Introduction
Microsoft Endpoint Configuration Manager 1910 came with BitLocker management capabilities (MBAM features), and this fits together nicely with task sequence steps regarding BitLocker.
The option to enable Full Disk Encryption actually started with Configuration Manager 1806 but MBAM integration (or BitLocker management) came with Configuration Manager 1910 and MBAM itself uses Full Disk Encryption, instead of the more commonly used Used Space Encryption found in typical task sequences.
By default, the Enable BitLocker task sequence step only encrypts used space on the drive. BitLocker management uses full disk encryption. Configure this task sequence step to enable the option to Use full disk encryption. For more information, see Task sequence steps – Enable BitLocker.
The Full Disk Encryption options can be found in two steps
- Pre-Provision BitLocker
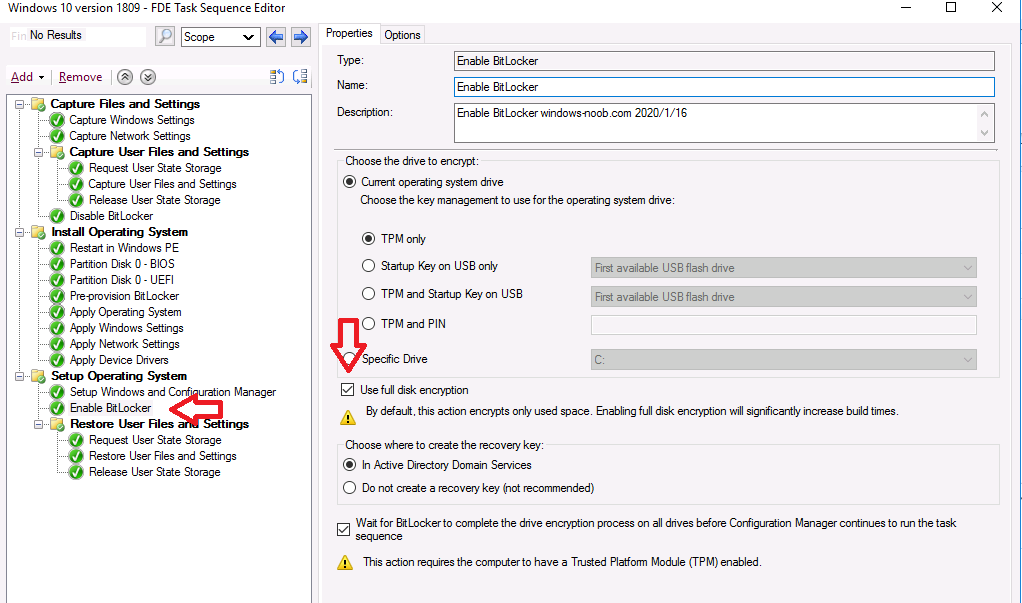
- Enable BitLocker
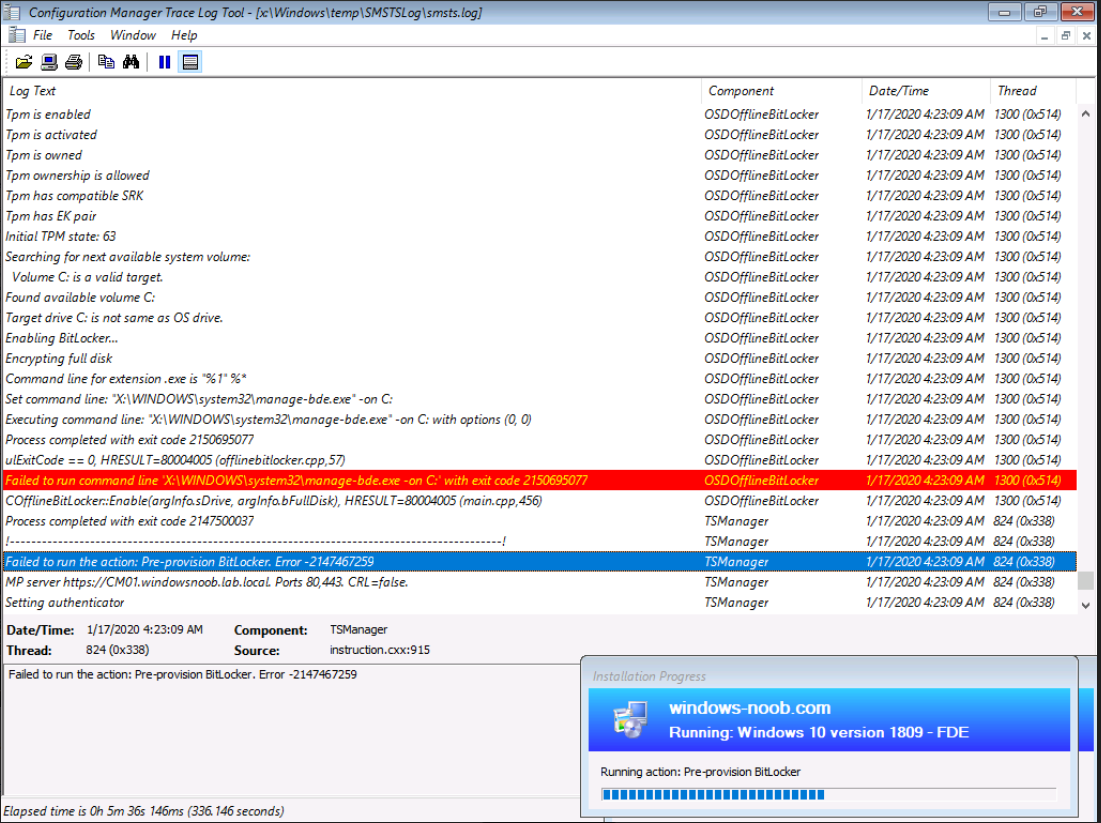
Note: The Full Disk Encryption method will not work on virtual machines with ADK 1709, and in particular will fail on the pre-provision Bitlocker step if you enable FDE on virtual machines. Below is how the failure will manifest itself.
Solution: Use ADK 1903.
Enabling FDE
To enable Full Disk Encryption in a task sequence using Configuration Manager 1910, right click on a task sequence and choose Edit. Locate the Pre-provision BitLocker step, and place a check mark in the Use full disk encryption check box.
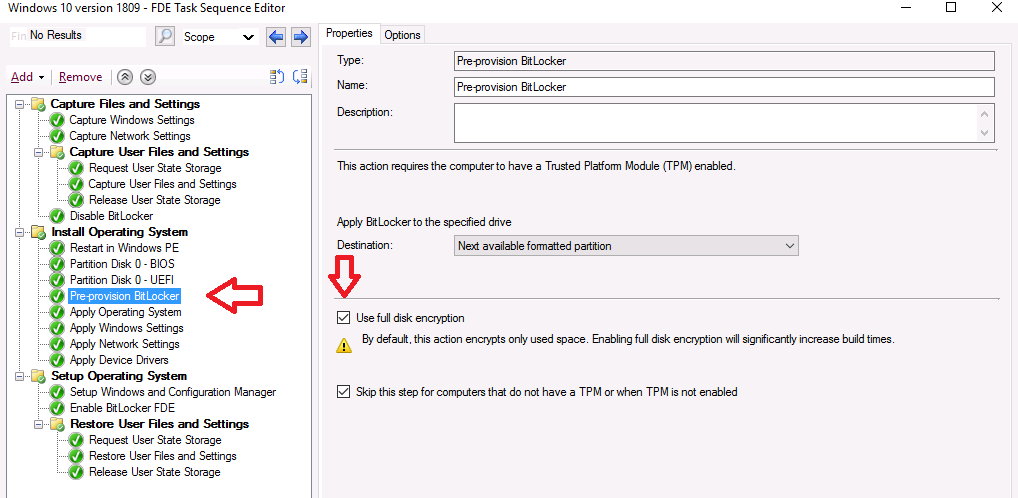 Once done, locate the Enable Bitlocker step and place a check in the Use full disk encryption check box. You can also optionally place a check mark in the Wait for Bitlocker to complete the drive encryption process before configuration manager continues to run the task sequence, however this will significantly add time to the deployment.
Once done, locate the Enable Bitlocker step and place a check in the Use full disk encryption check box. You can also optionally place a check mark in the Wait for Bitlocker to complete the drive encryption process before configuration manager continues to run the task sequence, however this will significantly add time to the deployment.
Once done, click on Apply and your changes are made. At this point you can kick off a new deployment using real hardware and you should see Full Disk Encryption taking place.
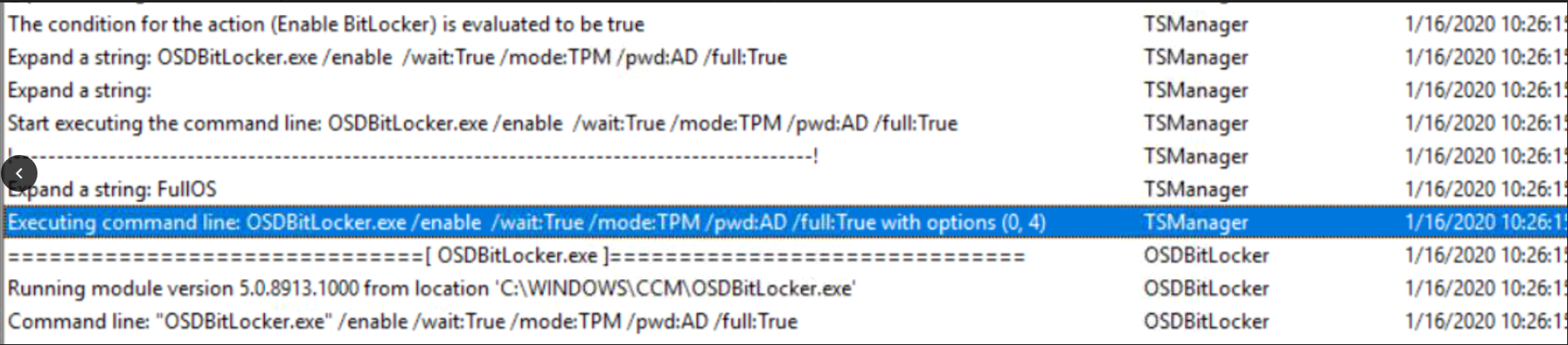
Below you can see the Enable Bitlocker step using the new switches via the smsts.log
OSDBitLocker.exe /enable /wait:True /mode: TPM /pwd:AD /full:True with options (0,4)
Note: I’m away from my ConfigMgr lab at the moment so cannot post logs proving that this actually succeeds on real hardware, but I will add that info next week once I can gain access to real hardware.
Update: Here’s the blog post on real hardware.
What’s missing from this ? well a few things, forcing the encryption algorithm and provisioning the key to MBAM integrated into ConfigMgr, i’ll cover those in a separate blog post.
Recommended reading
- Pre-provision Bitlocker https://docs.microsoft.com/en-us/configmgr/osd/understand/task-sequence-steps#BKMK_PreProvisionBitLocker
- Enable Bitlocker https://docs.microsoft.com/en-us/configmgr/osd/understand/task-sequence-steps#BKMK_EnableBitLocker
- Plan for Bitlocker Management https://docs.microsoft.com/en-us/configmgr/protect/plan-design/bitlocker-management



Great share, man…
Pingback: Want to learn about MBAM & the new Bitlocker Management feature in Microsoft Endpoint Manager Configuration Manager ? | just another windows noob ?
Niall, Thank you for the great blog and videos. After reading your blog about FDE in Task Sequence I am left wondering if the BitLocker Management in SCCM is ready for prime-time? Here are the challenges:
1. New machine builds – We can use FDE but cannot specify encryption strength or managing server. Also we have to still install MBAM Client. We would have to extend AD schema to store BL keys.
2. New machine builds – Would it be better to just re-use old methods of installing MBAM Client, Initialize TPM, and Invoke BitLocker encryption pointing to SCCM server instead of MBAM? Run Manage-BDE C: -On?
3. New machine builds – Would it be better to just place the machine into SCCM BitLocker Management collection at end of build? Why use Initialize and Enable built-in methods when they are not sufficient?
4. Existing Encrypted machines reporting to MBAM – Disable GPOs, place in SCCM collection to receive BitLocker Mgmt Policy and Config Baseline. Force gpupdate? Setting the OsEnforcePolicyPeriod and UsOsEnforcePolicy keys still does not force immediate encryption. If we ran as a phased migration we would need to be sure that machine is successfully managed by SCCM. Reporting is lackluster. How do we ensure? Checks of manage-bde and registry?
5. GPOs – Once fully migrated to SCCM for BitLocker Management we would need to create a new set of GPOs for any items not covered by BL policy.
Pingback: Full disk encryption – a closer look on real hardware | just another windows noob ?
Pingback: Bitlocker on Hyper-V Virtual Machine – GARYTOWN ConfigMgr Blog
Thank you for all you do Niall. I’ve used your videos for years. I have some questions now that MBAM is fully integrated into SCCM 2002. Are the task sequence steps to pre-provision and enable BitLocker still necessary or can I just place the newly imaged machines in the collection the MBAM policy is deployed to? I have followed your videos for MBAM setup in SCCM but I am not getting the encryption popup for the user on my test device. The MBAM client deployed fine and my portals are functional. Just no encryption popup. Thanks.
thanks for the thanks 🙂
as regards the MDOP Agent popping up, it will only do that if the computers are in the collection targeted with the BitLocker Management policy, and if they have a TPM and as long as you are not RDP’d to them. Also, they must have the matching version of the client, so are all of those things in place ?
Thanks for the response Niall. Yes the device is the only device in the collection targeted. It is a brand new HP ProBook 450 G6 and it does have TPM. I imaged it yesterday with Windows 10 1909 Ent then placed it in the collection. Ran machine policy to force it to go out and get the MDOP agent. The agent is installed. I waited for almost an hour and never got the pop up. I let it sit overnight and used SCCM to remote into the machine this morning but see no popup. Do I have to have the BitLocker settings in my imaging task sequences for this to work or should putting it in the targeted collection accomplish the same thing?
I guess I should clarify a bit more. I’m running SCCM 2002. My task sequence does not have pre-provision BitLocker or Enable BitLocker as part of the task. I haven’t found anywhere that says they need to be for MBAM to manage BitLocker in 2002. My understanding is that if they are in the task sequence the Recovery Keys end up in AD and not MBAM. Am I misunderstanding what is going on there? If they need to be in the task sequence that should be fairly painless.
Ok let’s take this one step at a time, what do you actually want to happen here, do you want Full Disk Encryption, or do you want to enforce encryption of USED space only using BitLocker Management ?
secondly, do you want the devices encrypted during the task sequence or after, which is your goal ?
let’s start by clarifying both of those things
cheers
niall
Great questions. Used space only makes the most sense to me. New machines obviously used space but I have a lot of users whose device is also going to need to be encrypted and sometimes those machines change hands. I would prefer they get encrypted after the task sequence since we are looking at using a 3rd party company to start doing our imaging prior to shipping but would be doing all in house re-imaging when necessary. I’d rather have the machine start to encrypt once it is on the user’s desk and placed in the MBAM policy targeted collection. In your experience what do you recommend for new machines vs devices that are currently in use? Thanks Niall.
I recommend Used Space Only unless you have a security requirement for FDE. FDE does mean that the task sequence will be slower as it has to wait until the disk is fully encrypted before finishing.