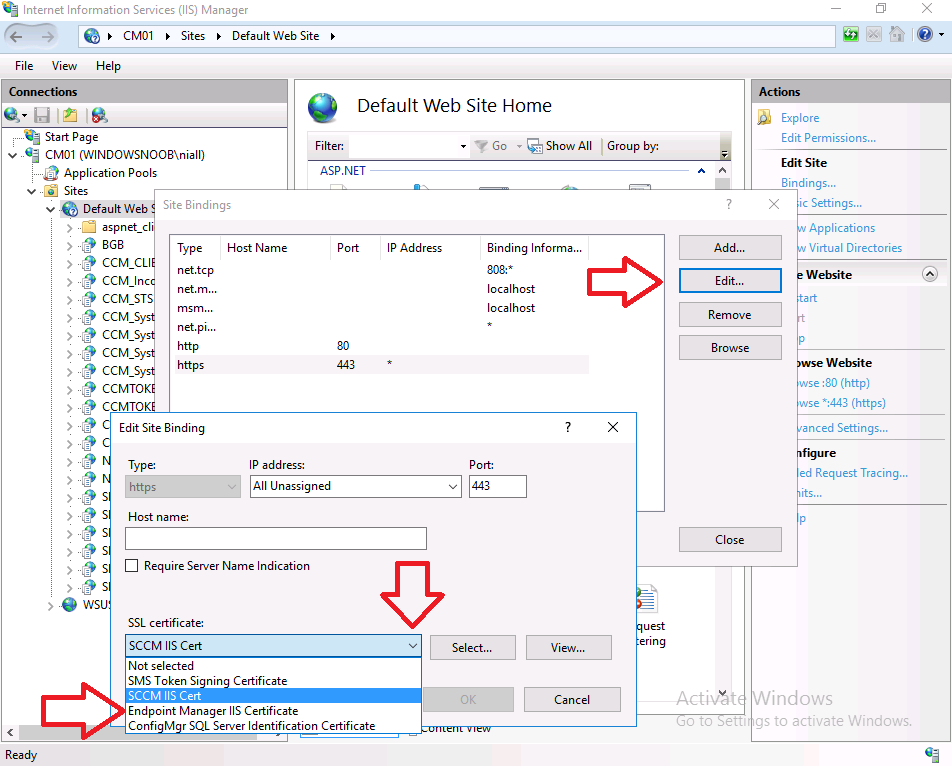 Click OK and then click Close.
Click OK and then click Close.
Note: If you are also hosting a Software Update Point (which uses WSUS) then you’ll need to do the same action for your WSUS https binding otherwise your software update point scans (on the client side) will fail with the following errors in WUAHANDLER.log
OnSearchComplete - Failed to end search job. Error = 0x80240438. Scan failed with error = 0x80240438.
Test the changes
Now that you’ve fixed the problem, PXE boot a computer again to verify the changes
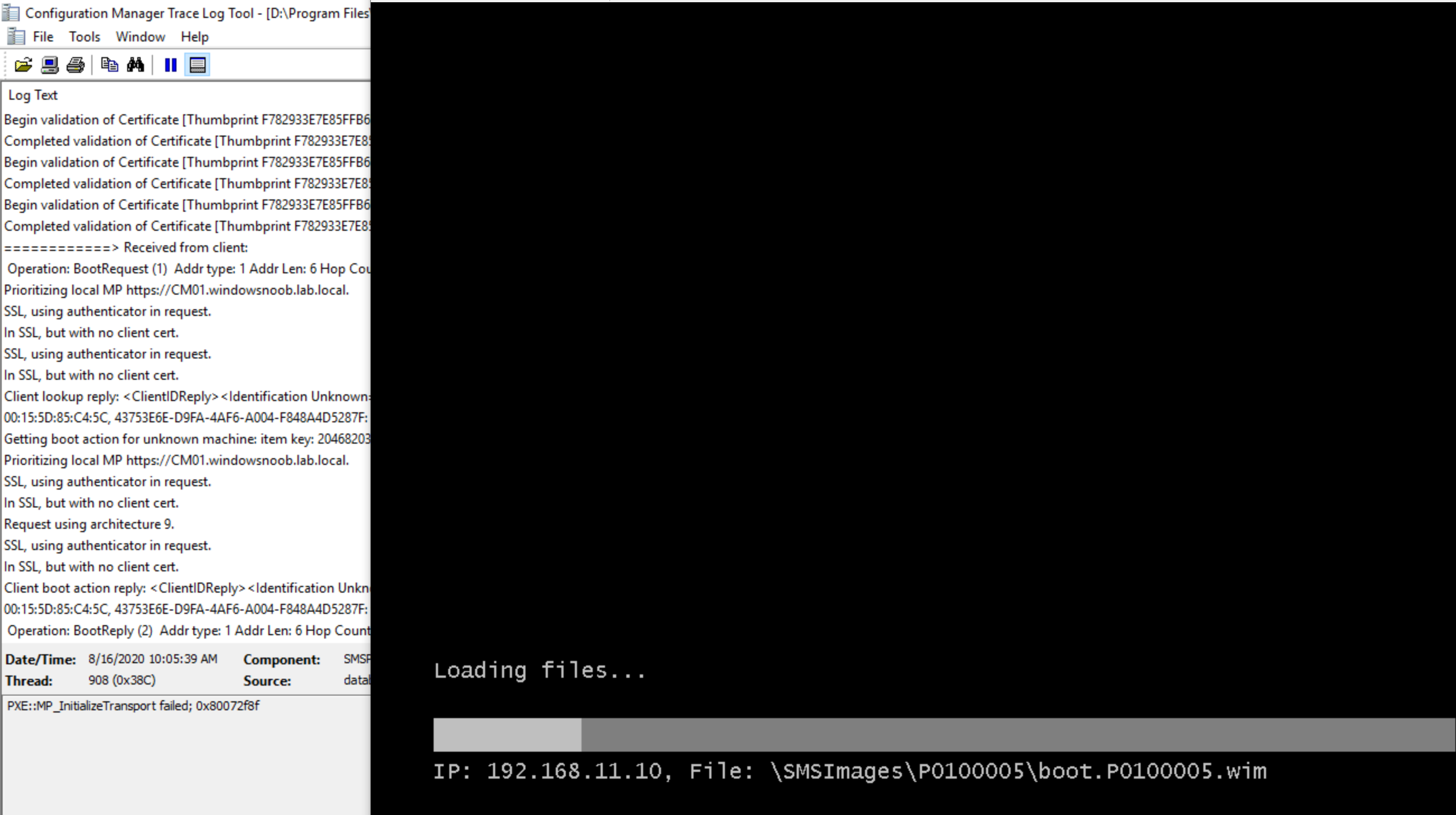 and as we can see, the SMSPXE.log is happy and PXE boot is working again, RESULT !
and as we can see, the SMSPXE.log is happy and PXE boot is working again, RESULT !



Pingback: Microsoft Cloud ve Datacenter Management Ağustos 2020 Bülten – Sertaç Topal
Thanks, this sorted the error for me. I could PXE boot but devices could not be joined to the domain or have any applications install. Renewing the certificate worked.
great to hear it!